How to remove DoNex Ransomware and decrypt victim’s id files
DoNex Ransomware is a type of malicious software that encrypts files on a victim’s computer and demands a ransom payment in order to decrypt them. It typically infects computers through email attachments, malicious websites, or software vulnerabilities.
When it encrypts files, DoNex Ransomware adds a specific file extension to them, such as “.donex” or “.encrypted”. It uses advanced encryption algorithms such as AES or RSA to lock the files and make them inaccessible without the decryption key.
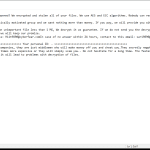
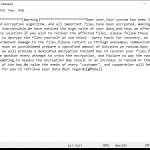
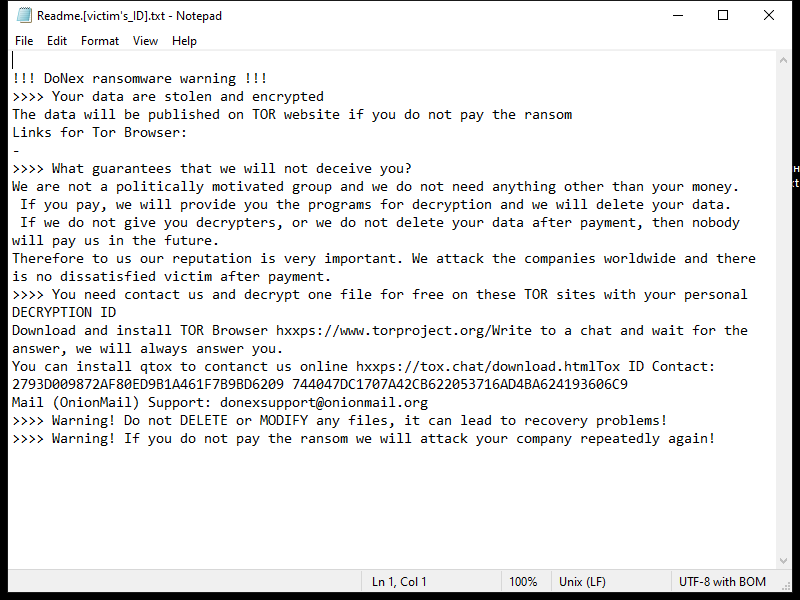
After encrypting the files, DoNex Ransomware creates a ransom note on the victim’s computer, usually in the form of a text file or a pop-up window. The note contains instructions on how to pay the ransom and receive the decryption key.
Unfortunately, there are currently no decryption tools available for DoNex Ransomware. However, victims should not pay the ransom as there is no guarantee that they will receive the decryption key or that their files will be decrypted. Instead, they should try to restore their files from backups or seek help from cybersecurity professionals.
In some cases, security researchers may develop decryption tools for specific ransomware variants, so victims should regularly check reputable cybersecurity websites for updates on decryption tools for DoNex Ransomware.