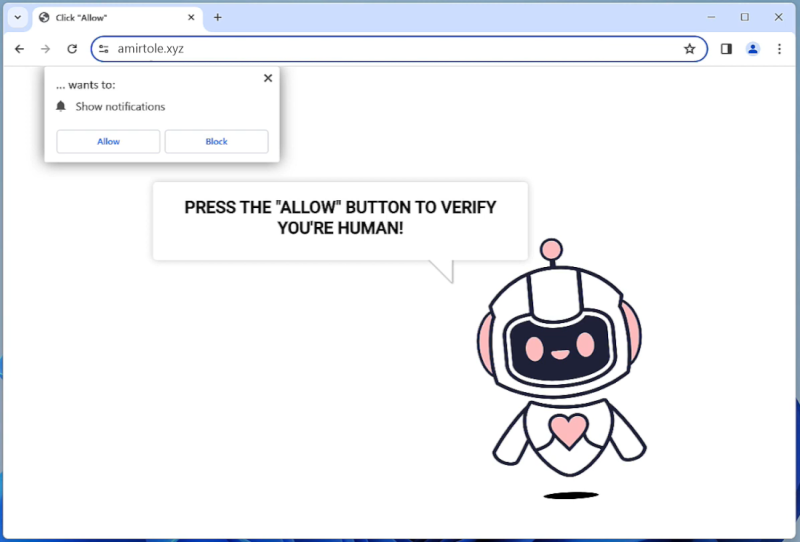
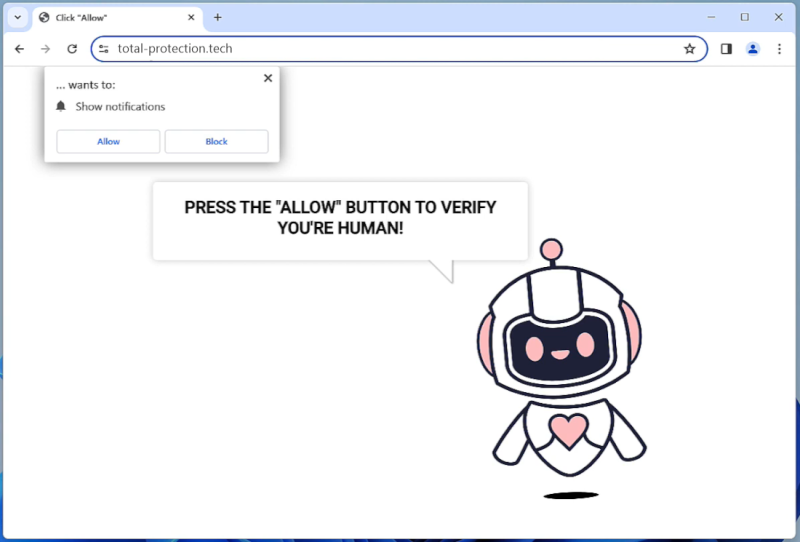
Amirtole.xyz is a malicious website that infects computers through deceptive tactics such as social engineering and fake alerts. When users visit the website, they may be prompted to allow browser notifications in order to access content or continue browsing. Once users grant permission, Amirtole.xyz can exploit these notifications to bombard them with unwanted advertisements, pop-ups, and potentially harmful content.
This website can infect a wide range of browsers including Google Chrome, Mozilla Firefox, and Safari, as well as various devices such as desktops, laptops, and mobile phones. By tricking users into enabling browser notifications, Amirtole.xyz gains the ability to push intrusive and malicious content to their devices, ultimately leading to a compromised browsing experience and potential security risks. It is important for users to be cautious when encountering suspicious websites and to avoid granting unnecessary permissions to prevent falling victim to such threats.