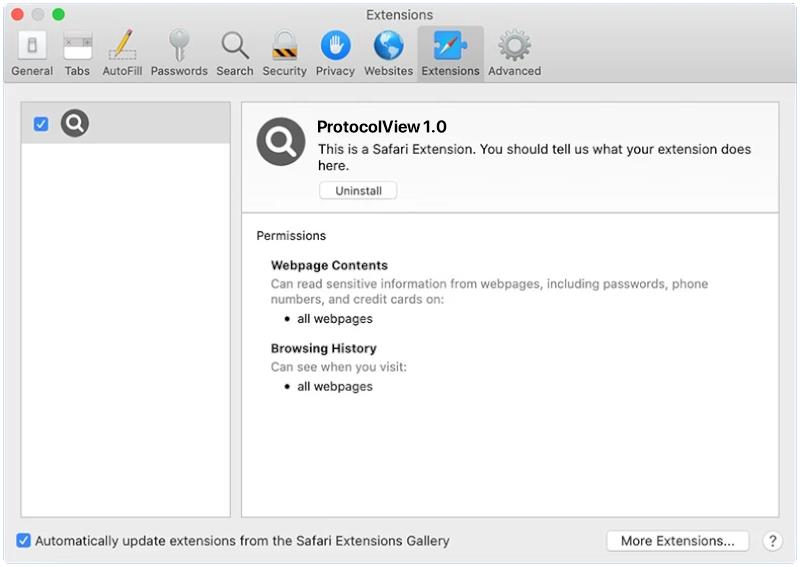
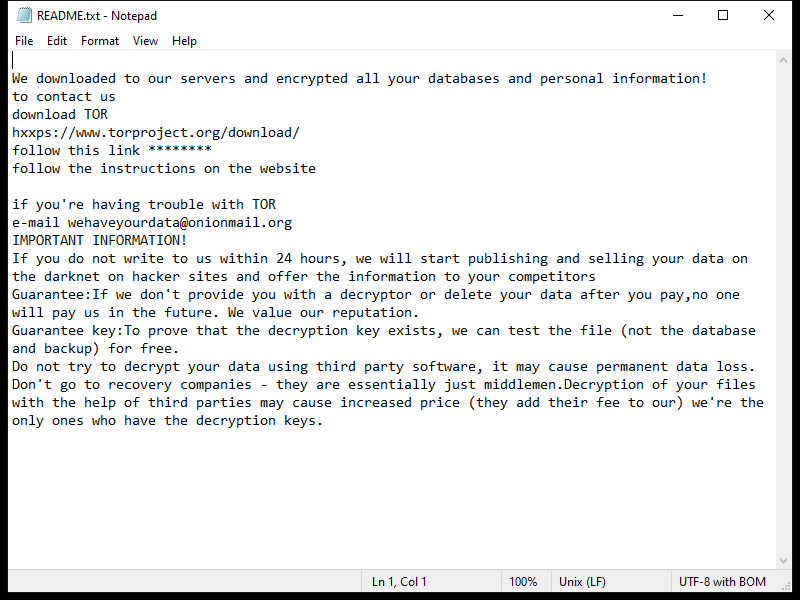
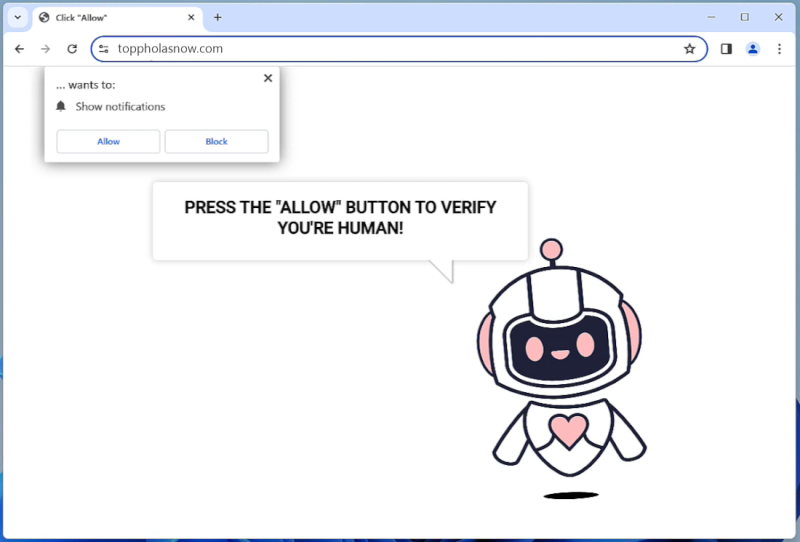
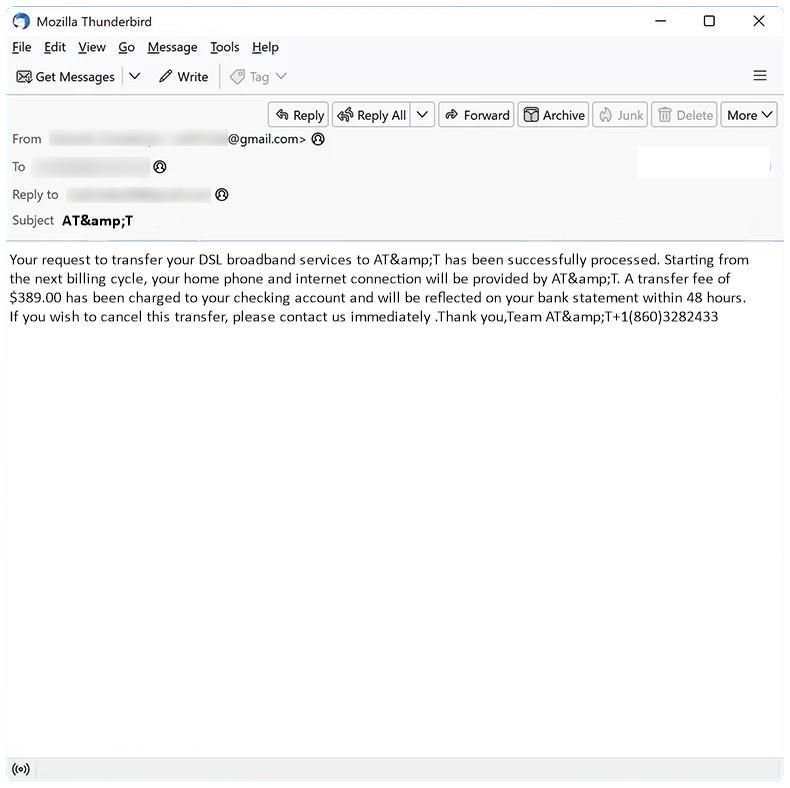
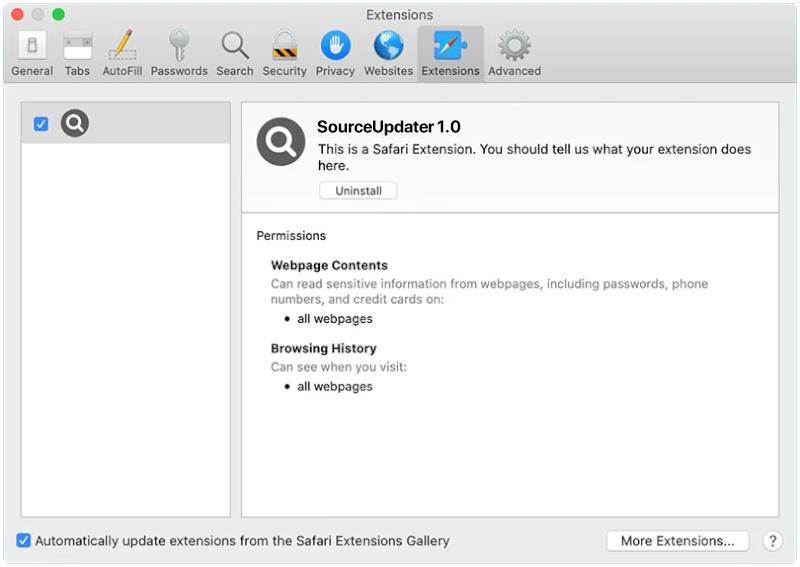
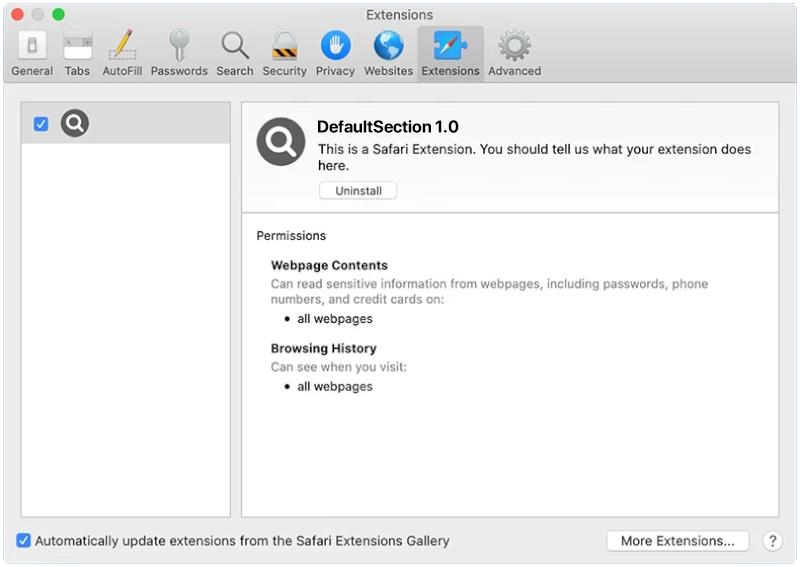
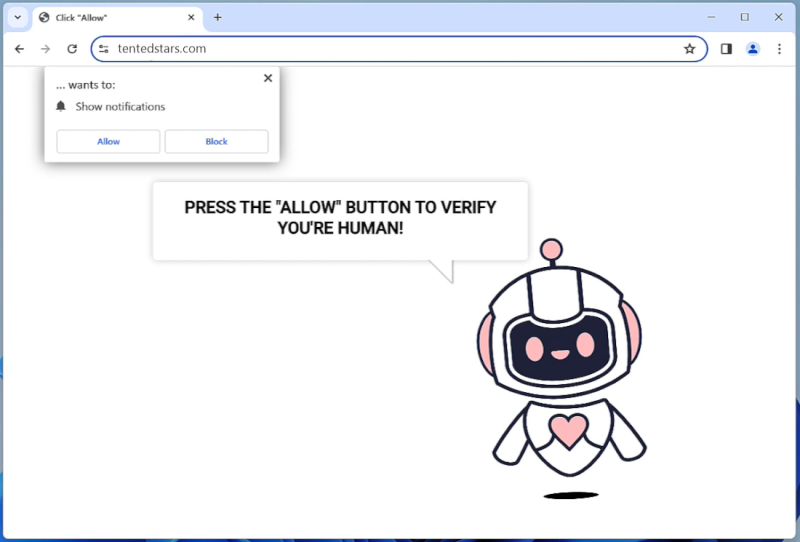
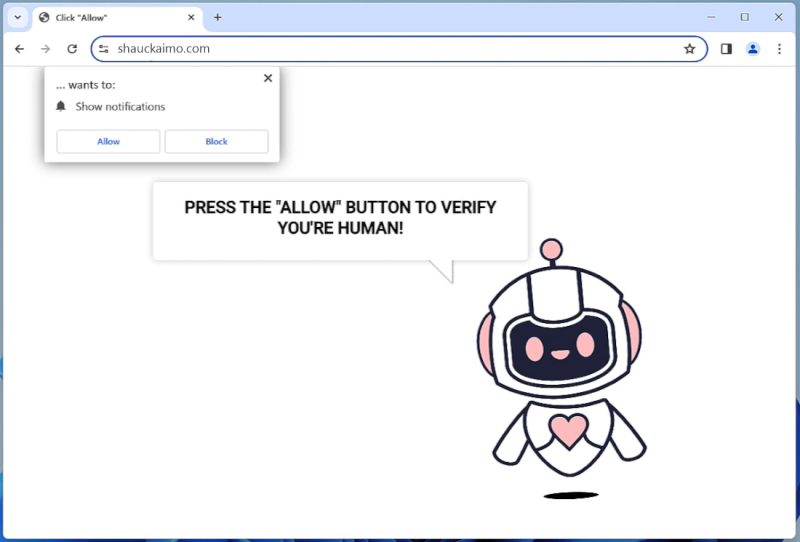
ProtocolView is a type of malware that specifically targets Mac devices. This malware is designed to infect Mac computers by infiltrating the system through various means, such as phishing emails, malicious websites, or software downloads. Once ProtocolView infects a Mac device, it can gain access to sensitive information, track user activity, and even take control of the system.
ProtocolView is a stealthy malware that can be difficult to detect and remove from a Mac device. It can disguise itself as a legitimate application or file, making it challenging for users to identify and remove it. Additionally, ProtocolView can spread to other devices on the same network, putting the entire system at risk of being compromised. It is important for Mac users to be vigilant and take precautions to protect their devices from malware like ProtocolView.