How to remove MP3 Cutter Joiner Free
MP3 Cutter Joiner Free is a software program that allows users to easily cut and join MP3 audio files. This tool is especially useful for those who want to create custom ringtones, mix songs, or edit audio tracks for various purposes. With its user-friendly interface and simple features, MP3 Cutter Joiner Free has become a popular choice among music enthusiasts and professionals alike.
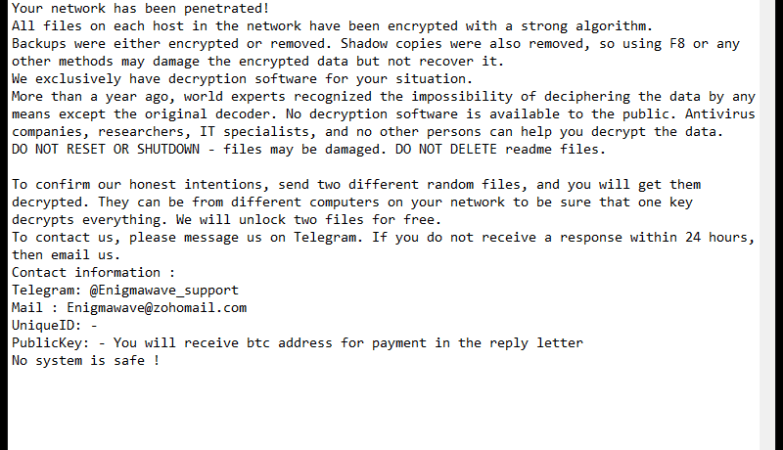
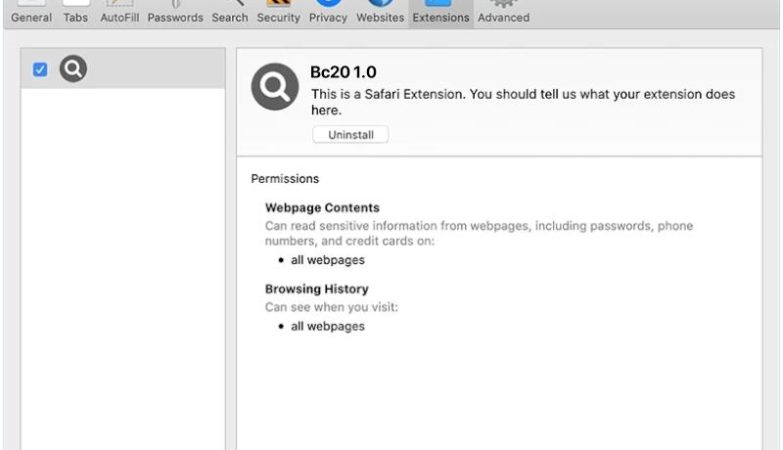
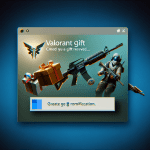
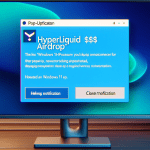
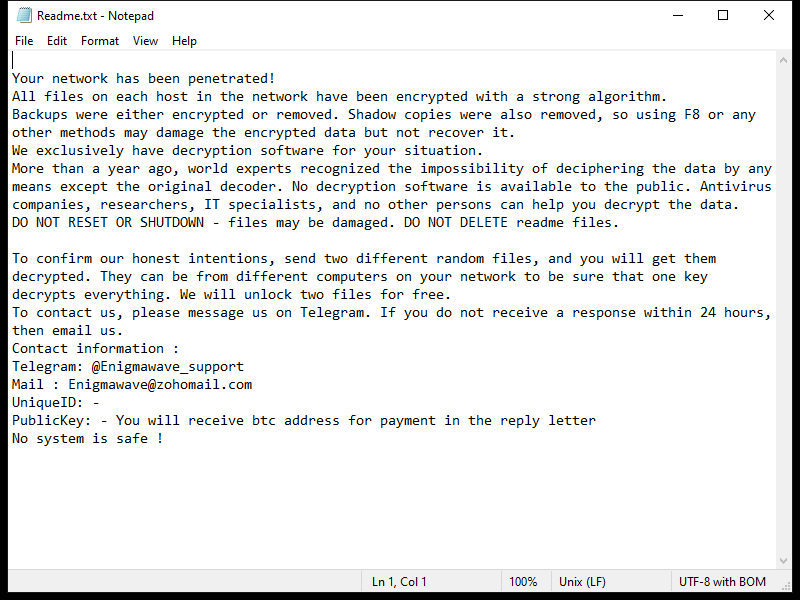
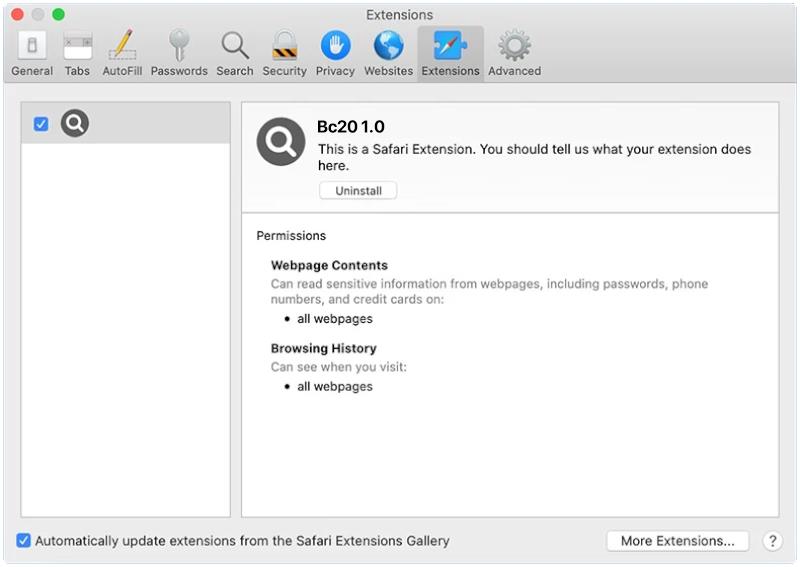
However, it is important to note that MP3 Cutter Joiner Free can also pose a threat to computer security. Like many other free software programs, this tool may come bundled with adware, spyware, or other potentially harmful software components. These malicious programs can infect a user’s computer, causing performance issues, privacy breaches, and even data loss. To avoid such risks, it is advisable to download MP3 Cutter Joiner Free from reputable sources and be cautious when installing any software on your computer.