How to remove Universal Browser
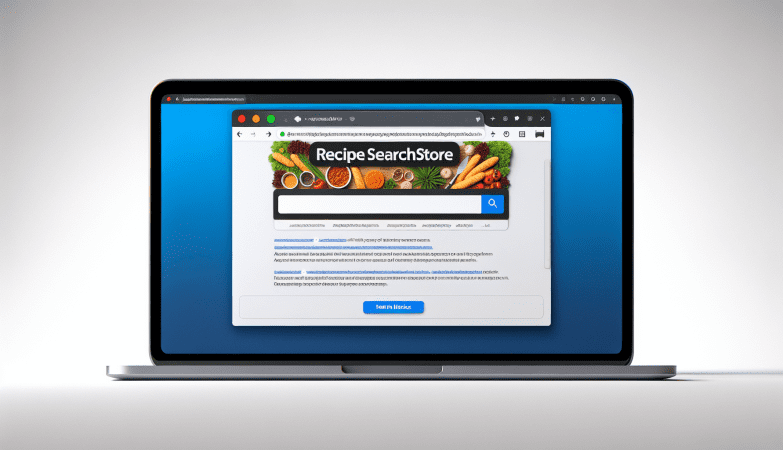
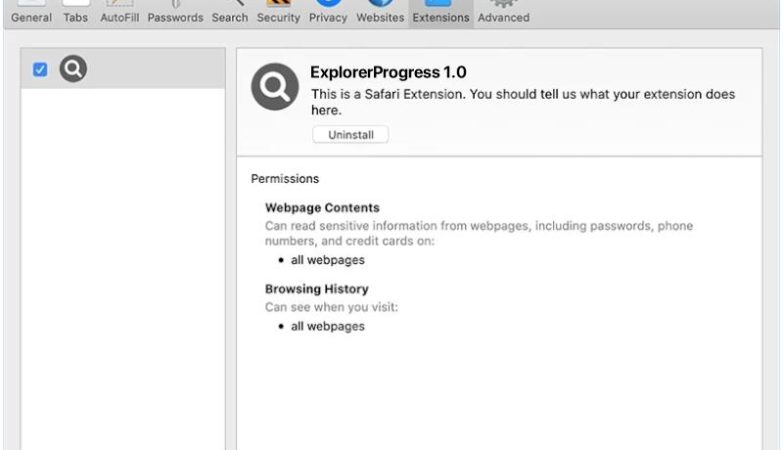
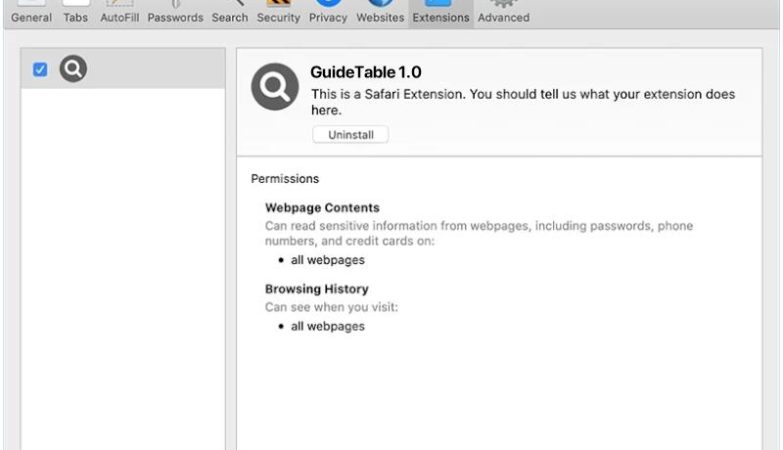
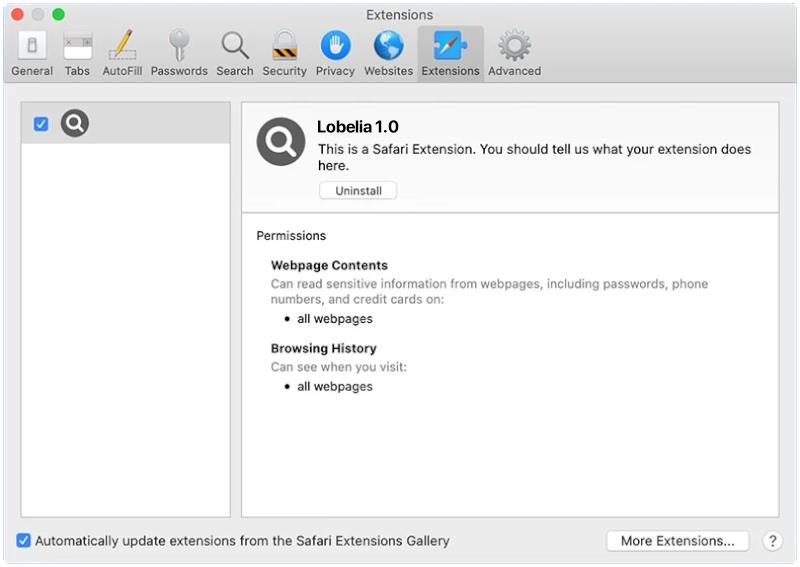
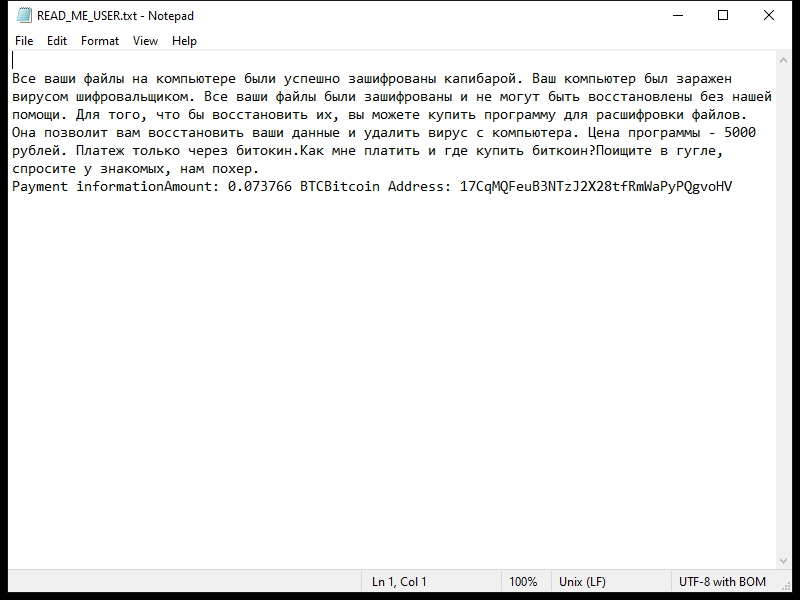
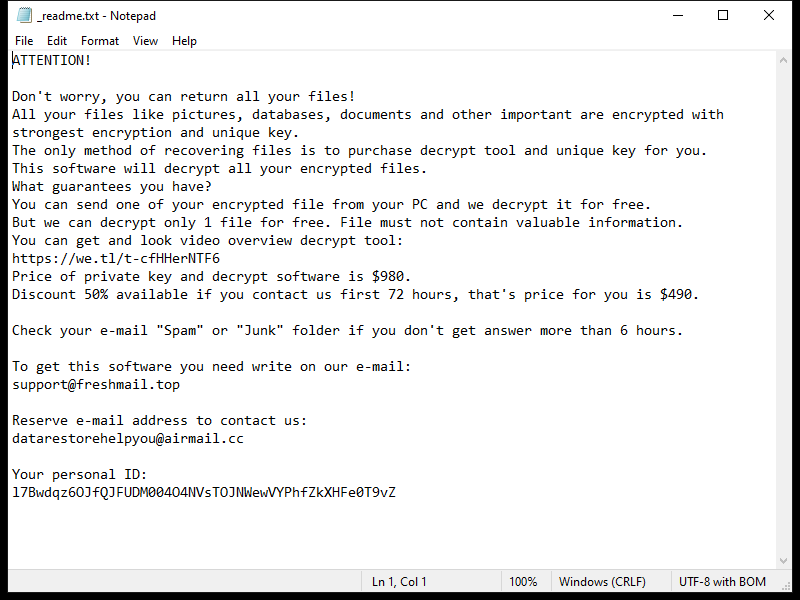
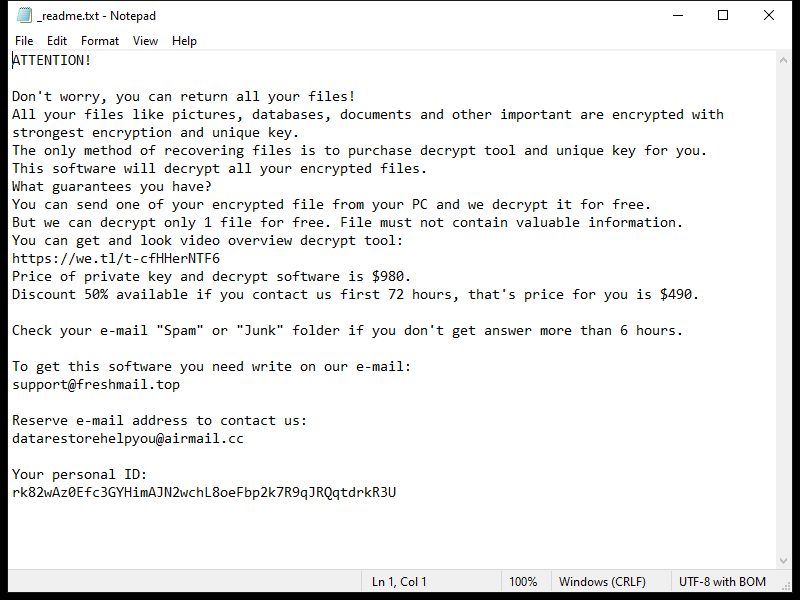
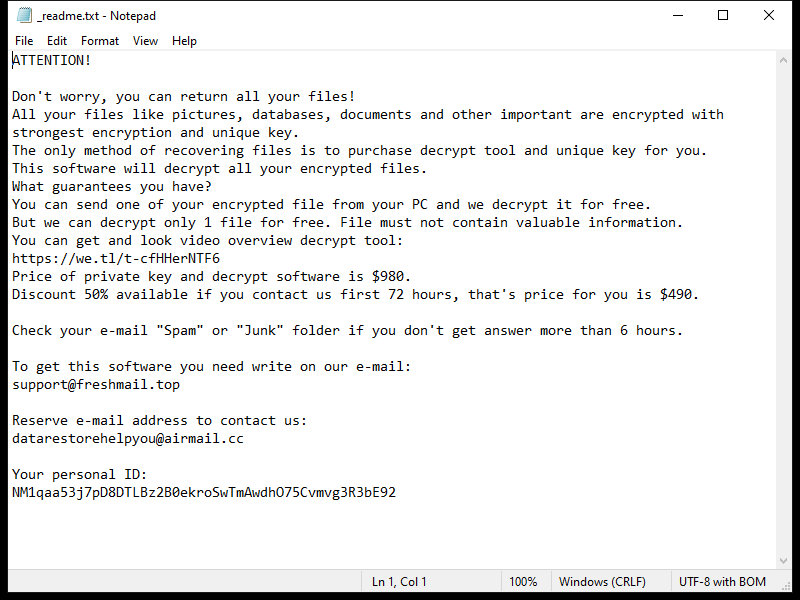
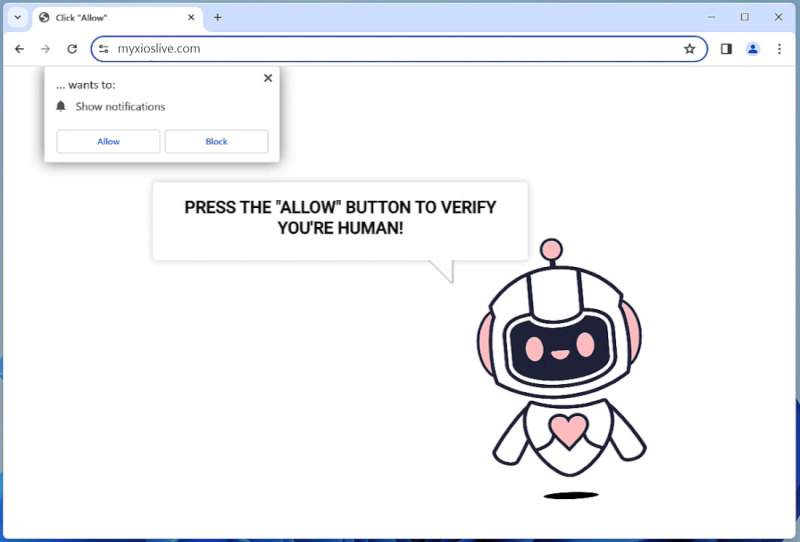
A Universal Browser is a type of malicious software that infects computers and hijacks web browsers. Once installed, it can change browser settings, track user activity, display unwanted advertisements, and redirect web searches to malicious websites. Universal Browser infections can occur through various means, including downloading infected files or software, clicking on malicious links or ads, or visiting compromised websites.
One common way that Universal Browser infects computers is through software bundling. This occurs when the malware is bundled with legitimate software downloads, such as free games or programs, and installed without the user’s knowledge. Once installed, the Universal Browser can take over the user’s browser, redirecting searches and displaying unwanted pop-up ads. It can also collect sensitive information, such as login credentials and financial data, putting users at risk of identity theft and fraud. It is important for users to be cautious when downloading software and to regularly update their antivirus software to protect against Universal Browser infections.