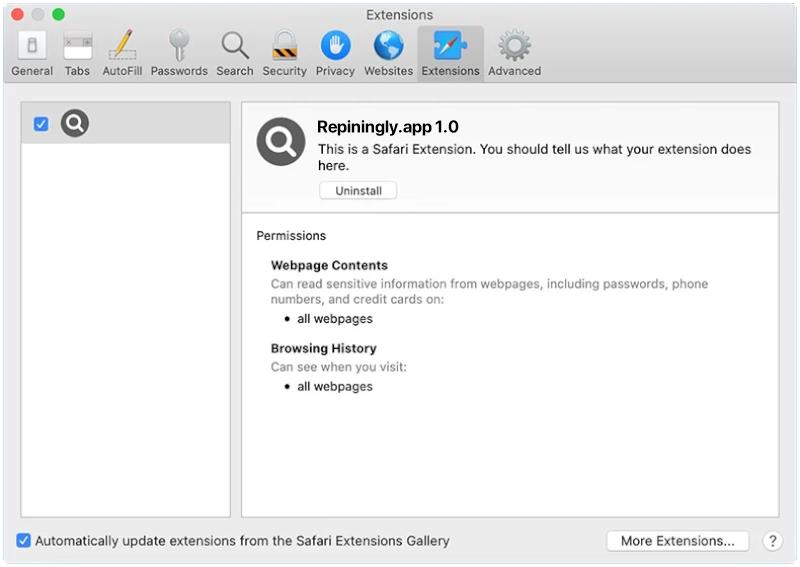
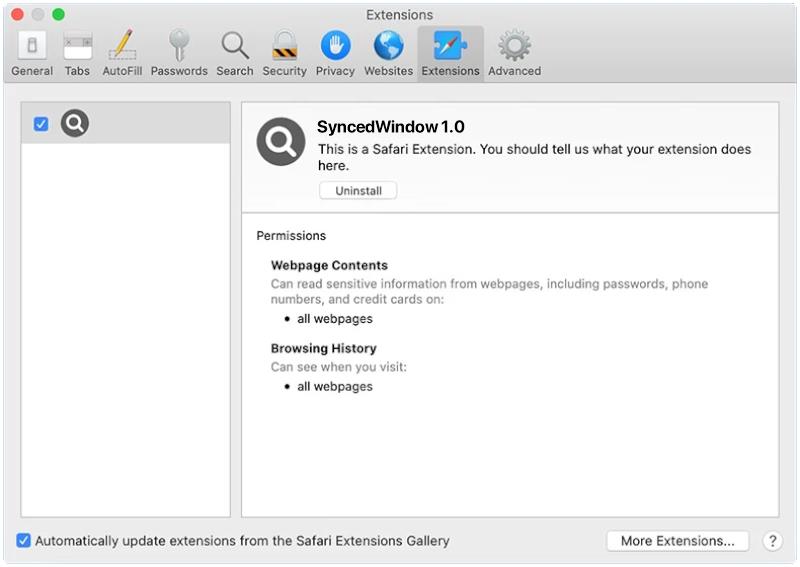
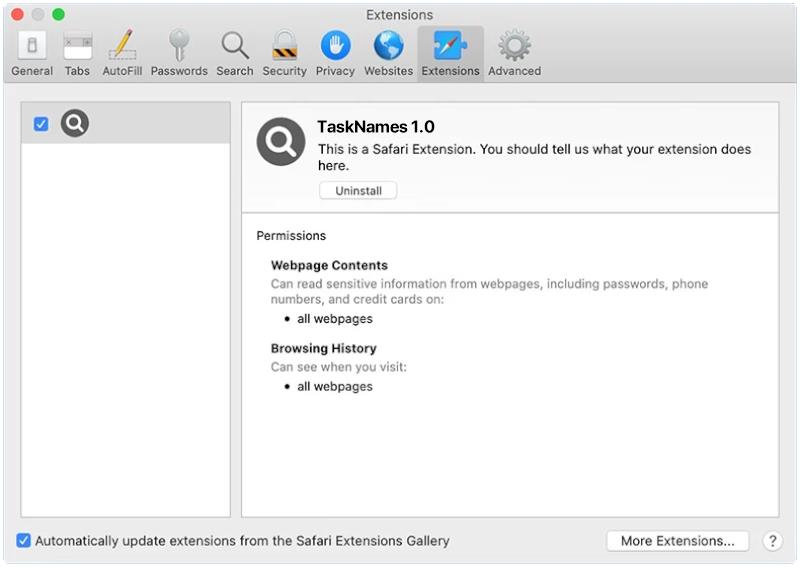
How to remove TerabyteLogoff (Mac)
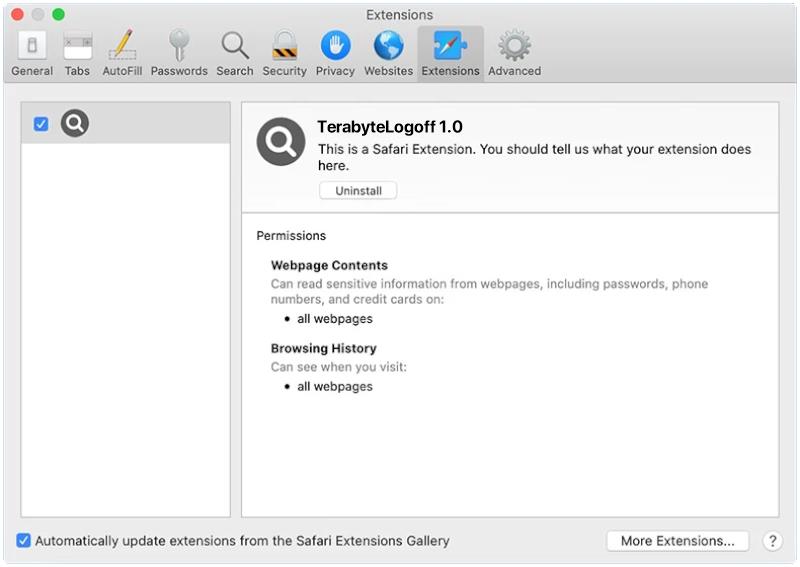
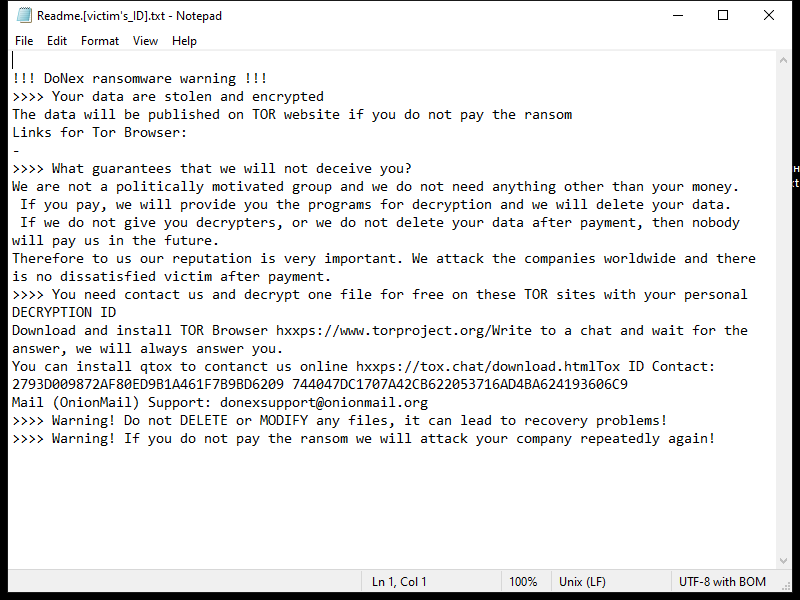
TerabyteLogoff is a type of malware that targets macOS systems. It is designed to infect Mac computers and steal sensitive information from the user, such as login credentials, personal data, and financial information. Once installed on a Mac system, TerabyteLogoff can operate silently in the background, collecting data and sending it to remote servers controlled by cybercriminals.
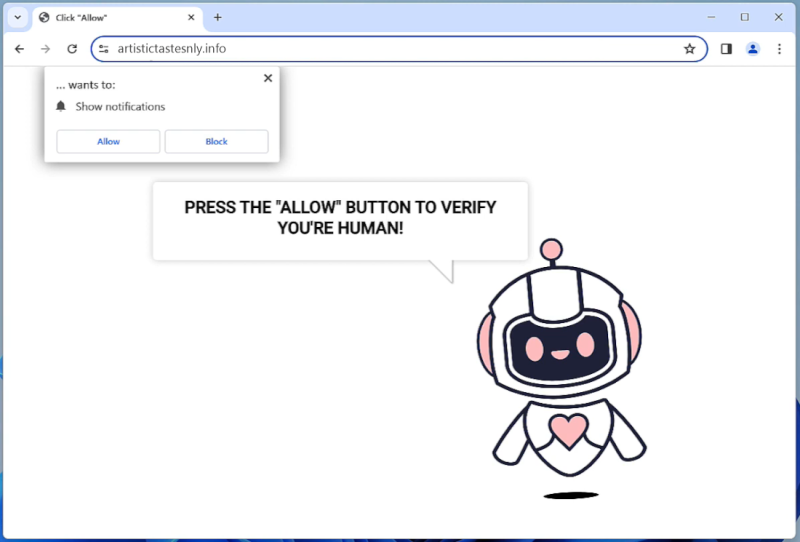
TerabyteLogoff typically infects Mac computers through malicious email attachments, fake software updates, or by exploiting vulnerabilities in the system’s security. Users may unknowingly download and install the malware by clicking on phishing links or downloading untrustworthy software. Once infected, TerabyteLogoff can be difficult to detect and remove, making it a serious threat to the privacy and security of Mac users. Users should be cautious when downloading files or clicking on links from unknown sources to prevent the infection of TerabyteLogoff on their Mac systems.