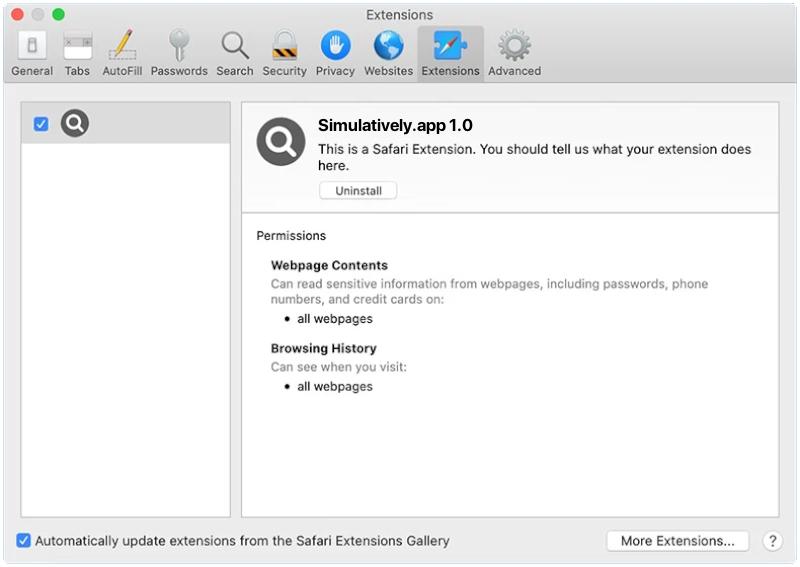
Simulatively.app is a potentially unwanted application (PUA) that often affects Mac users. This software is categorized as a PUA due to its deceptive distribution techniques and its tendency to infiltrate systems without the user’s explicit consent. Once installed, it can cause a variety of issues, including displaying intrusive advertisements, collecting personal data, and modifying browser settings. In some cases, this app can even lead to serious privacy issues or identity theft. Simulatively.app often infiltrates Mac systems through bundled software or deceptive advertisements. Users may unknowingly download and install this PUA when they install free software from unreliable sources, as it may be bundled within the installer. Additionally, clicking on suspicious pop-up ads or banners can also result in the installation of this app. Once inside the system, Simulatively.app starts its suspicious activities, which can significantly decrease system performance and compromise the user’s privacy.
Author: admin
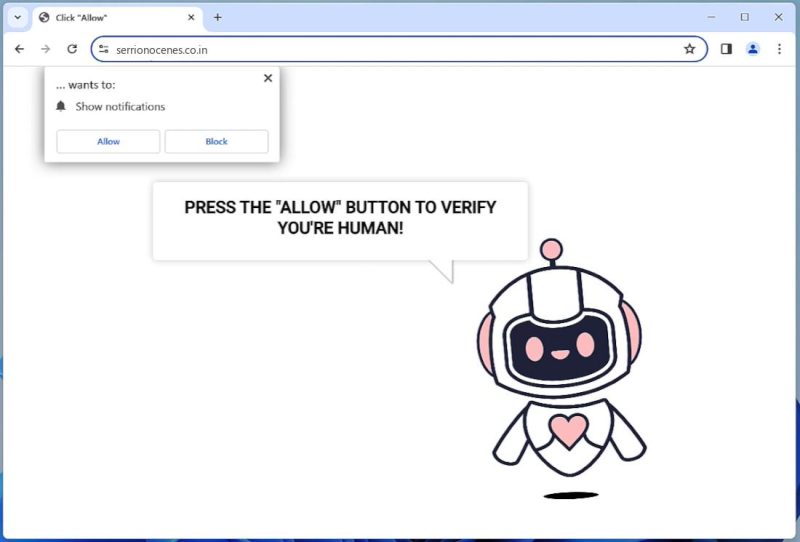
How to remove Serrionocenes.co.in
Serrionocenes.co.in is a potentially harmful website that is categorized as a browser hijacker or adware. It is designed to infiltrate computer systems without user’s consent, often bundled with free software downloaded from the internet. This malicious website targets web browsers, altering their settings to promote fake search engines. This site uses a deceptive method called “clickbait” to trick users into subscribing to its browser notifications. It often displays misleading pop-up ads or messages that entice users to click on them, leading to unwanted software downloads, data breaches, or exposure to harmful content. Serrionocenes.co.in can infect various browsers such as Google Chrome, Mozilla Firefox, Internet Explorer, and Safari, and has the capability to affect both Windows and Mac devices. Once it gains access to a device, it exploits browser notifications by sending unsolicited ads and pop-ups directly to the user’s desktop, even when the browser is not opened. These notifications may contain malicious links that, when clicked, can lead to further malware infections, identity theft, or financial loss. To avoid such threats, it is essential to keep your device’s security software updated and practice safe browsing habits.
How to remove Trojan:Win32/Suweezy
Trojan:Win32/Suweezy is a malicious software program identified as a trojan. Trojans are a type of malware that appear to be normal or desirable software, but once installed, they grant a hacker unauthorized access to the infected system. Trojan:Win32/Suweezy typically infects computers by disguising itself as a legitimate program or file that users are tricked into downloading and installing. It can also be delivered via email attachments, malicious websites, or bundled with other software. Once the trojan has been executed on a system, it can perform various harmful activities. These may include stealing sensitive data, installing more malware, modifying system settings, and even using the infected system to launch attacks on other computers. To protect against Trojan:Win32/Suweezy and other malware, it’s important to keep all software up-to-date, use a reliable antivirus solution, and avoid downloading files or clicking on links from unknown sources.
How to remove K Searches
K Searches adware is a form of malicious software that infects a user’s computer or browser, mainly for the purpose of generating unsolicited advertisements. This adware often disguises itself as a helpful tool, promising to enhance your browsing experience by providing better search results. However, once installed, it serves annoying pop-up ads, redirects users to suspicious websites, and may even collect sensitive data such as browsing history and personal information, which can lead to privacy issues. K Searches can infect computers and browsers through various methods. The most common way is through bundled software. When users download free software from untrusted sources, the adware can be included within the software package and gets installed unknowingly by the user. It can also infect browsers through deceptive pop-up ads or compromised websites. Once clicked, these ads or websites can automatically download and install the adware onto the user’s system. Additionally, K Searches can also spread via email attachments or infected USB drives.
How to remove StartnSearch Search
StartnSearch is a potentially unwanted program (PUP) that primarily targets web browsers. It is classified as adware due to its primary function of generating intrusive advertisements and modifying browser settings without the user’s consent. This adware typically alters the default search engine, new tab URL, and homepage to StartnSearch Search. Its main aim is to generate revenue by redirecting users to affiliated or sponsored websites, usually filled with intrusive ads. StartnSearch Search adware usually infiltrates computers through bundled software packages or deceptive pop-up ads. Users often unknowingly download and install such adware when they install freeware or shareware applications from unreliable sources, without carefully reading the terms and conditions. Once installed, the adware can potentially track user’s online activities, collect personal data, and expose the system to other malware or security risks. To avoid such infections, it is crucial to install a reliable antivirus program and always choose the custom or advanced installation options when downloading and installing software.
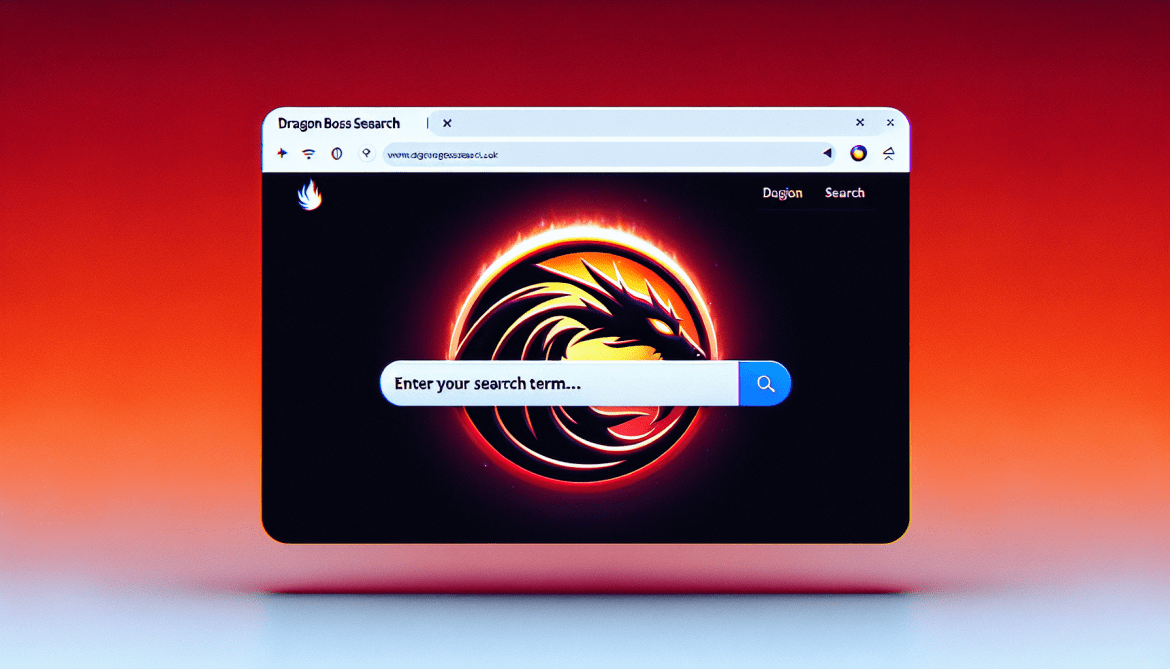
How to remove Dragon Boss Search
Dragon Boss Search is a type of adware, which is a software application that displays unwanted advertisements on a user’s computer. It is designed to generate revenue for its developers by showing pop-up ads, banners, and other types of online advertisements, often leading to potentially dangerous websites. This adware hijacks the user’s browser settings, changing the default homepage and search engine to Dragon Boss Search without the user’s consent. It also tracks browsing data, gathering information about the user’s online activities and preferences. Dragon Boss Search typically infects computers and browsers through bundled software, where it is hidden within the installation process of other free software downloaded from the internet. Users often unknowingly install the adware while installing the desired program. It can also infect systems through malicious email attachments, fake software updates, or by visiting infected websites. Once installed, it can be difficult to remove as it embeds itself deeply into the system and browser settings. Therefore, users are advised to pay close attention during software installation processes and to keep their antivirus software updated.
How to remove Lomx Ransomware and decrypt .lomx files
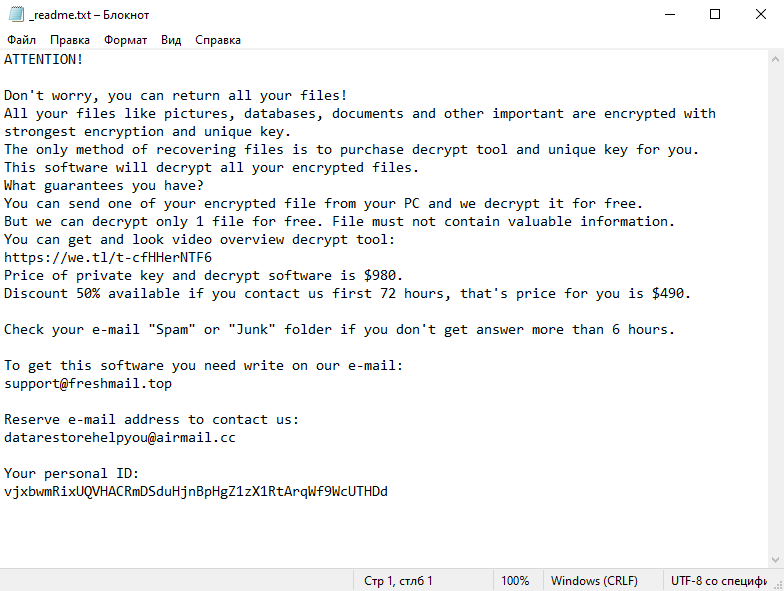
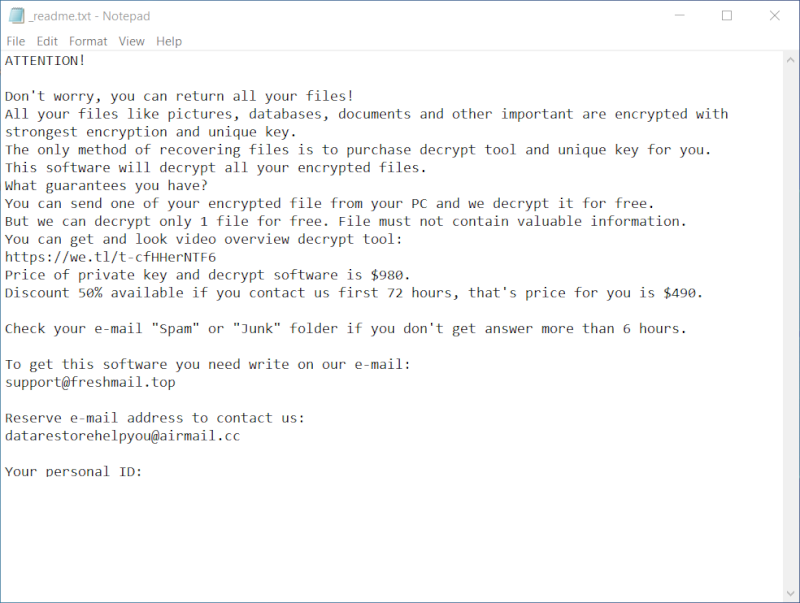
paid. The Lomx ransomware is classified as a member of the STOP/Djvu ransomware family. The infection process can occur through various ways such as visiting malicious websites, downloading infected files or software, opening suspicious emails and attachments, or through peer-to-peer file sharing. Once the Lomx ransomware infects a computer, it scans for various file types such as documents, images, videos, and more, and encrypts them using a strong encryption algorithm. After the encryption process, it appends the .lomx extension to the affected files. For instance, a file originally named ‘photo.jpg’ would be renamed to ‘photo.jpg.lomx’. The Lomx ransomware then creates a ransom note in a text file typically named _readme.txt, which is usually placed in every folder containing the encrypted files. This note contains information about the encryption and demands a ransom payment (usually in Bitcoin) in exchange for a decryption key.
How to remove Cdmx Ransomware and decrypt .cdmx files
Cdmx Ransomware is a type of malicious software that is part of the Djvu/STOP Ransomware family. It’s designed to infiltrate computer systems and encrypt users’ files, making them inaccessible until a ransom is paid.
Infection Method:
Cdmx Ransomware often infects computers via spam emails, malicious advertisements, or compromised websites. It can also infiltrate a system through unpatched software vulnerabilities or weak passwords.
File Extensions and Encryption:
Once installed, the ransomware scans and encrypts a wide range of file types, such as documents, images, videos, music, etc. It typically appends a unique extension, .cdmx, to the end of each encrypted file’s name, indicating that the file has been encrypted. The encryption method used by Cdmx Ransomware is typically AES-256, a robust and secure encryption algorithm.
Ransom Note:
After the encryption process, Cdmx Ransomware generates a ransom note, typically named _readme.txt. The note contains information about the encryption and instructions on how to pay the ransom to get the decryption key. It’s usually placed in every folder that contains encrypted files.
Decryption Tools:
As of now, there are no specific decryption tools designed for Cdmx Ransomware. However, Emsisoft has developed a decryption tool for the STOP Djvu family, which Cdmx Ransomware is a part of. The tool may not always work, especially if the ransomware used an online key for the encryption, but it’s worth trying.
How to Decrypt Files:
To decrypt the encrypted files, you would need the decryption tool and the unique decryption key, which is typically held by the attackers. When using the Emsisoft STOP Djvu decryptor, you must download and run the tool, then follow the on-screen instructions. However, it’s important to remove the ransomware from your system first to prevent further encryption.
Keep in mind that paying the ransom is not recommended, as there is no guarantee the attackers will provide the decryption key. It’s always best to keep regular backups of your important files to prevent data loss from such attacks.
How to remove Trojan.Win64.Encoder
Trojan.Win64.Encoder is a type of malicious software, specifically a Trojan horse, that primarily targets Windows 64-bit operating systems. Its main purpose is to infiltrate a user’s computer without their knowledge or consent and perform various harmful activities. The Trojan.Win64.Encoder is often camouflaged as a legitimate file or software to deceive users into downloading and installing it. It can also be embedded in email attachments, software updates, or distributed through malicious websites. Once installed, it can gain control over the system by modifying system settings, disabling antivirus software, and opening backdoors for further infections. The Trojan.Win64.Encoder is particularly known for its data encoding or encryption capabilities. After infecting a system, it can encrypt files and data stored on the computer, making them inaccessible to the user. Typically, a ransom message is then displayed, demanding payment from the victim to decrypt and restore access to the files. This kind of malicious activity is commonly referred to as ransomware. As with other types of malware, prevention is the best way to protect against Trojan.Win64.Encoder. This includes maintaining up-to-date antivirus software, being careful when downloading or installing new software, and avoiding suspicious websites and emails.
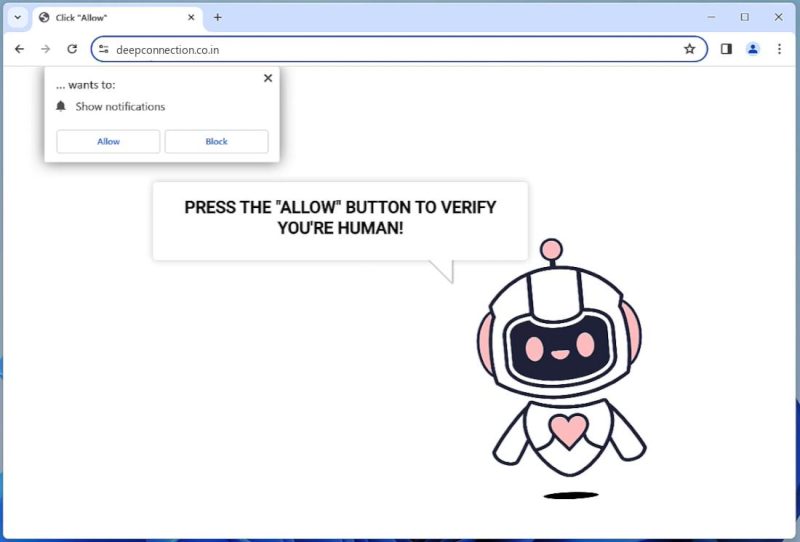
How to remove Deepconnection.co.in
Deepconnection.co.in is a potentially unwanted program (PUP) or a browser hijacker that tends to infiltrate computers without the users’ knowledge. It usually comes bundled with free software downloads or through deceptive advertising. Once installed, it modifies browser settings to promote its fake search engine and generate intrusive advertisements. This PUP is also known for collecting user data such as browsing history, search queries, and personal details that could compromise user privacy. Deepconnection.co.in exploits browser notifications by tricking users into enabling them. It displays a pop-up message asking users to allow notifications to continue using the website or to access its content. Once allowed, it starts sending unwanted ads, links to malicious sites, or even malware directly to the user’s desktop. It can infect all major browsers, including Google Chrome, Mozilla Firefox, and Safari, and is not limited to any specific devices, meaning it can affect both PCs and mobile devices. The best way to prevent such infections is by practicing safe browsing habits and regularly updating and scanning your device with a reputable antivirus software.