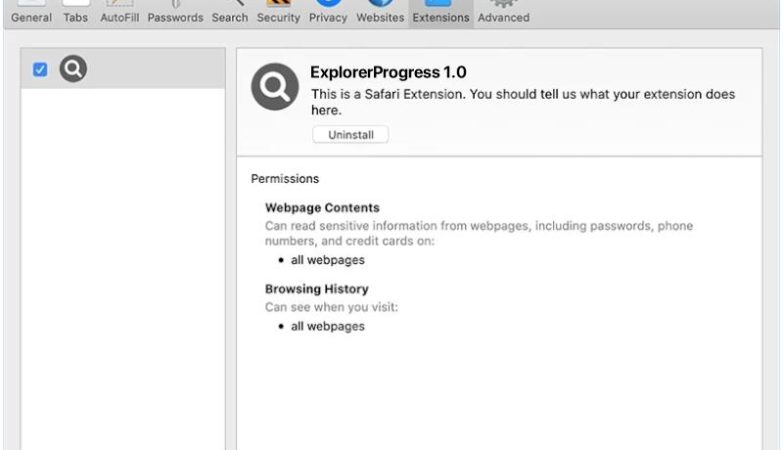
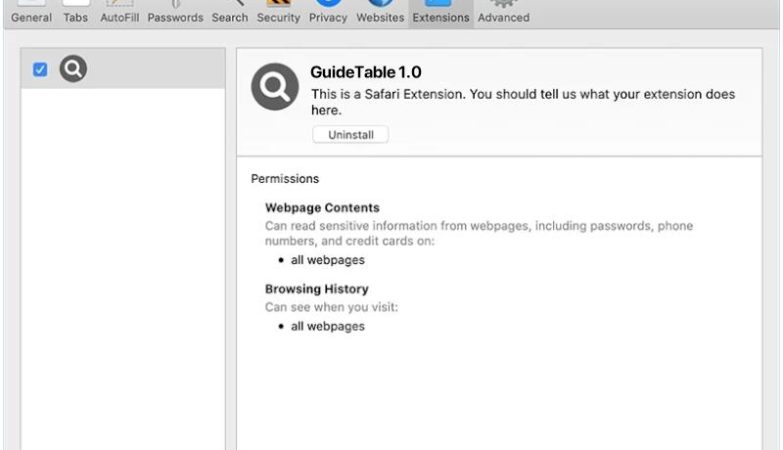
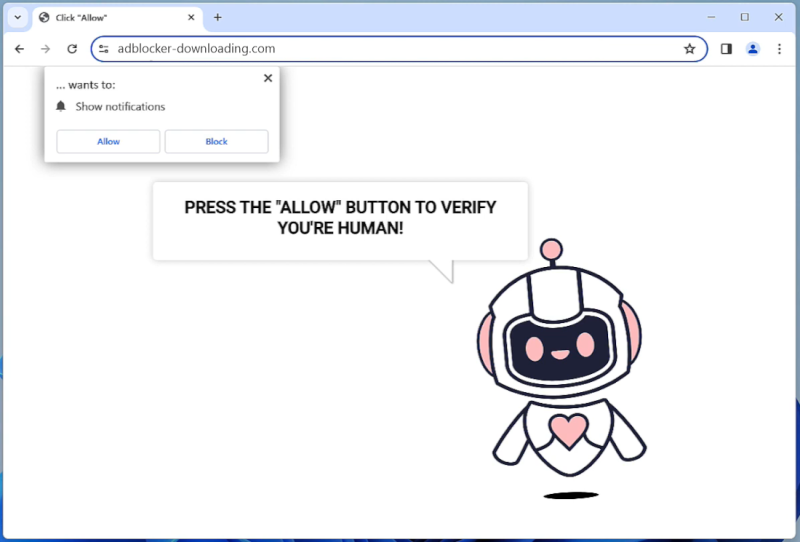
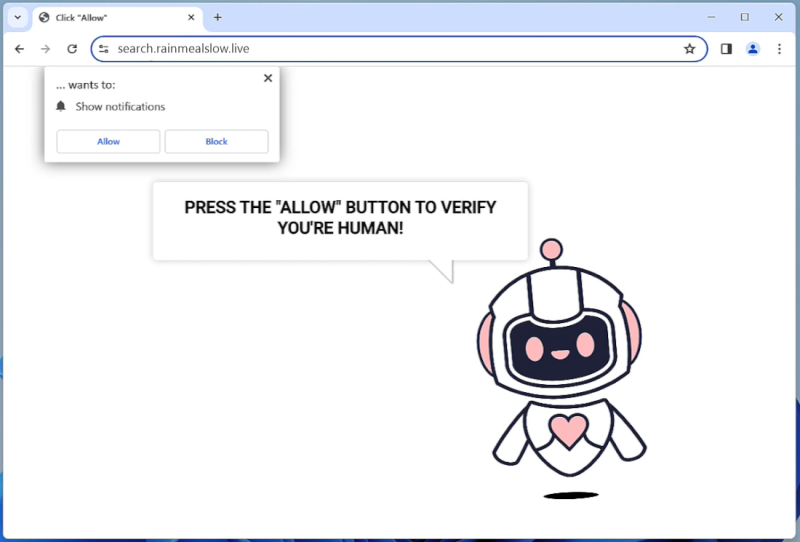
How to remove Artrade #RWA pop-ups
Artrade #RWA is a term that may appear in web browsers due to various reasons. It could be a tracking code or identifier used by a website to monitor user activity, such as tracking clicks, page views, or other interactions. In some cases, it may indicate that the website is utilizing real-time web analytics to track and analyze user behavior on the site.
Another possibility is that Artrade #RWA could be related to a specific plugin, extension, or software that is installed on the browser. These tools often generate unique identifiers or codes to track their own performance or to provide additional functionality to the user. In either case, the appearance of Artrade #RWA in a browser does not necessarily indicate a security threat, but rather a technical feature or tool being utilized by the website or browser.