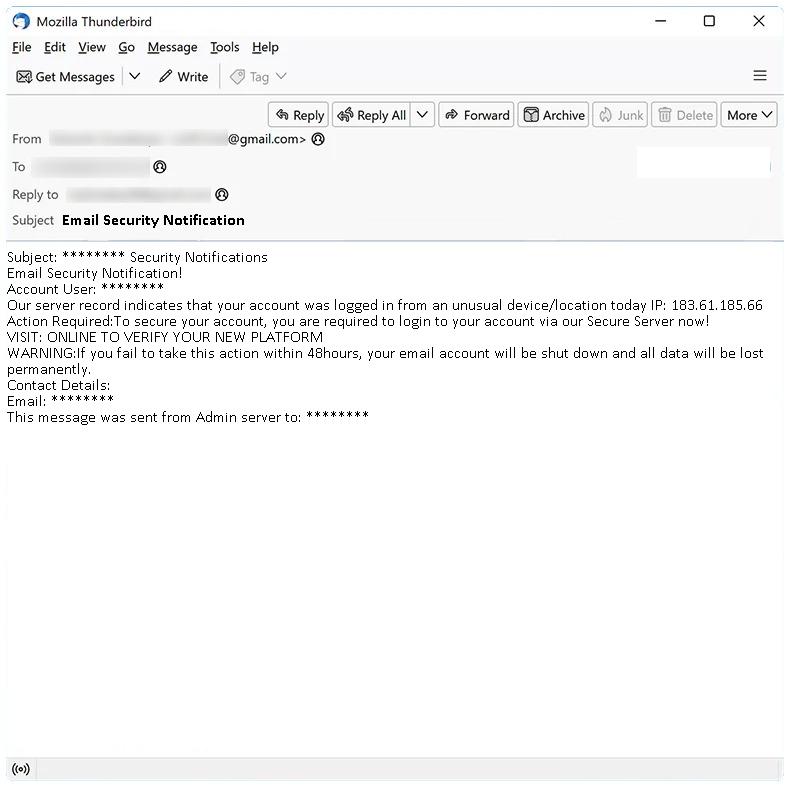
Email Security Notification email spam refers to a type of phishing scam where cybercriminals send deceptive emails pretending to be from a legitimate email security service or provider. These emails typically notify the recipient about a supposed security breach, compromised account, or suspicious activity in their email account. The purpose of these scams is to trick users into divulging their login credentials, personal information, or install malware onto their computers.
Email Security Notification spam campaigns often employ various techniques to infect computers:
1. Phishing links: The email may contain a link that directs the user to a fake login page designed to steal their email credentials.
2. Malicious attachments: The email might include an attachment that, when opened, installs malware or ransomware onto the victim’s computer.
3. Social engineering: The email may employ psychological manipulation, urgency, or fear tactics to trick users into taking immediate action without thoroughly verifying the legitimacy of the email.
Interacting with Email Security Notification email scams can pose several risks:
1. Account compromise: If users fall for these scams and provide their login credentials, the attackers gain unauthorized access to their email accounts, potentially leading to identity theft, financial fraud, or unauthorized access to sensitive information.
2. Malware installation: Clicking on links or opening attachments in these emails can result in the installation of malware or ransomware, which can compromise the security and functionality of the victim’s computer.
3. Data loss: In some cases, scammers may trick users into providing personal information, such as social security numbers or credit card details, leading to potential financial loss or identity theft.
4. Further phishing attacks: If scammers gain access to an email account, they can use it to send more phishing emails to the victim’s contacts, spreading the scam further.
It is crucial to be cautious when encountering such emails and avoid interacting with them. Instead, users should independently verify the legitimacy of the email by contacting their email service provider directly or accessing their accounts through official websites or applications.