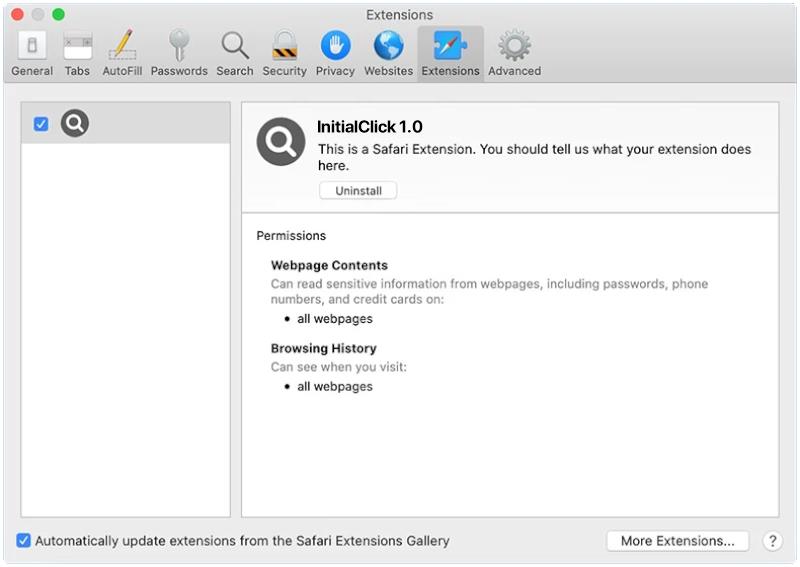
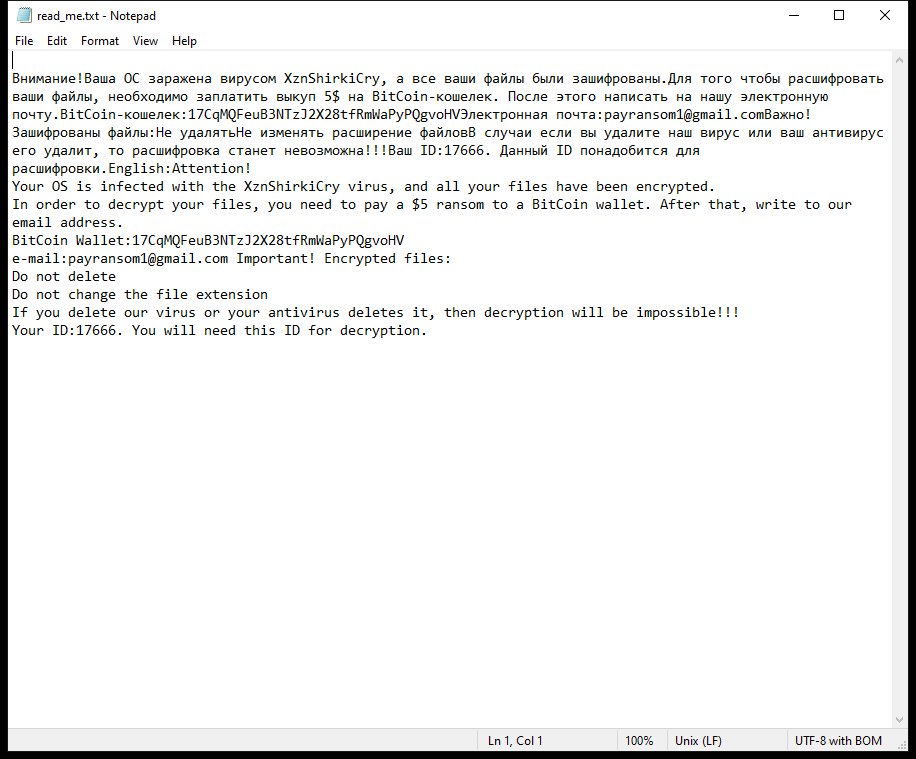
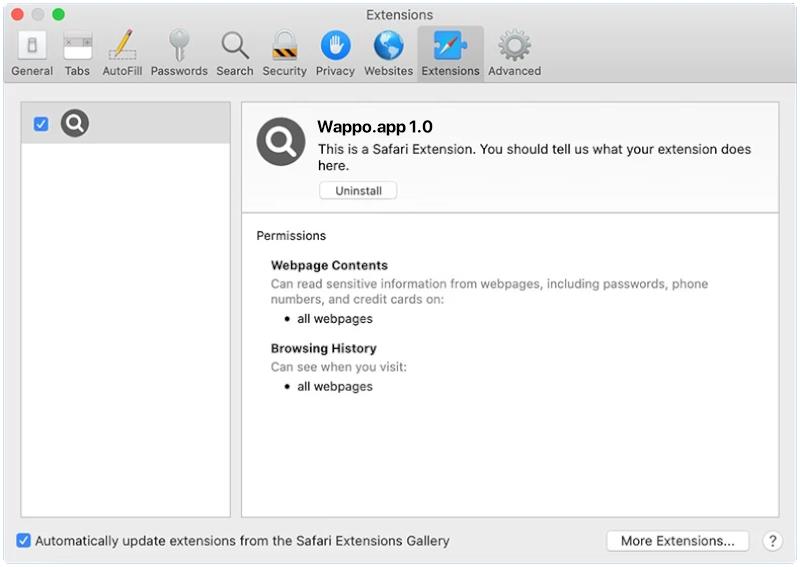
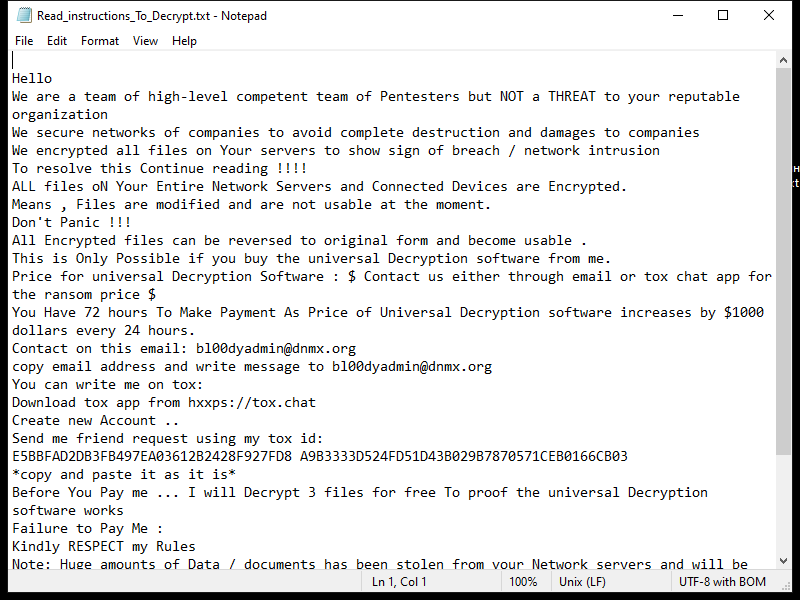
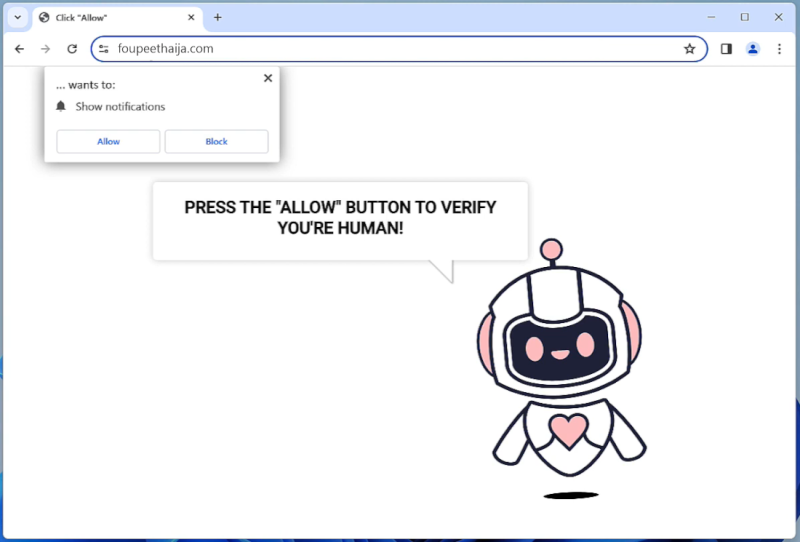
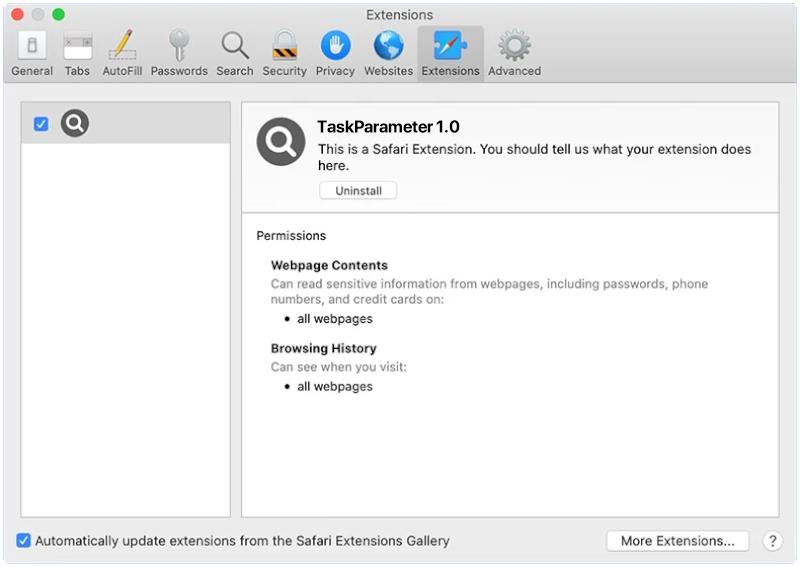
InitialClick is a type of malware that specifically targets Mac devices. It is designed to infect Mac computers and steal sensitive information such as login credentials, financial data, and personal information. InitialClick can enter a Mac device through various methods, including email attachments, malicious websites, and software downloads. Once it infects a Mac device, InitialClick can run in the background without the user’s knowledge, allowing cybercriminals to access and steal data from the infected device.
InitialClick can also spread to other devices on the same network, making it important for Mac users to take precautions to protect their devices from this type of malware. To avoid becoming infected with InitialClick, Mac users should be cautious when downloading software or files from unknown sources, avoid clicking on suspicious links in emails or websites, and keep their operating system and security software up to date. Additionally, using strong and unique passwords for online accounts can help protect against data theft by malware like InitialClick.