What is GANDCRAB V5.0 ransomware
GANDCRAB V5.0 is one of the most notorious ransomware threats around the global net. There is 5 versions of this virus, and GANDCRAB V5.0 is the newest one. All of Gandcrab viruses are very dangerous and disastrous for any computer. Cyber criminals are trying to make distribution of their virus as big as possible, the number of victims has critically grown. Hundreds of thousands users got their PC infected with GANDCRAB ransomware. If you are a victim of this encoder, you may use this guide to remove GANDCRAB V5.0 ransomware and decrypt files.
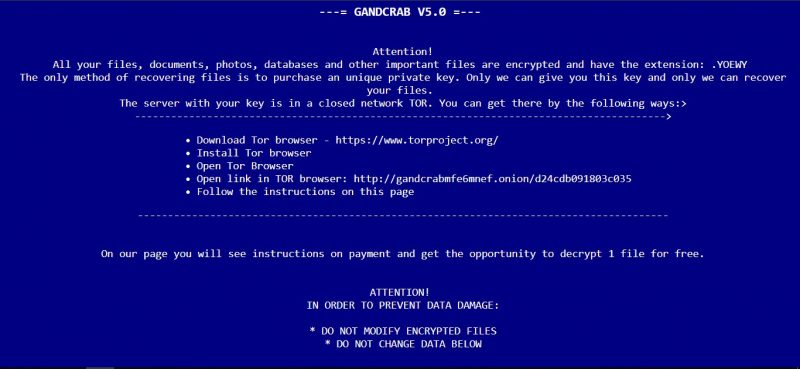
GANDCRAB V5.0 is using Salsa20 and RSA-2048 encryption algorithm to encode personal data of a victim. Encrypted data is not accessible and user can’t open or run encrypted files. The virus may encipher all the important files: any kind of documents (like MS Office), photos, videos, audio files, email files and so on. Then cyber criminals are offering a simple deal – 2400$ in cryptocurrency (in this particular case it is BitCoins or DASH) for decryption (the process reverse to encryption). You may find this offer in any ransom note of this virus.
The ransomware will drop [random characters and numbers]-DECRYPT.html file (for example XMMFA-DECRYPT.html), here is the content of it:
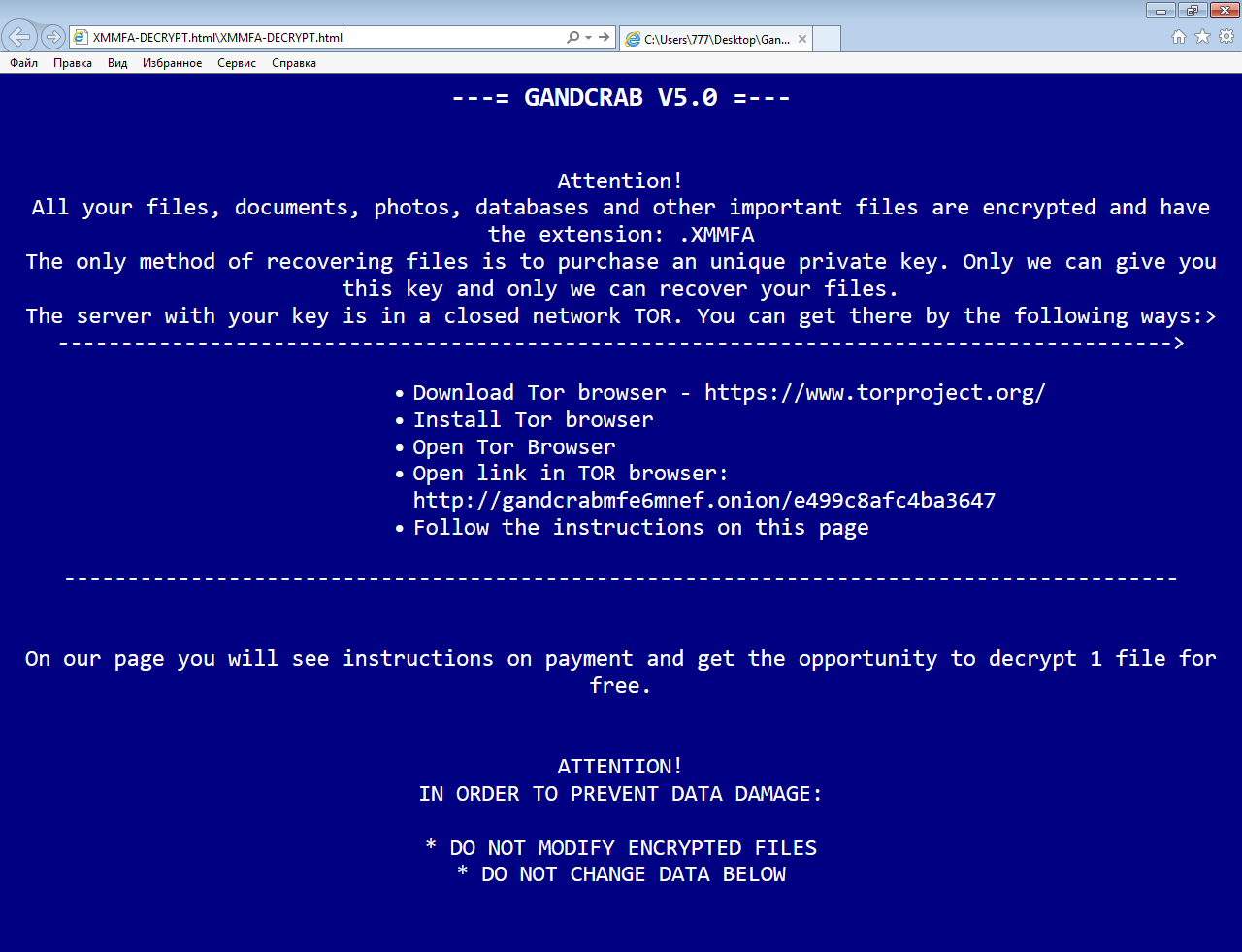
—= GANDCRAB V5.0 =—
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension: .XMMFA
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:>
—————————————————————————————->
•Download Tor browser – https://www.torproject.org/
• Install Tor browser
• Open Tor Browser
• Open link in TOR browser: http://gandcrabmfe6mnef.onion/e499c8afc4ba3647
• Follow the instructions on this page
—————————————————————————————-
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
The virus will also change desktop wallpapers to pidor.bmp as a blackmail message:
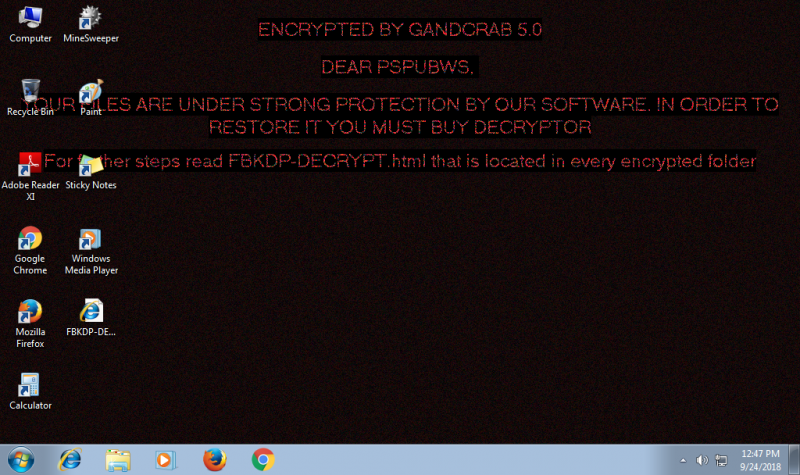
ENCRYPTED BY GANDCRAB 5.0
DEAR Admin YOUR FILES ARE UNDER STRONG PROTECTION BY OUR SOFTWARE IN ORDER TO RESTORE IT YOU MUST BUY DECRYPTOR
For further steps read XMMFA-DECRYPT.html that is located in every encrypted folder.
You may find more information on their onion-site, here is the first page:
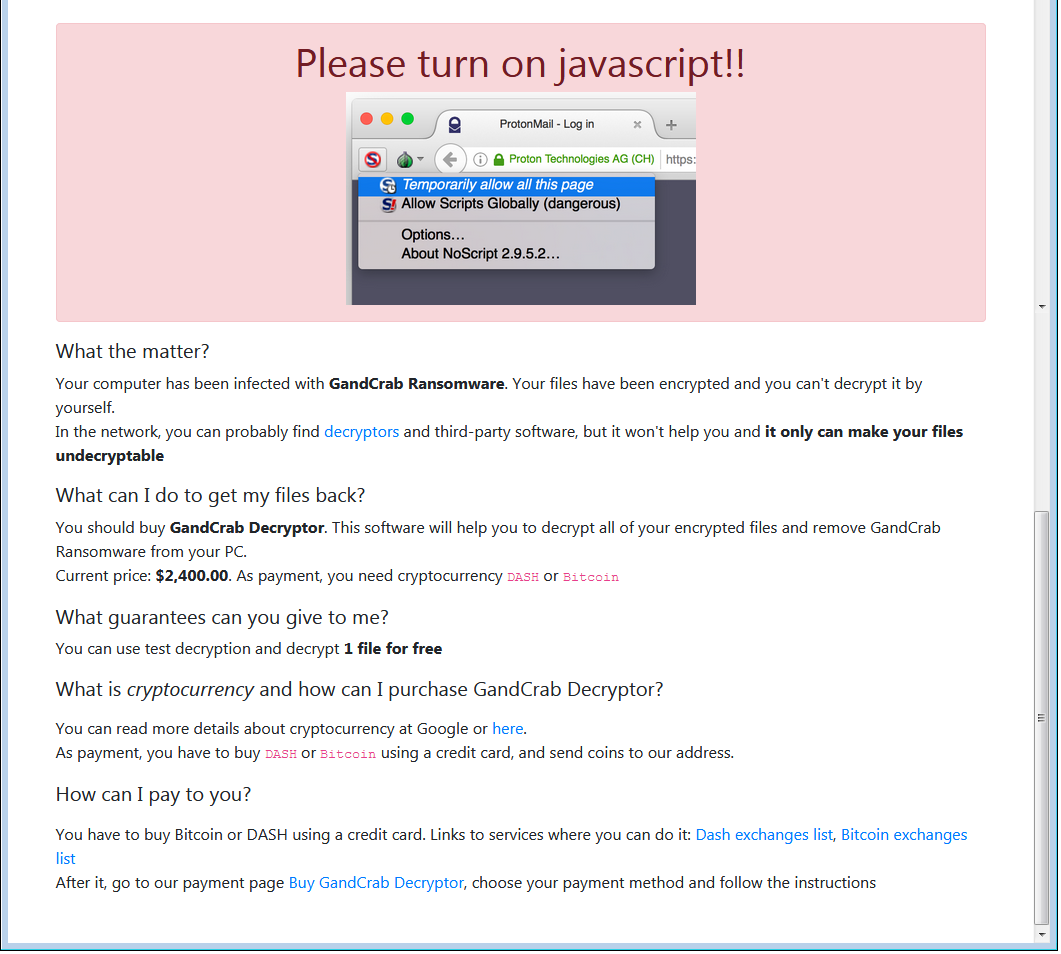
We are sorry, but your files have been encrypted!
Don’t worry, we can help you to return all of your files!
Files decryptor’s price is 2400 USD
If payment isn’t made until 2018-07-20 02:32:41 UTC the cost of decrypting files will be doubled
Amount was doubled!
Time left to double price:
—————————————————————————————–
What the matter? Buy GandCrab Decryptor Support is 24/7 Test decrypt
—————————————————————————————–
Please turn on javascript!!
What the matter?
Your computer has been infected with GandCrab Ransomware. Your files have been encrypted and you can’t decrypt it by yourself.
In the network, you can probably find decryptors and third-party software, but it won’t help you and it only can make your files undecryptable
What can I do to get my files back?
You should buy GandCrab Decryptor. This software will help you to decrypt all of your encrypted files and remove GandCrab Ransomware from your PC.
Current price: $2,400.00. As payment, you need cryptocurrency DASH or Bitcoin
What guarantees can you give to me?
You can use test decryption and decrypt 1 file for free
What is cryptocurrency and how can I purchase GandCrab Decryptor?
You can read more details about cryptocurrency at Google or here.
As payment, you have to buy DASH or Bitcoin using a credit card, and send coins to our address.
How can I pay to you?
You have to buy Bitcoin or DASH using a credit card. Links to services where you can do it: Dash exchanges list, Bitcoin exchanges list
After it, go to our payment page Buy GandCrab Decryptor, choose your payment method and follow the instructions
And the second page:
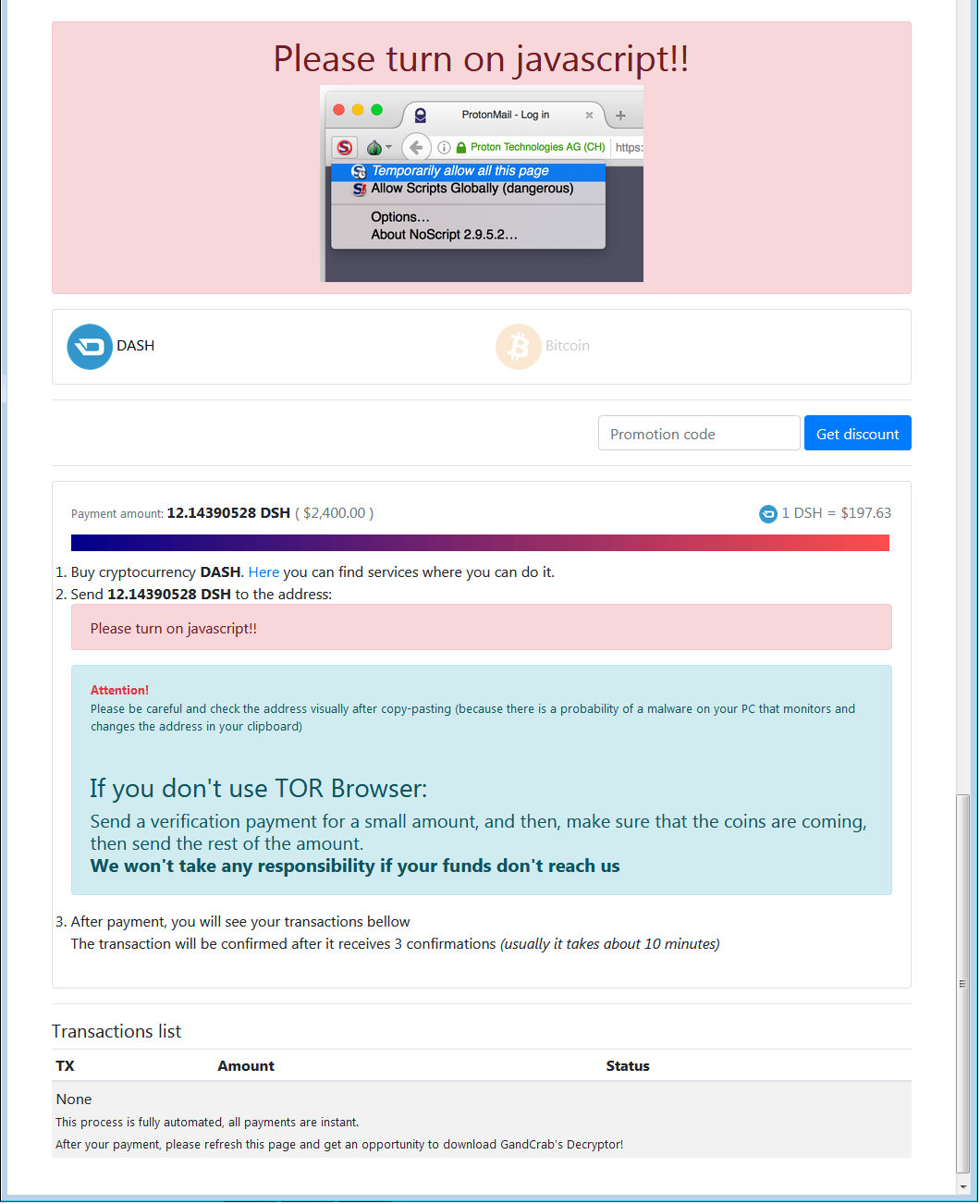
Please turn on javascript!!
DASH
Bitcoin
Promotion code
Payment amount: 12.14390528 DSH ( $2,400.00 )
1 DSH = $197.63
Buy cryptocurrency DASH. Here you can find services where you can do it.
Send 12.14390528 DSH to the address:
Please turn on javascript!!
Attention!
Please be careful and check the address visually after copy-pasting (because there is a probability of a malware on your PC that monitors and changes the address in your clipboard)
If you don’t use TOR Browser:
Send a verification payment for a small amount, and then, make sure that the coins are coming, then send the rest of the amount.
We won’t take any responsibility if your funds don’t reach us
After payment, you will see your transactions bellow
The transaction will be confirmed after it receives 3 confirmations (usually it takes about 10 minutes)
Transactions list
TX Amount Status
None
This process is fully automated, all payments are instant.
After your payment, please refresh this page and get an opportunity to download GandCrab’s Decryptor!
Important note: In order to infect their victims, GANDCRAB V5.0 uses method of fraudulent downloads with hacked, repacked (RePack) and infected installers of popular programs, games and other software. When users download and run any of these infected programs, they will install GANDCRAB V5.0. Also we must warn you that usually cyber criminals do not answer to their victims, so there is no use to spend huge money on a ransom, especially when you can remove the virus by using this guide.
Here’s the list of extensions that GANDCRAB V5.0 ransomware will encrypt:
.cat, .csv, .db, .doc, .gif, .htm, .ico, .inf, .ini, .jpg, .png, .ppt, .sam, .shw, .txt, .url, .xls, .xml, .wav, .wb2, .wk4, .wpd, .wpg
These are MS Office documents, OpenOffice, PDF, text files, databases, photos, music, video, image files, archives and so on.
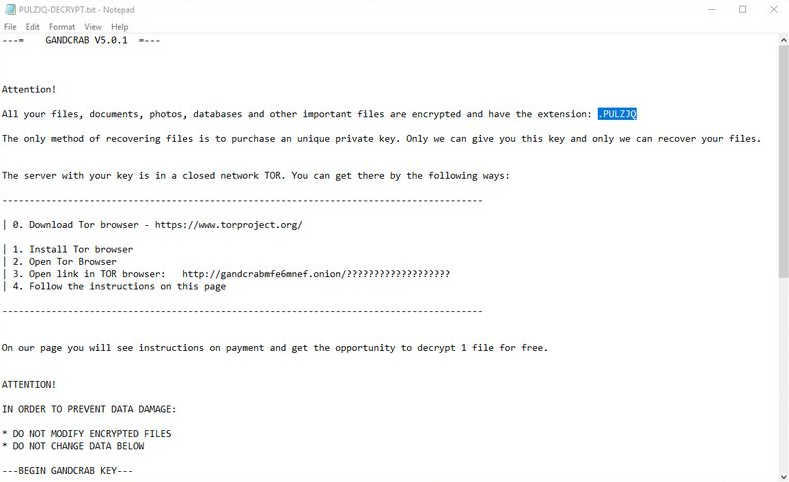
UPDATE: GANDCRAB V5.0.1
The developers of this terrible ransomware would not stop until they have fail-safe version of their virus, so that they can infect more victims and generate more profit. The extension is still the same – random characters and numbers. Ransom note have switched from an .HTML to a .TXT: DECRYPT.txt.
UPDATE: GANDCRAB V5.0.2
Another one version of GandCrab. The extension is still random. Cyber crooks are probably trying out some new technics of malware distribution. However, the workflow of this ransomware is quite the same. Here you may see the new ransom note and upgraded pidor.bmp wallpaper.
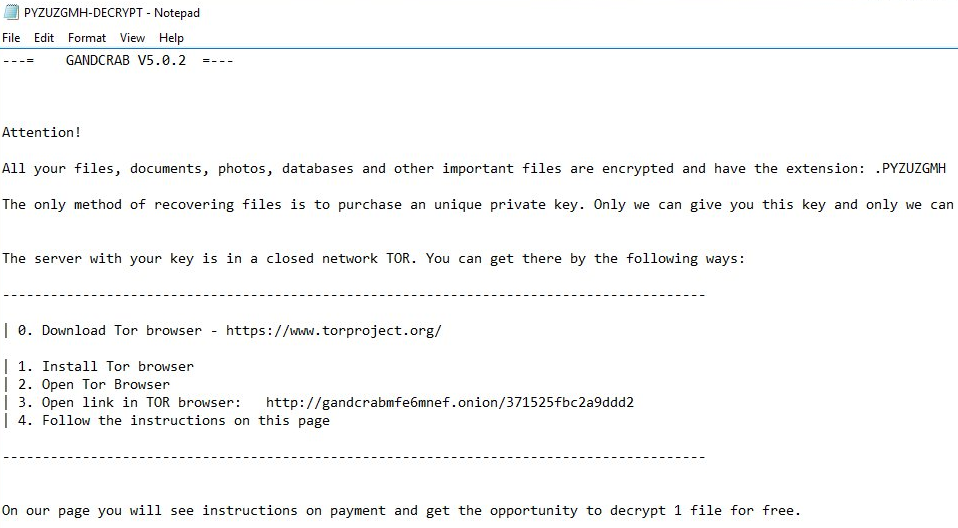
—= GANDCRAB V5.0.2 =—
Attention!
All your files, documents, photos, databases and other important files are encrypted and have the extension: .EIUHTXJZS
The only method of recovering files is to purchase an unique private key. Only we can give you this key and only we can recover your files.
The server with your key is in a closed network TOR. You can get there by the following ways:
—————————————————————————————-
| 0. Download Tor browser – https://www.torproject.org/
| 1. Install Tor browser
| 2. Open Tor Browser
| 3. Open link in TOR browser:
| 4. Follow the instructions on this page
—————————————————————————————-
On our page you will see instructions on payment and get the opportunity to decrypt 1 file for free.
ATTENTION!
IN ORDER TO PREVENT DATA DAMAGE:
* DO NOT MODIFY ENCRYPTED FILES
* DO NOT CHANGE DATA BELOW
—BEGIN GANDCRAB KEY—
lAQAALRIFLlHrvGelKfYkRPhOg4DIks7v***
—END GANDCRAB KEY—
—BEGIN PC DATA—
wfKD6iudumBkmpL8IRr4U4OxG1avOXPt***
—END PC DATA—

UPDATE 10/5/2018: Be cautious
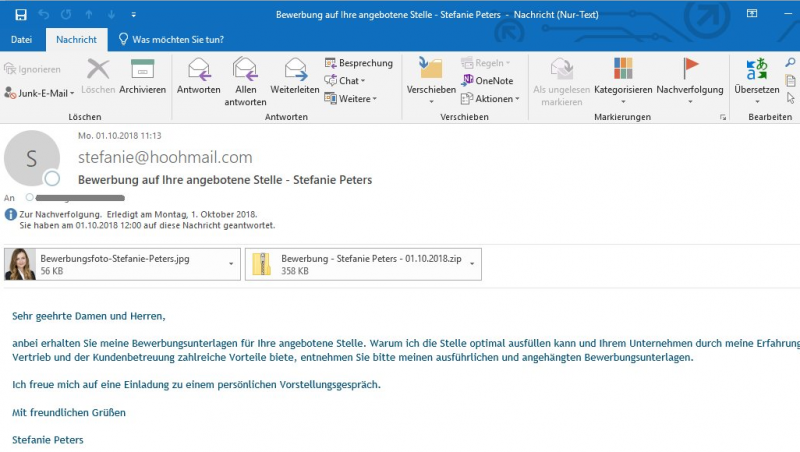
It is common knowledge that most of ransomware viruses use spam emails as a method of distribution. Cyber criminals screen their viruses behind email messages with infected attachments, so that their victims will voluntarily open them, making virus infiltration process much easier. That’s why we strongly recommend not to open any suspicious and shady attachments from unknown emails. Cyber crooks make use of anything that can force a user to open such email: fake memos, messages from big and trusted shops like Amazon or Ebay, congratulation letters about winning some expensive gadgets or big sum of money, and so on. For example, here is the letter that the victim of GandCrab V5.0 may receive (German version):
UPDATE: GANDCRAB 5.0.3
There is a new version of GANDCRAB 5.0 floating around the internet. Nothing brand new about it, though. Cyber criminals are eager to maintain the numbers of their victims, that is the main reason of generating all these new versions of GANDCRAB 5.0. In GANDCRAB 5.0.3 we may find new ransom note, where cyber crooks are trying to convince their victims not to delete related to ransomware files until their data is encrypted.
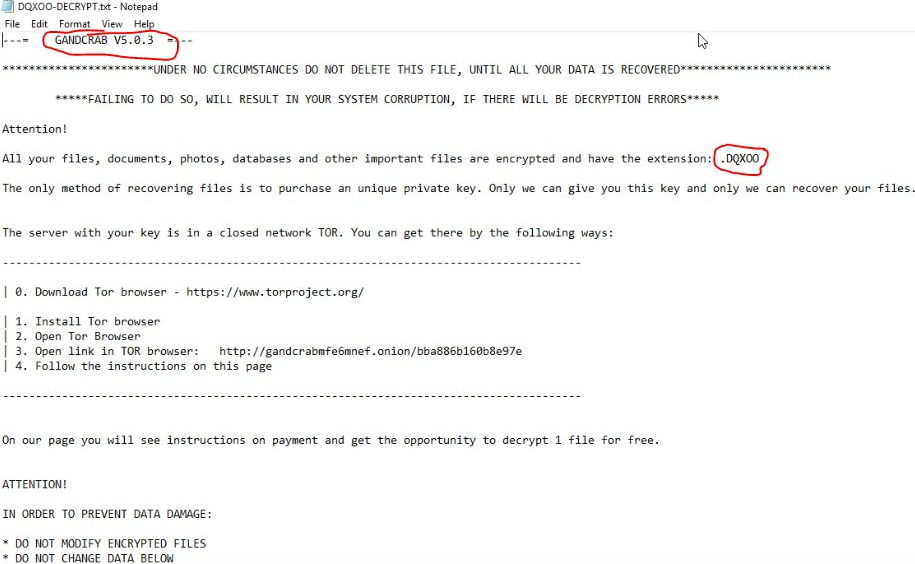
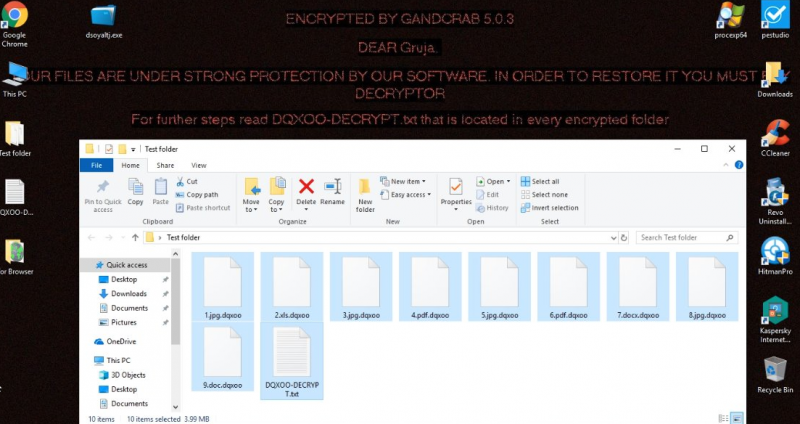
Examples of infected by GANDCRAB 5.0.3 files:
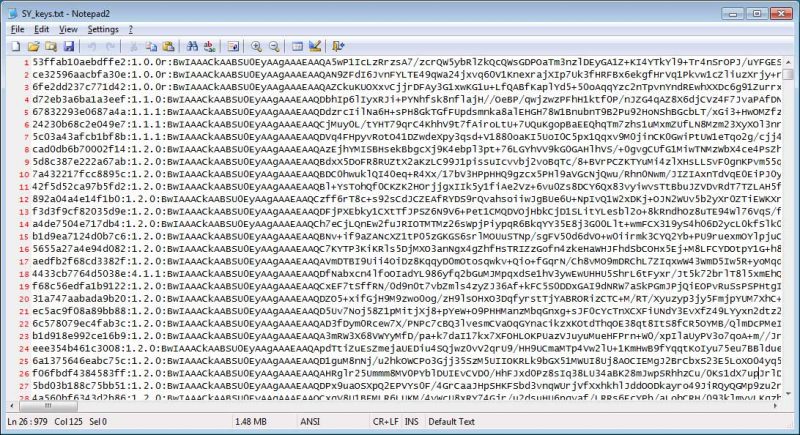
UPDATE: SYRIAN DECRYPTION KEYS
The developers of GandCrab 5 have released free decryption keys for the Syrian victims (includes this and all other versions of GandCrab).
There are two solutions of this problem. First is to use special Removal Tool. Removal Tools delete all instances of malware by few clicks and help user to save time. Or you can use Manual Removal Guide, but you should know that it might be very difficult to remove GANDCRAB V5.0 ransomware manually without specialist’s help.
How to remove GANDCRAB V5.0 ransomware automatically:
Thor Home may help you to get rid of this virus and clean up your system. In case you need a proper and reliable antivirus, we recommend you to try it.

Manual GANDCRAB V5.0 Removal Guide
Here is step-by-step instructions on how to remove GANDCRAB V5.0 from Windows and Mac computers. Follow this steps carefully and remove files and folders belonging to GANDCRAB V5.0. First of all, you need to run system in a Safe Mode. Then find and remove needed files and folders.
Uninstall GANDCRAB V5.0 from Windows or Mac
Here you may find the list of confirmed related to the ransomware files and registry keys. You should delete them in order to remove virus, however it would be easier to do it with our automatic removal tool. The list:
-DECRYPT.html
%s-DECRYPT.html
%s-DECRYPT.txt
XMMFA-DECRYPT.html
IBAGX-DECRYPT.html
QIKKA-DECRYPT.html
KRAB-DECRYPT.html
KRAB-DECRYPT.txt
CRAB-DECRYPT.txt
pidor.bmp
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to GANDCRAB V5.0 by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to GANDCRAB V5.0 by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to GANDCRAB V5.0 by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to GANDCRAB V5.0 by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple logo appears;
- Find programs or files potentially related to GANDCRAB V5.0 by using Removal Tool;
- Delete found files;
How to restore encrypted files
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
This program can restore the encrypted files, it is easy to use and very helpful.
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Restore encrypted files using Recuva
There is an alternative program, that you may use – Recuva.
- Run the Recuva;
- Follow instructions and wait until scan process ends;
- Find needed files, mark them and Press Recover button;
How to prevent ransomware infection?
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
Malwarebytes
SpyHunter is a reliable antimalware removal tool application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.
Additional information
In case this instruction would not help, you may use our decryption service. First of all, please refer to this instruction:
- Decryption by our service usually takes at least 5 business days.
- Our service may process about 3-4 test files from different directories with the file size no more than 8 MB.
- The files must be unique files from your computer, there must be no files that me be found in open access in the internet.
- Once test decryption and analyzing procedures are finished, we will inform you about possibility, cost and term of decryption.
Now you are ready to fill up the form below, thank you for your cooperation:


thanks! removal tool worked for me and Data Recovery Pro is quite helpful too
Thank you sir, if you have any questions – feel free to ask!
Does this really work? I do not know if this is something simple to be true.
You may find out only by following our instructions, sir. Feel free to comment any time.
Can you remove the gandcrab v5.0.2 virus?
Yes, this guide is relevant for this version of GandCrab too.
thank you for help, this data recovery pro works for me
I am glad to hear it, thank you for your feedback!
your guide really do the job, thanks!!!
Please, i need some help. I tried to recover encrypted files via Recuva. I followed program instructions, but the result of recovered file was still file with encrypted extension letters. Extension did´t get back to original. Can anyone describe step by step instructions to decrypt file ? Thanks for any help.
Good day, Lukas. You should try Data Recovery Pro or Stellar Phoenix Windows Data Recovery programs for data recovery, these applications have more chances to recover your files. You may learn about these programs in this article – click here.
Thank you for response. I found out the recovery programs as Data Recovery Pro, Stellar Phoenix Windows Data Recovery, Recuva and etc recovery programs can recover your files only if files shadows are exising. Otherwise you can not recover your files. Recovery softwares can not to do decryption of files. Best solution for me (because of no payment required) was Shadow Explorer. I recovered files with shadows files only. The other files that have not shadow files are still encrypted.
Today i attacked by GrandCrab ransomware virus, with a new extension of .ollao.
Please help me to decrypt my data.
Good day, Hassan. This extension is not new, GandCrab generates random extensions for all their victims. There is no possible way to decrypt GandCrab 5 files for a moment, but you can use recovery software in order to restore your files, use this link – click here. We recommend you to use Stellar Phoenix Windows Data Recovery or Data Recovery Pro application.
can you remove and decrypt file after Gandcrab 5.0.4 attack?
Yes, sir. This guide is relevant for Gandcrab 5.0.4 version too.