Tprc Ransomware is a type of malicious software that belongs to the Djvu ransomware family. Its primary function is to encrypt files on a victim’s computer, making them inaccessible until a ransom is paid.
Infection Methods:
Tprc ransomware typically infects computers through spam email attachments, dubious software downloads, or malicious advertisements. Users often inadvertently download and install the ransomware by opening an infected file or clicking on a suspicious link.
File Extensions:
Once in the system, Tprc ransomware scans for files to encrypt and appends a specific extension to the affected files. The extension is typically “.tprc”.
File Encryption:
Tprc Ransomware uses asymmetric encryption, typically RSA or AES, to lock the victims’ files. Asymmetric encryption involves a pair of keys – a public key to encrypt the files and a private key to decrypt them. The private key is held by the attacker, who demands a ransom in exchange for it.
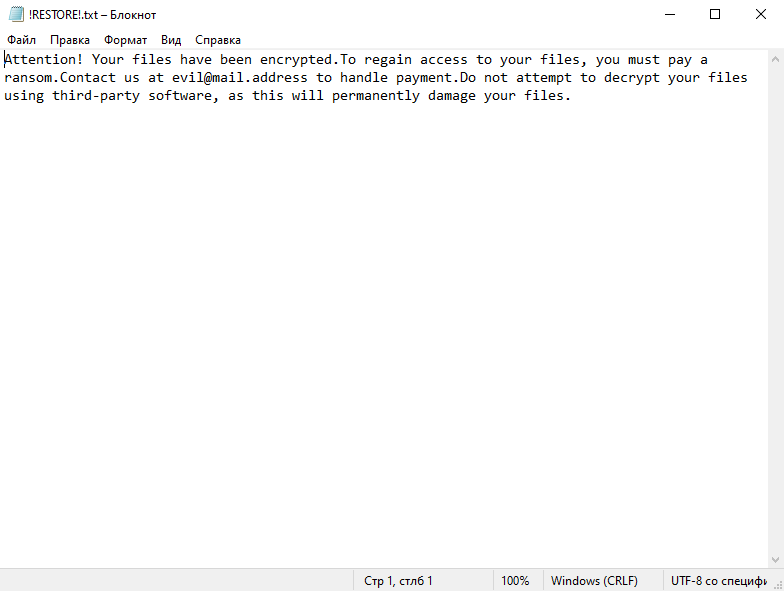
Ransom Note:
After encrypting the files, Tprc Ransomware generates a ransom note, usually in a text file. The note typically includes information about the encryption and instructions on how to pay the ransom to retrieve the decryption key. This note is usually placed in every folder containing the encrypted files, often named “_readme.txt”.
Decryption Tools:
It’s important to note that paying the ransom does not guarantee that the files will be decrypted. In fact, it only encourages the criminals to continue their illicit activities. Instead, victims should seek professional help to remove the ransomware and restore their files. However, as of now, there are no specific decryption tools available for Tprc Ransomware.
Decryption of %EXTENSION% Files:
Decryption of files encrypted by Tprc Ransomware is challenging without the private key. However, victims can try to recover their files through other means such as backup copies, shadow volume copies, or file recovery tools. In some cases, cybersecurity firms or law enforcement agencies may be able to assist with decryption. It’s always advisable to maintain regular backups of important files and keep your system and antivirus software up-to-date to prevent such infections.