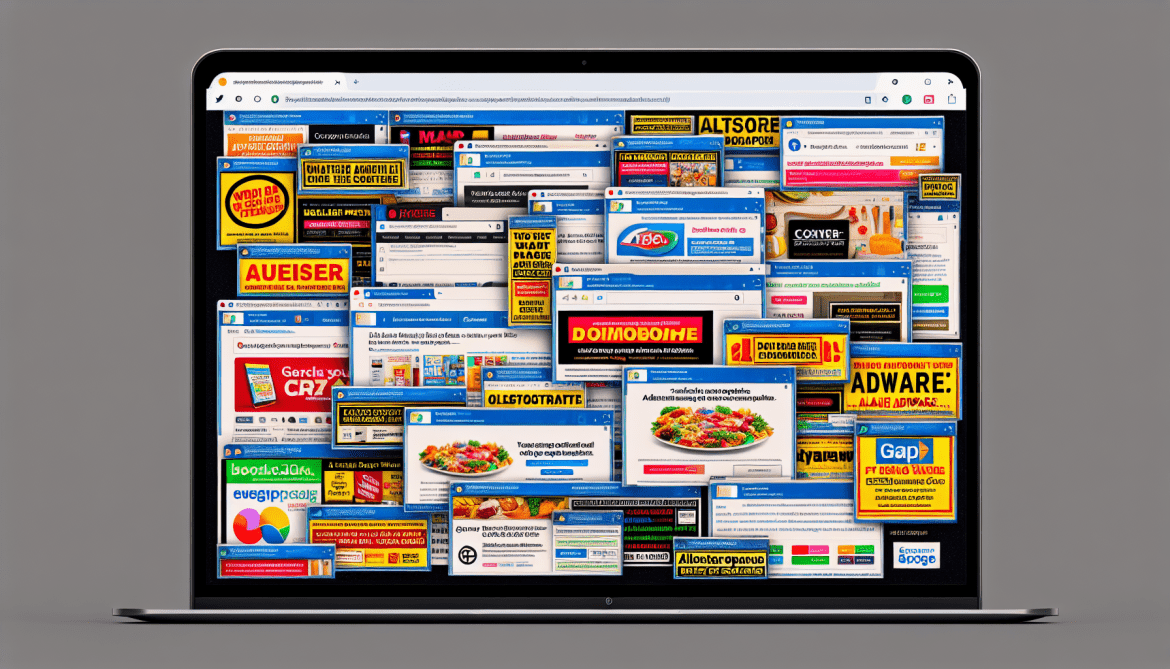
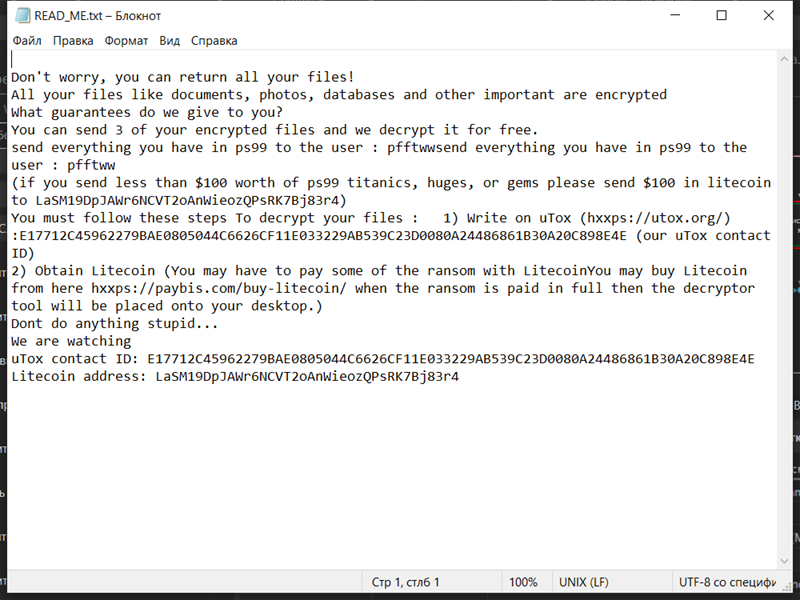
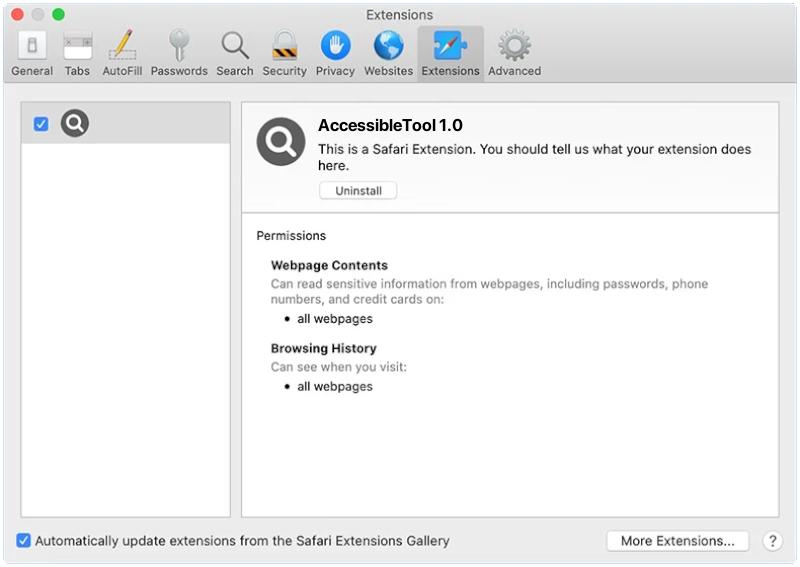
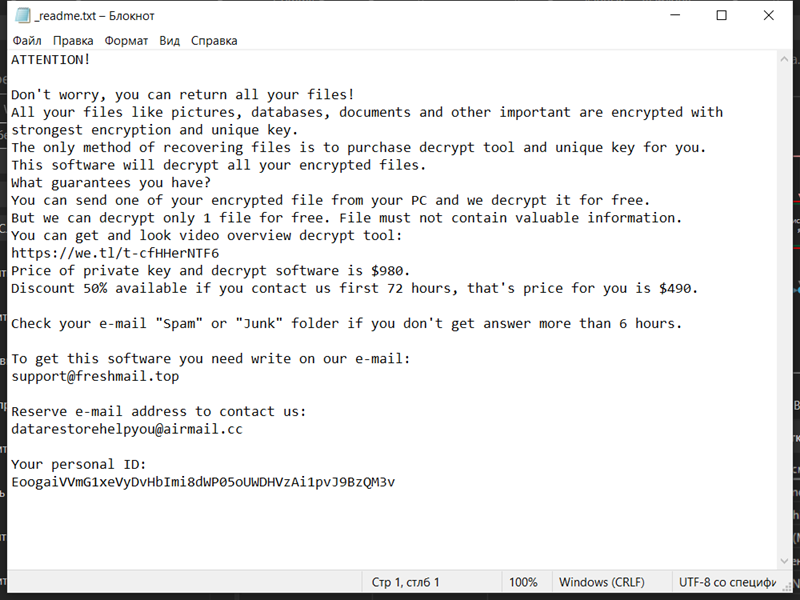
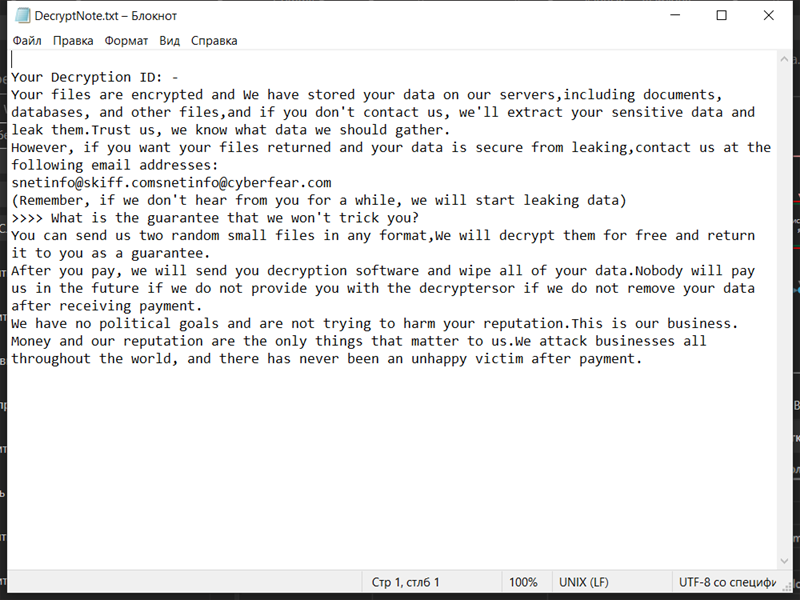
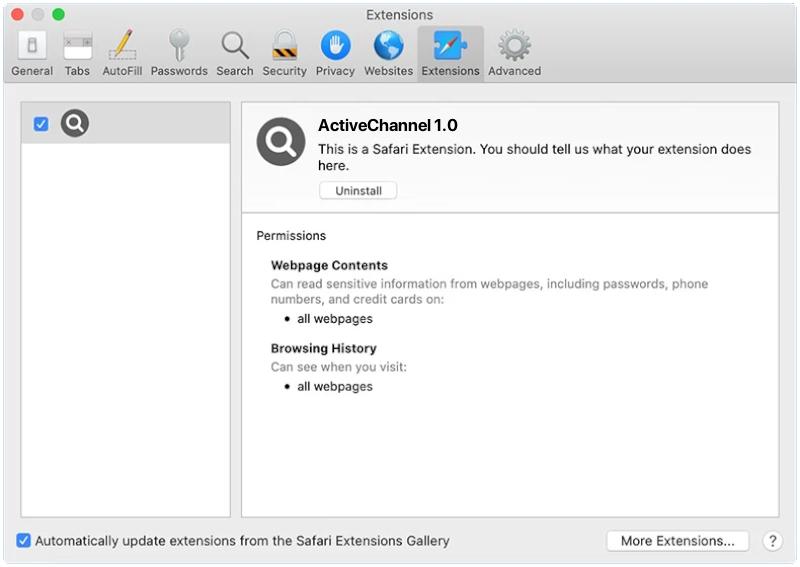
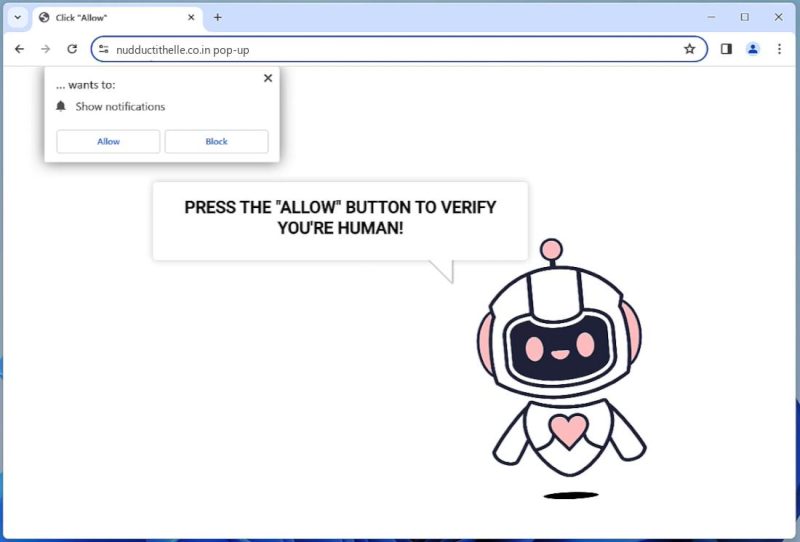
AltostratusOpacus is a type of adware that infects computers and displays unwanted advertisements to users. Adware, short for advertising-supported software, is a form of malicious software that generates revenue for its creators by displaying intrusive advertisements on infected devices.
AltostratusOpacus typically infects computers through various methods such as software bundling, malicious downloads, or by exploiting vulnerabilities in outdated software. It can also be distributed through deceptive advertising, where users are tricked into clicking on ads that install the adware onto their devices. Once installed, AltostratusOpacus starts displaying unwanted and often intrusive ads, pop-ups, banners, or even redirecting users to malicious websites. These advertisements are not only annoying but can also slow down the computer’s performance and compromise the user’s privacy and security.
To protect against AltostratusOpacus and similar adware, it is crucial to exercise caution when downloading software from the internet and to only use trusted sources. Keeping all software and applications up to date with the latest security patches can also help prevent vulnerabilities that adware may exploit. Additionally, using a reliable antivirus program and regularly scanning the computer for malware can help detect and remove any potential adware infections.