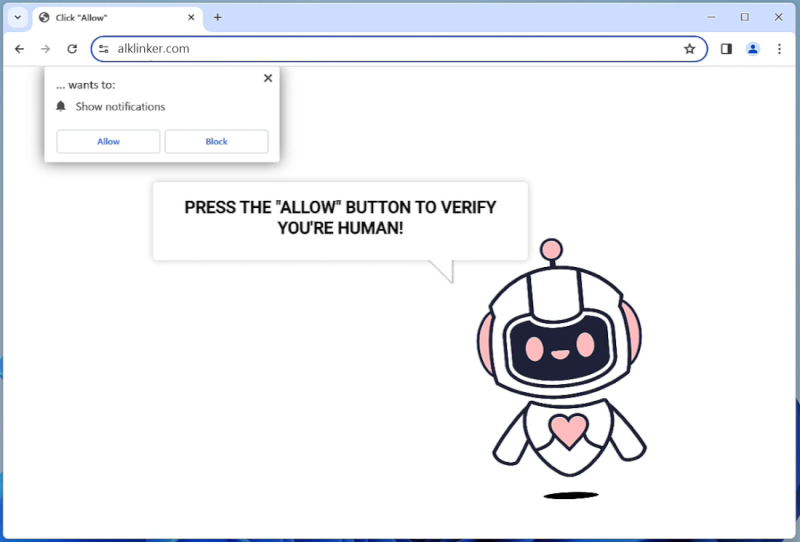
Carthemetab.com is a type of adware that typically infiltrates computers and web browsers without the user’s consent. This adware is designed to display intrusive advertisements, pop-ups, and redirects while users are browsing the internet. Carthemetab.com may also track users’ online activities and collect personal information for targeted advertising purposes.
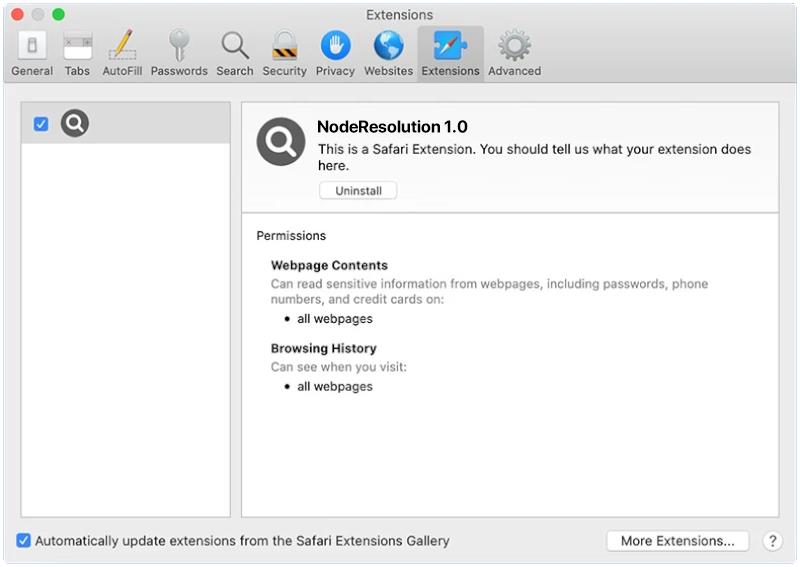
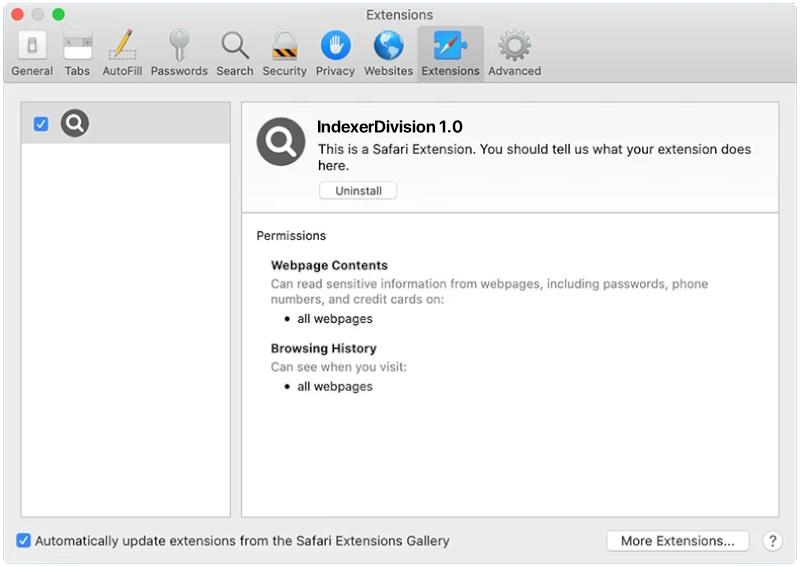
Carthemetab.com usually infects computers through software bundling, where it is included in the installation package of freeware or shareware programs. When users download and install these programs, the adware is also installed without their knowledge. Additionally, clicking on malicious links or visiting compromised websites can also lead to the infiltration of Carthemetab.com. Once installed, Carthemetab.com alters browser settings and injects unwanted ads into websites, disrupting the user’s browsing experience.