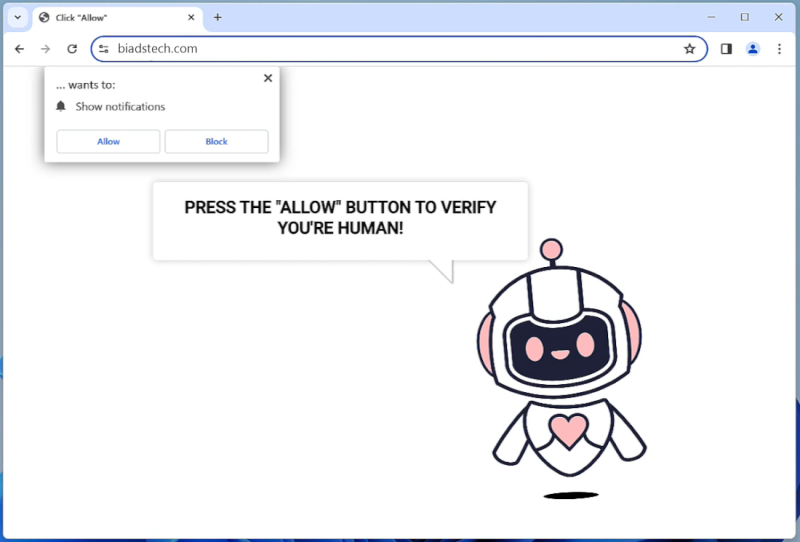
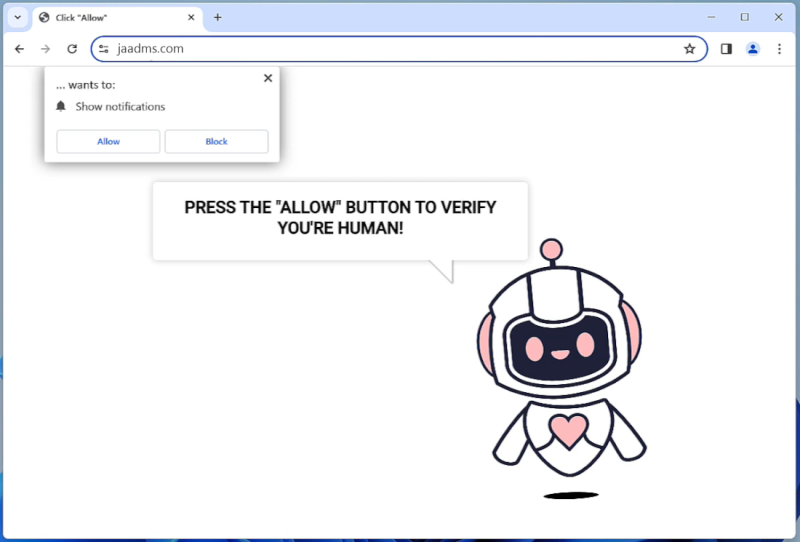
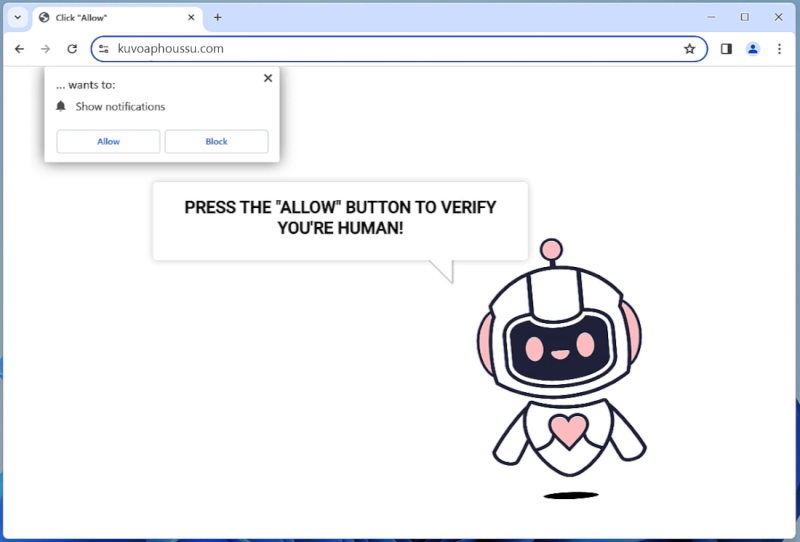
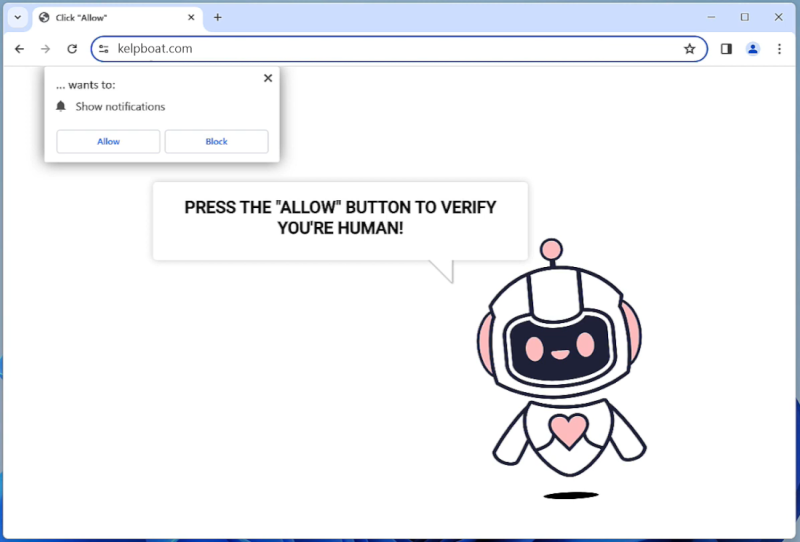
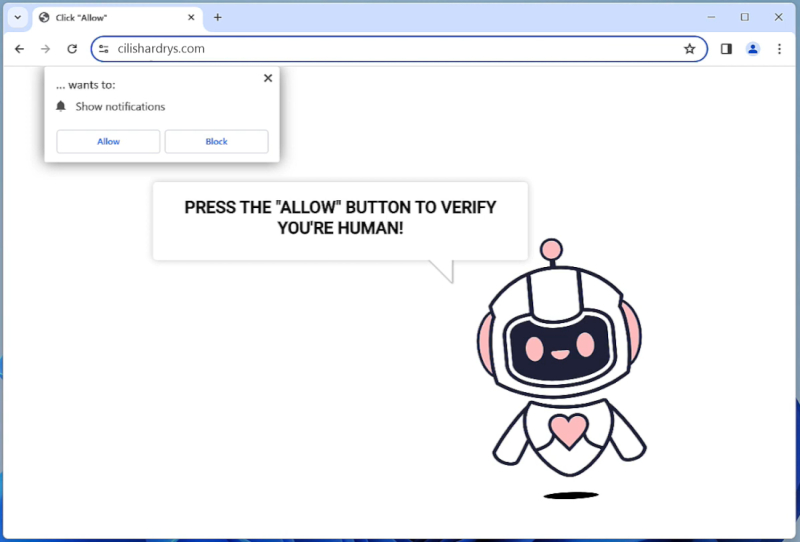
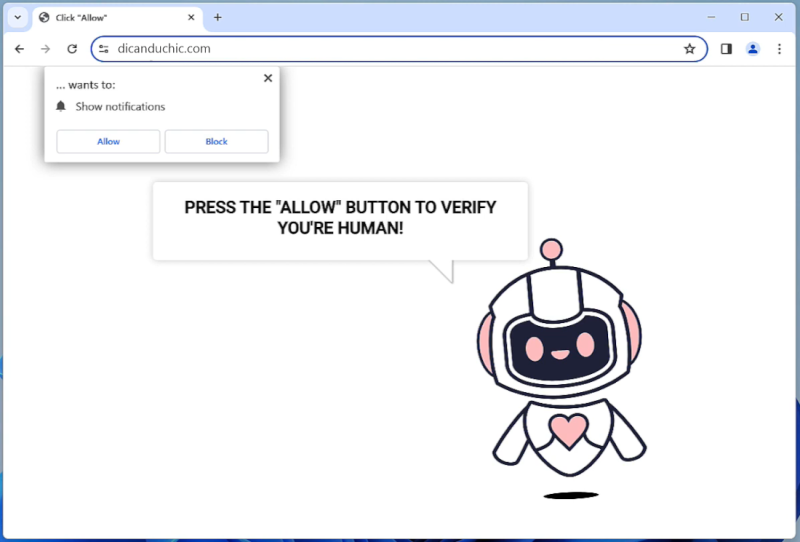
Biadstech.com is a malicious website that infects computers by using deceptive techniques to trick users into allowing browser notifications. Once a user visits the website, they may be prompted with a message asking them to click “Allow” to enable notifications. If the user clicks on this, they unknowingly give permission for Biadstech.com to send unwanted notifications to their browser.
This website exploits browser notifications by sending a constant stream of pop-up notifications advertising various products or services. These notifications can be intrusive and disruptive to the user’s browsing experience. Biadstech.com can infect a variety of browsers such as Google Chrome, Mozilla Firefox, and Safari, as well as different devices including desktop computers, laptops, and mobile devices. Users should be cautious when visiting unfamiliar websites and avoid clicking on any suspicious pop-up messages to prevent their devices from being infected by Biadstech.com.