What is Lomx Ransomware
Lomx is a type of ransomware, a malicious software that infects computers and encrypts user files, making them inaccessible until a ransom is paid. The Lomx ransomware is classified as a member of the STOP/Djvu ransomware family. The infection process can occur through various ways such as visiting malicious websites, downloading infected files or software, opening suspicious emails and attachments, or through peer-to-peer file sharing. Once the Lomx ransomware infects a computer, it scans for various file types such as documents, images, videos, and more, and encrypts them using a strong encryption algorithm. After the encryption process, it appends the .lomx extension to the affected files. For instance, a file originally named ‘photo.jpg’ would be renamed to ‘photo.jpg.lomx’. The Lomx ransomware then creates a ransom note in a text file typically named _readme.txt, which is usually placed in every folder containing the encrypted files. This note contains information about the encryption and demands a ransom payment (usually in Bitcoin) in exchange for a decryption key.
As of now, complete decryption for the Lomx ransomware is typically not possible without obtaining the unique key from the criminals. However, security companies like Emsisoft have created a ‘STOP Djvu Decryptor’ tool, which can decrypt some versions of the STOP/Djvu ransomware. Its effectiveness depends on whether the files were encrypted using an ‘online’ or ‘offline’ key. If an ‘offline’ key was used and Emsisoft has that specific key in their database, then decryption is possible. To decrypt ‘.lomx’ files using the Emsisoft’s STOP Djvu Decryptor, you would need to download and run the decryptor tool on your computer. Upon launching it, you will be asked to agree to the terms and conditions before you can use the tool. Then, you will need to add the directory of the encrypted files and the tool will start the decryption process. Remember, it’s always best to protect your computer from ransomware by keeping your software updated, using reliable antivirus software, and avoiding suspicious emails, websites, and downloads. In addition, regularly backing up your important files can also help to minimize the potential damage caused by ransomware.
You can not trust scammers and pay money without a guarantee of receiving files. The most effective way to get your files back is to remove Lomx Ransomware to prevent infection. There are 2 options for solving this problem. The first is to use an automatic removal utility that will remove the threat and all instances related to it. Moreover, it will save you time. Or you can use the Manual Removal Guide, but you should know that it might be very difficult to remove Lomx Ransomware manually without a specialist’s help. If for any reason you need to recover deleted or lost files, then check out our article Top 5 Deleted File Recovery Software
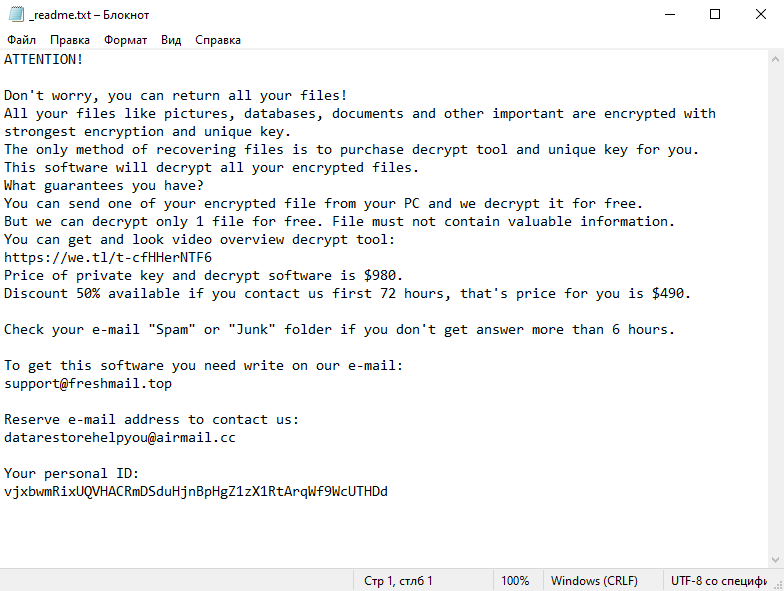
Contents of the ransom note:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-cfHHerNTF6
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
support@freshmail.top
Reserve e-mail address to contact us:
datarestorehelpyou@airmail.cc
Your personal ID: -
Lomx Ransomware Removal Guide

Remember that you need to remove Lomx Ransomware first and foremost to prevent further encryption of your files before the state of your data becomes totally useless. And only after that, you can start recovering your files. Removal must be performed according to the following steps:
Download Lomx Ransomware Removal Tool
SpyHunter 5 is a powerful malware detection and removal tool developed by EnigmaSoft Limited. It’s designed to provide robust protection against a wide range of malware threats, including viruses, trojans, worms, rootkits, and ransomware. SpyHunter 5 is particularly known for its effectiveness in dealing with complex and evolving malware types that traditional antivirus programs may struggle to detect.
Manual Lomx Ransomware Removal Guide
Here are step-by-step instructions to remove Lomx Ransomware from Windows. Follow these steps carefully and remove files and folders belonging to Lomx Ransomware. Firstly, you need to run the system in a Safe Mode. Then find and remove needed files and folders.
Lomx Ransomware files:
{randomname}.exe, _readme.txt
Clean up hosts file to access security websites
Cleaning up the “hosts” file from unwanted entries involves a few steps. The “hosts” file is a system file used by an operating system to map hostnames to IP addresses. Often, viruses add entries to block popular antivirus websites. It’s important to be cautious when editing this file, as incorrect modifications can cause network issues. Here’s a general guide on how to clean it up:
- Open Notepad as an Administrator:
- Type ‘Notepad’ in the search bar.
- Right-click on the Notepad app and select ‘Run as administrator’.
- Open the Hosts File in Notepad:
- In Notepad, go to File > Open.
- Navigate to
C:\Windows\System32\drivers\etc. - Select “All Files” from the drop-down menu next to the filename text box.
- Open the “hosts” file.
- Edit the File:
- Locate any unwanted entries. These are typically at the bottom of the file.
- Remove or comment them out by adding a
#at the beginning of the line.
- Save Your Changes:
- Go to File > Save.
- Close Notepad.
Check for malicious processes on Windows
Checking for malicious processes in Windows involves a few steps and the use of some tools. While some basic checks can be done manually, for a more thorough examination, specialized software is often required. Here’s a guide to help you get started:
- Task Manager:
- Press
Ctrl + Shift + Escto open Task Manager. - Go to the Processes tab.
- Look for any unusual or unfamiliar processes, especially those using high CPU or memory.
- Right-click on a suspicious process and select Open file location to investigate further.
- Press
- Resource Monitor:
- Access Resource Monitor by typing Resource Monitor in the Start menu search bar.
- Check the Overview or CPU tab for suspicious activities.
Remove unwanted startup entries
- Open System Configuration:
- Press
Windows Key + Rto open the Run dialog box. - Type
msconfigand press Enter. This opens the System Configuration window.
- Press
- Navigate to the Startup Tab:
- In the System Configuration window, go to the Startup tab.
- Note: In Windows 10 and later, you might be redirected to the Task Manager for managing startup items.
- Disable Unwanted Startup Programs:
- If within System Configuration, uncheck the boxes next to the programs you want to disable.
- If in Task Manager, select the program and click Disable.
- Apply Changes and Restart:
- Click OK or Apply to save your changes.
- Restart your computer if prompted.
How to decrypt .lomx files
Decrypt files using STOP Djvu Decryptor from Emsisoft
Before proceeding, it’s important to note that this decryptor works only for files encrypted by the STOP Djvu ransomware and only if they were encrypted using an offline key that the decryptor has. Here’s how to use the STOP Djvu Decryptor:
- Go to the Emsisoft website and download the STOP Djvu Decryptor.
- Find and open the downloaded file.
- Read and agree to the terms and conditions when prompted.
- Use the tool to select the encrypted files you want to decrypt.
- Click the button to begin the decryption process.
- Allow the decryptor to complete the process.
- Review which files were successfully decrypted.
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
Stellar Data Recovery is able to find and restore different types of encrypted files, including removed emails.
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Use Windows Previous Versions or Shadow Explorer to recover .lomx files
Using Windows Previous Versions and Shadow Explorer to restore files is a valuable technique, especially when dealing with accidental deletions or file corruptions. It can also be helpful in case of ransomware infections. Here’s how to use each feature:
Using Windows Previous Versions
- Find the File or Folder:
- Right-click on the file or folder you want to restore.
- Select Properties from the context menu.
- Access Previous Versions:
- In the Properties dialog, go to the Previous Versions tab.
- You’ll see a list of available previous versions from restore points or File History backups.
- Restore the File or Folder:
- Select the version you want to restore.
- Click Restore to overwrite the current version, or Copy to place it in a different location.
Using Shadow Explorer
- Download and Install Shadow Explorer:
- Download Shadow Explorer from its official website.
- Install and open the application.
- Select the Volume and Date:
- At the top of the Shadow Explorer window, select the desired drive (volume).
- Choose the date of the shadow copy you want to explore.
- Navigate and Restore Files:
- Navigate through the file system as in Windows Explorer.
- Right-click on the file or folder you wish to restore.
- Select Export and choose where to save the restored file.
How to prevent Lomx Ransomware infection?
Use G-DATA STOP/Djvu Vaccine
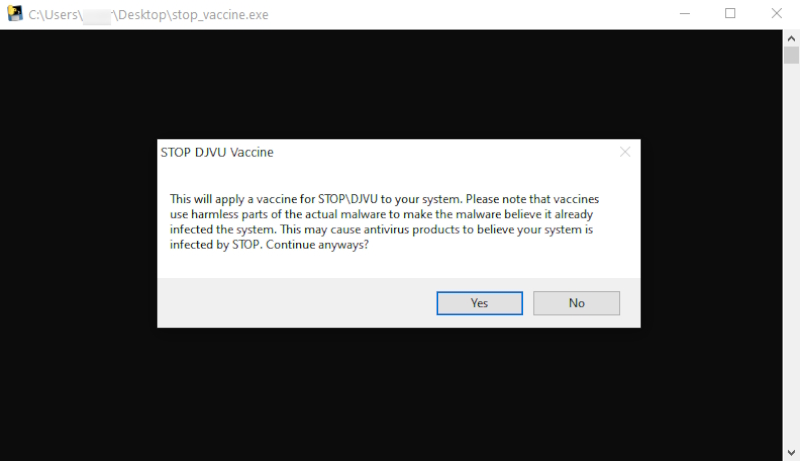
Using the G-DATA STOP/Djvu Vaccine is a preventative measure to protect against certain types of ransomware, specifically the STOP (Djvu) ransomware family. This tool doesn’t decrypt files that have already been encrypted but rather prevents the encryption from happening in the first place. Here are the steps to use it:
- Go to the official G-DATA website and download the STOP/Djvu Vaccine tool.
- Open the downloaded installer file and follow the on-screen instructions to install.
- Launch the G-DATA STOP/Djvu Vaccine program, allowing administrative privileges if prompted.
- Ensure the protection feature is active once the program is running.
- Check for updates regularly to protect against the latest ransomware variants.
- Watch for any notifications or logs from the vaccine to stay informed about ransomware activities.
Get antivirus protection
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
SpyHunter is a reliable antimalware removal tool application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.
