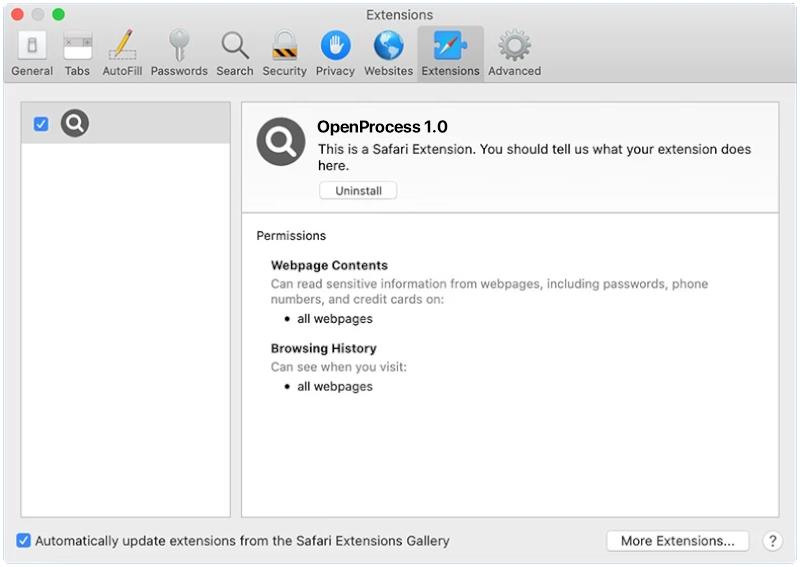
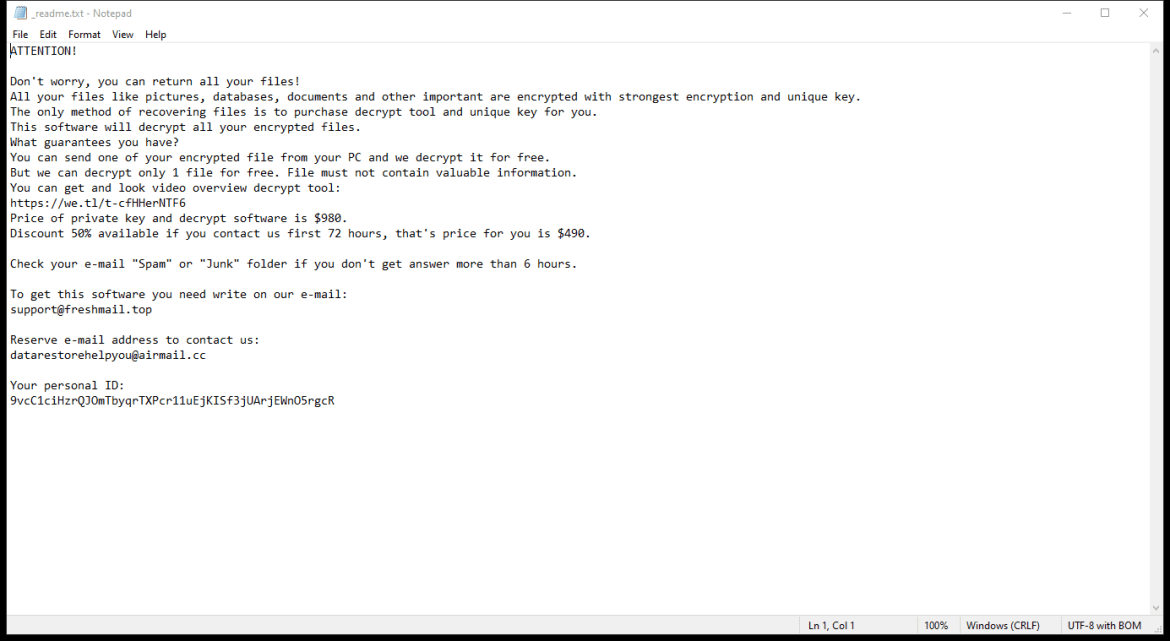
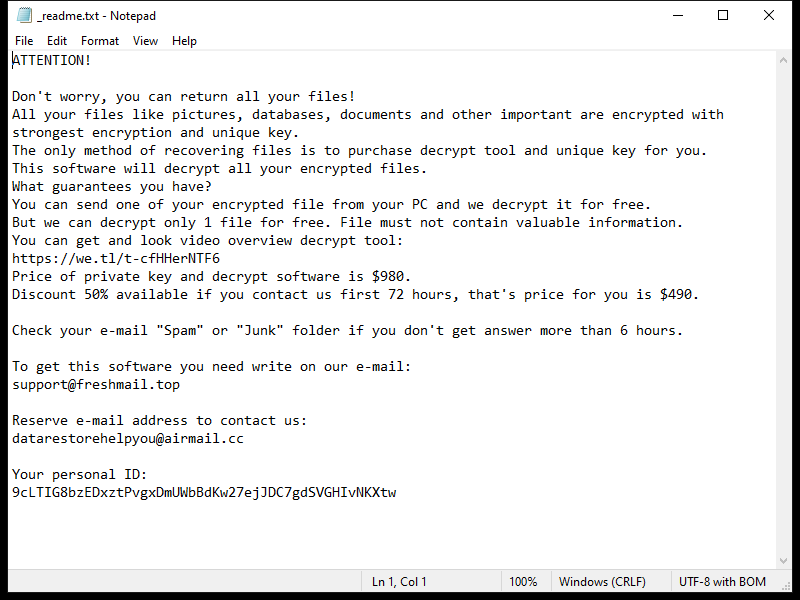
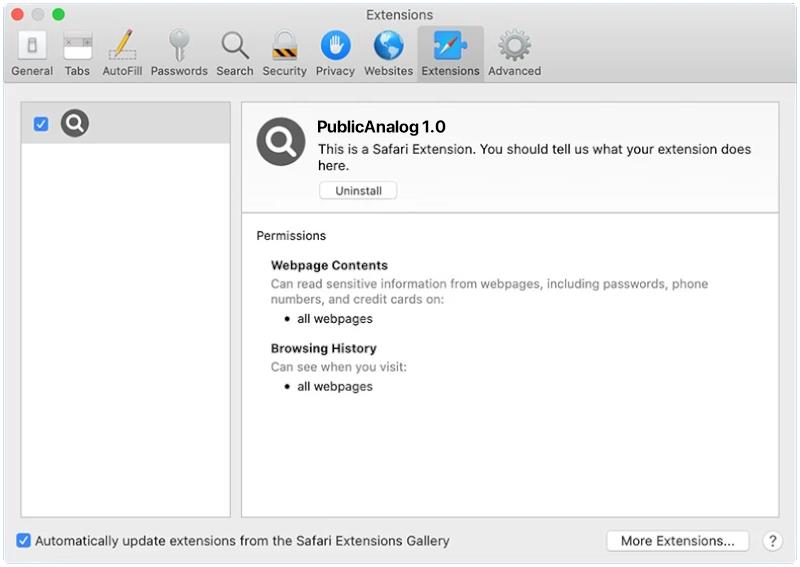
OpenProcess is a type of malware that specifically targets Mac operating systems. This malware is designed to infiltrate a user’s system and gain unauthorized access to sensitive information, such as personal data, passwords, and financial information. OpenProcess can infect a Mac through various means, including malicious email attachments, fake software downloads, and compromised websites.
Once OpenProcess infects a Mac, it can run in the background without the user’s knowledge, collecting and transmitting data to remote servers controlled by cybercriminals. This malware can also install additional malicious software onto the infected system, further compromising its security and stability. To protect against OpenProcess and other types of malware, Mac users should practice safe browsing habits, avoid clicking on suspicious links or downloading unknown files, and regularly update their operating system and security software.