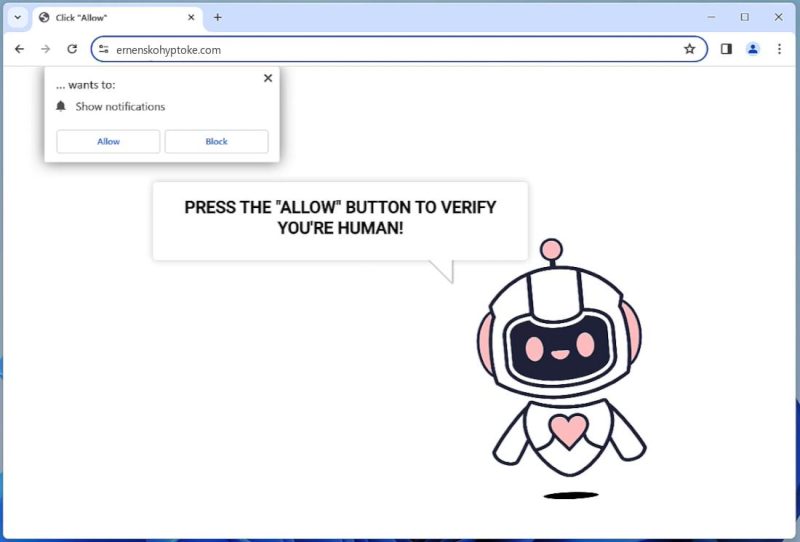
Ernenskohyptoke.com is a deceptive website that is known for running a malicious browser notification scam. It’s a type of browser hijacker that manipulates the browser settings without the user’s consent and starts displaying intrusive advertisements. It infects computers through deceptive pop-up ads, freeware or shareware programs, spam emails, or infected websites. Once clicked or downloaded, the malware initiates unauthorized changes in the browser settings. Ernenskohyptoke.com exploits browser notifications by prompting users to enable notifications for updates or to view content. Once the user clicks ‘Allow’, it starts to send unwanted ads and potentially harmful links directly to their desktop. The website’s notifications can appear in any browser including Google Chrome, Mozilla Firefox, and Internet Explorer, and can infect any device including Windows, macOS, or Android. The main purpose of this malware is to generate revenue from these intrusive ads and to redirect traffic to other malicious websites.
Author: admin
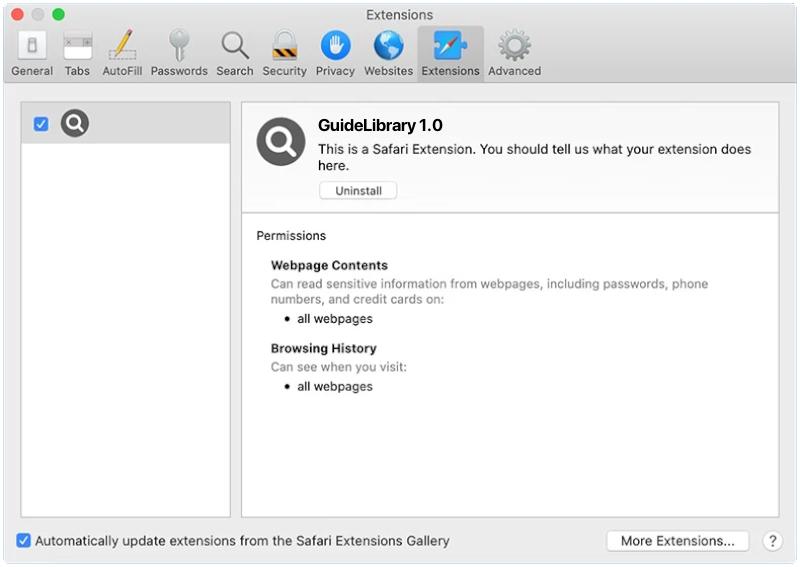
How to remove GuideLibrary (Mac)
GuideLibrary is a type of adware that is specifically designed to target Mac operating systems. It is often bundled with other software or disguised as a useful application, and once installed, it begins to generate intrusive advertisements and pop-ups. This adware can also redirect users to potentially harmful websites, collect personal data, and negatively impact the performance and speed of the affected device. GuideLibrary typically infiltrates a Mac system through deceptive techniques such as “bundling” or “social engineering”. In bundling, the adware is packaged with other free software that the user downloads and installs. The user may not be aware that they are also installing the adware. Social engineering, on the other hand, involves tricking the user into downloading and installing the adware, often by masquerading as a legitimate or necessary program. Once the adware is installed, it can start causing various issues on the Mac.
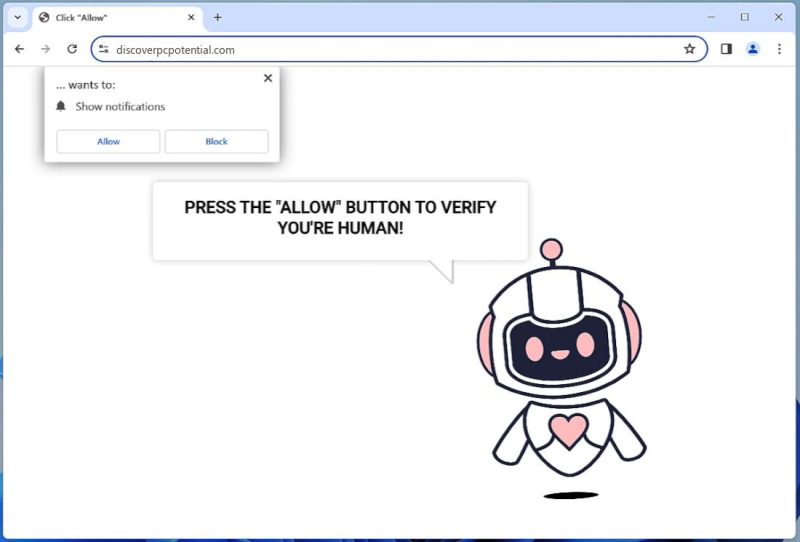
How to remove Discoverpcpotential.com
Discoverpcpotential.com is a potentially unwanted program (PUP) or a browser hijacker, typically considered as adware, that can infiltrate a computer system without the user’s knowledge. It often enters systems bundled with other freeware or shareware programs when users download them from the internet. Once installed, it can modify the browser settings, such as the default homepage or search engine, and introduce unwanted ads, redirects, or pop-ups. The software exploits browser notifications by triggering constant pop-up alerts that can interrupt a user’s browsing experience. These notifications often urge users to click on links or download additional software, potentially leading to further infections or data compromise. The most common browsers targeted by Discoverpcpotential.com include Internet Explorer, Firefox, and Chrome. It can infect a variety of devices, including Windows PCs, Macs, and even smartphones. The best defense against such PUPs is to maintain updated antivirus software and be vigilant while downloading free software from the internet.
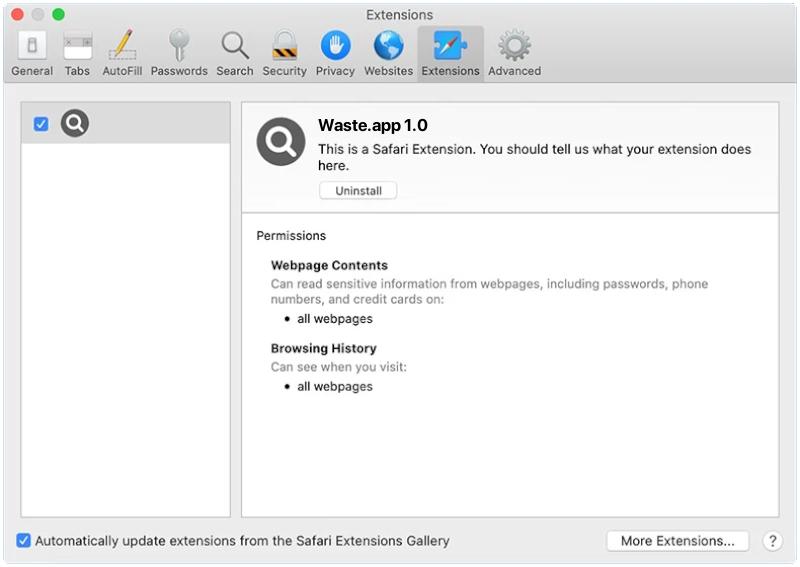
How to remove Waste.app (Mac)
Waste.app is a potentially unwanted program (PUP) or malware that is designed to infiltrate the Mac operating system and cause various issues. It often comes bundled with free software downloads or through deceptive pop-up ads. Once installed, Waste.app can cause a myriad of problems including slowing down the system, displaying unwanted ads, causing redirects to suspicious websites, and possibly even stealing sensitive information. Waste.app usually infects Mac systems through a deceptive technique known as “bundling”. This means it is often hidden within the installer of another program, particularly free software downloaded from the internet. Users might unknowingly install the Waste.app while installing the desired program. It can also be spread through malicious pop-up ads, fake software updates, or infected email attachments. Upon clicking or downloading these, the Waste.app gets installed and starts affecting the system’s performance and user’s data privacy.
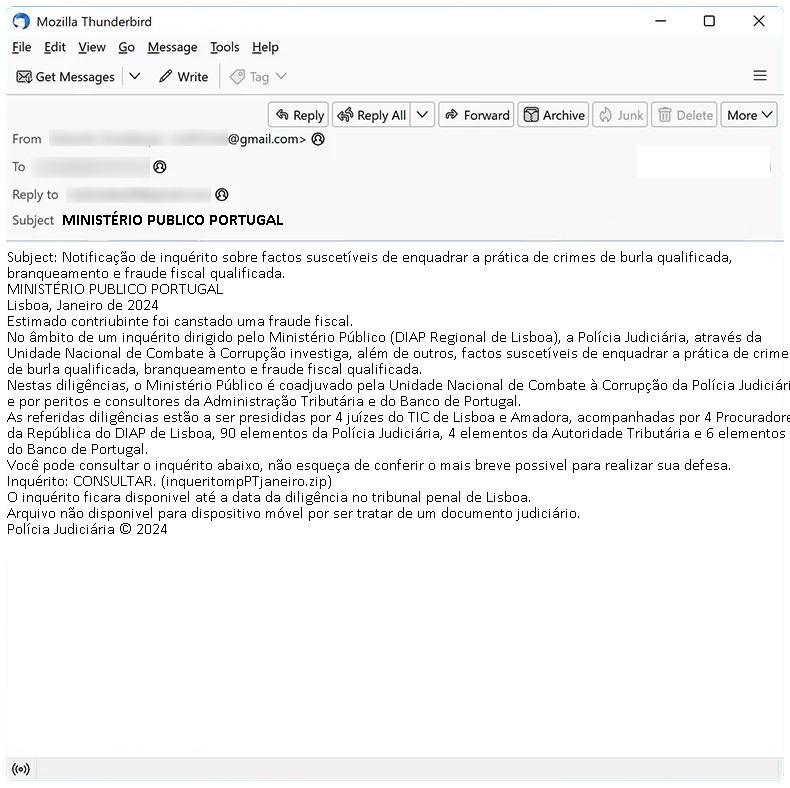
How to stop MINISTÉRIO PUBLICO PORTUGAL email scam
MINISTÉRIO PUBLICO PORTUGAL is the Public Prosecutor’s Office in Portugal. It is highly unlikely that the official MINISTÉRIO PUBLICO PORTUGAL would engage in email spam campaigns or scams. However, if you have received an email claiming to be from MINISTÉRIO PUBLICO PORTUGAL that seems suspicious, it is likely a phishing attempt or scam.
Phishing emails impersonate legitimate organizations to trick individuals into revealing personal information, such as login credentials or financial details. These emails often contain malicious links or attachments that, when clicked or downloaded, can infect computers with malware or ransomware.
Interacting with MINISTÉRIO PUBLICO PORTUGAL email scams can lead to several risks, including:
1. Data theft: Scammers may attempt to steal personal or financial information, which can be used for identity theft or financial fraud.
2. Malware infection: Clicking on links or downloading attachments from these emails can infect your computer with malware, allowing hackers to gain unauthorized access or control over your system.
3. Financial loss: In some cases, scammers may request payment or provide false information about outstanding fines or legal issues, leading to financial loss if individuals fall for the scam.
4. Privacy invasion: By interacting with such scams, you may inadvertently provide access to personal information or compromise your privacy.
To protect yourself from MINISTÉRIO PUBLICO PORTUGAL email scams or any other phishing attempts, it is important to:
1. Verify the sender: Check the email address and ensure it matches the official email format for MINISTÉRIO PUBLICO PORTUGAL or any other legitimate organization.
2. Be cautious of urgent or threatening language: Scammers often use fear tactics to pressure individuals into taking immediate action. Legitimate organizations usually communicate in a professional and respectful manner.
3. Avoid clicking on suspicious links or downloading attachments: Hover over links to see the actual URL before clicking, and only download files from trusted sources.
4. Keep your computer and antivirus software up to date: Regularly update your operating system and antivirus software to protect against known vulnerabilities and malware.
5. Educate yourself: Stay informed about common phishing techniques and scams to recognize and avoid them.
Remember, official entities like MINISTÉRIO PUBLICO PORTUGAL would not send unsolicited emails asking for personal information or requesting urgent actions. If you suspect an email to be a scam, it is advisable to report it to your local authorities or the official MINISTÉRIO PUBLICO PORTUGAL.
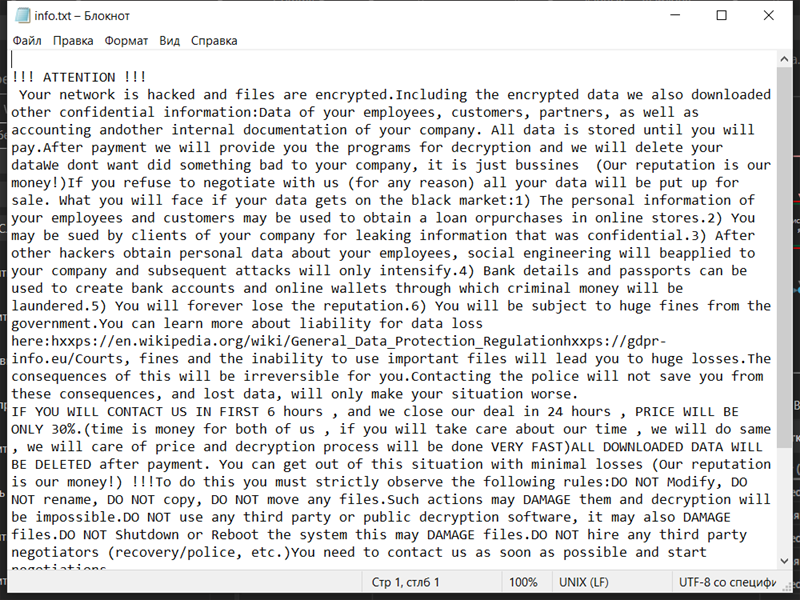
How to remove Gotmydatafast Ransomware and decrypt .gotmydatafast files
Gotmydatafast Ransomware is a type of malicious software that infects computers and encrypts files stored on the affected system. It is a variant of the Dharma/Crysis ransomware family. Here is some information about Gotmydatafast Ransomware:
1. Infection: Gotmydatafast Ransomware typically infects computers through various methods, including malicious email attachments, fake software updates, compromised websites, or by exploiting vulnerabilities in the system.
2. File Extensions: Once the ransomware infects a computer, it adds a unique extension to the encrypted files. The specific extension used by Gotmydatafast Ransomware may vary, but it commonly appends “.gotmydatafast” to the original file names.
3. File Encryption: Gotmydatafast Ransomware uses a strong encryption algorithm to lock the victim’s files, making them inaccessible. It typically targets a wide range of file types, including documents, images, videos, databases, archives, and more.
4. Ransom Note: After encrypting the files, Gotmydatafast Ransomware creates a ransom note that contains instructions on how to pay the ransom to get the files decrypted. This note is usually in the form of a text file or a pop-up message and can be found in various locations on the infected system, such as the desktop or folders containing encrypted files.
5. Decryption Tools: Unfortunately, there are currently no publicly available decryption tools specifically designed for Gotmydatafast Ransomware. It is generally not recommended to pay the ransom, as it does not guarantee that the cybercriminals will provide the decryption key.
6. Decrypting .gotmydatafast files: As of now, the only reliable way to decrypt the files encrypted by Gotmydatafast Ransomware is to restore them from a backup. If you have a backup of your important files stored on an external device or in the cloud, you can use it to recover your data after removing the ransomware from your system.
It is crucial to regularly back up your important files and keep your operating system and security software up to date to minimize the risk of ransomware infections. Additionally, practicing safe browsing habits and being cautious while opening email attachments or downloading files from untrusted sources can help prevent ransomware infections.
How to remove Mycool Search
Mycool Search is an adware program that infiltrates computers and browsers, causing unwanted advertisements and search redirects. It is designed to generate revenue for its developers by promoting various sponsored content and collecting user data for targeted advertising purposes. Once installed on a computer, Mycool Search modifies browser settings, such as the default search engine and homepage, to redirect users to its own search engine or affiliated websites.
Mycool Search primarily infects computers through software bundling, a technique in which it is bundled with free or pirated software that users download from unreliable sources. When users install such software without paying close attention to the installation process, they may unknowingly agree to install additional programs like Mycool Search. In some cases, the adware may also be distributed through malicious email attachments or infected websites. To avoid getting infected by Mycool Search, it is important to download software only from trusted sources and regularly update antivirus software to detect and remove any potential threats.
How to remove Extreme Security Adblocker
Extreme Security Adblocker is a type of adware that is known for causing intrusive and unwanted advertisements to appear on a user’s computer. This adware typically disguises itself as a legitimate browser extension or software program that claims to enhance the security of the user’s online browsing experience. However, once installed, Extreme Security Adblocker starts displaying excessive pop-up ads, banners, and other advertisements on websites that the user visits.
Extreme Security Adblocker primarily infects computers through deceptive methods such as bundling with freeware or shareware programs, or through malicious websites that trick users into downloading and installing the adware. It may also exploit vulnerabilities in outdated software or operating systems to gain unauthorized access to a user’s computer. Once installed, Extreme Security Adblocker modifies the browser settings and injects its own code into the webpages visited by the user, thereby displaying unwanted advertisements. This adware can significantly slow down the computer’s performance, disrupt the browsing experience, and pose a potential security risk by exposing users to malicious websites or content.
How to remove Personalized Notepad with Reminders
Personalized Notepad with Reminders is a seemingly harmless application that claims to enhance productivity and organization by providing users with a digital notepad and reminder system. It appears as a legitimate software solution, often offering customizable features to suit individual preferences. Users are enticed by the idea of an efficient and personalized note-taking tool, making them more susceptible to falling victim to this deceitful software. However, beneath its innocent facade, Personalized Notepad with Reminders harbors malicious intentions. Once installed on a computer, it gains unauthorized access to personal data, monitors online activities, and even modifies system settings without the user’s consent. It may also display intrusive advertisements or redirect users to suspicious websites, further compromising computer security and user privacy.
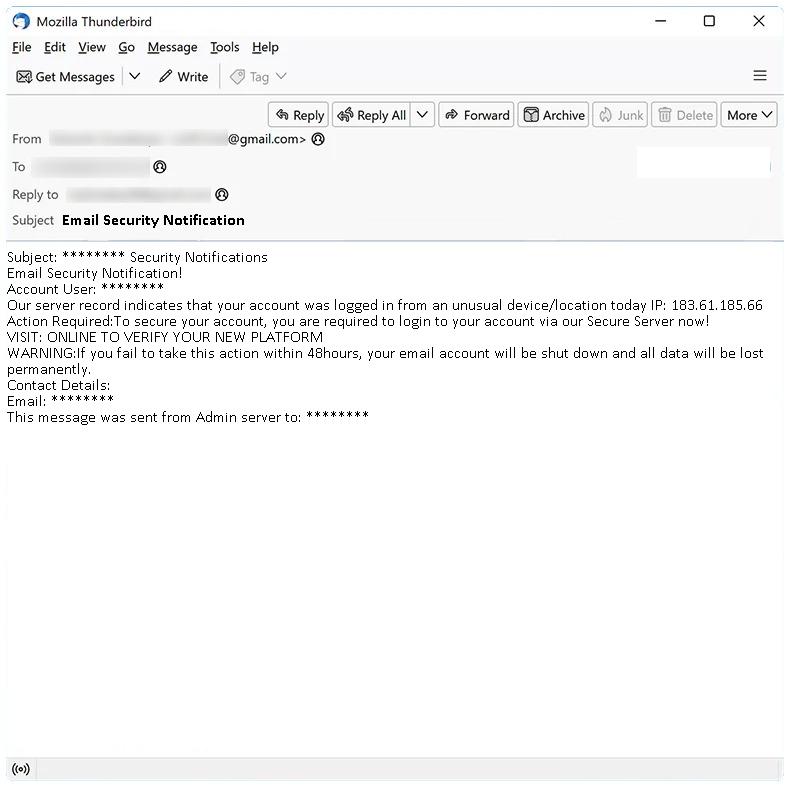
How to stop Email Security Notification email scam
Email Security Notification email spam refers to a type of phishing scam where cybercriminals send deceptive emails pretending to be from a legitimate email security service or provider. These emails typically notify the recipient about a supposed security breach, compromised account, or suspicious activity in their email account. The purpose of these scams is to trick users into divulging their login credentials, personal information, or install malware onto their computers.
Email Security Notification spam campaigns often employ various techniques to infect computers:
1. Phishing links: The email may contain a link that directs the user to a fake login page designed to steal their email credentials.
2. Malicious attachments: The email might include an attachment that, when opened, installs malware or ransomware onto the victim’s computer.
3. Social engineering: The email may employ psychological manipulation, urgency, or fear tactics to trick users into taking immediate action without thoroughly verifying the legitimacy of the email.
Interacting with Email Security Notification email scams can pose several risks:
1. Account compromise: If users fall for these scams and provide their login credentials, the attackers gain unauthorized access to their email accounts, potentially leading to identity theft, financial fraud, or unauthorized access to sensitive information.
2. Malware installation: Clicking on links or opening attachments in these emails can result in the installation of malware or ransomware, which can compromise the security and functionality of the victim’s computer.
3. Data loss: In some cases, scammers may trick users into providing personal information, such as social security numbers or credit card details, leading to potential financial loss or identity theft.
4. Further phishing attacks: If scammers gain access to an email account, they can use it to send more phishing emails to the victim’s contacts, spreading the scam further.
It is crucial to be cautious when encountering such emails and avoid interacting with them. Instead, users should independently verify the legitimacy of the email by contacting their email service provider directly or accessing their accounts through official websites or applications.