Pua:Win32/Fusioncore is a potentially unwanted application (PUA) that is categorized as malicious software or malware by Windows Defender and other antivirus software. It’s not as harmful as a virus or ransomware, but it can still pose a threat to your computer’s security and your personal data. Pua:Win32/Fusioncore often comes bundled with free software downloads from the internet. It usually infects computers when users download and install free software without carefully reading the terms and conditions. The PUA is hidden within the software installer and gets installed alongside the desired program without the user’s knowledge. Once installed, Pua:Win32/Fusioncore can cause various problems. It may slow down your computer, display annoying advertisements, or even change your browser settings. It can also potentially collect your personal information and send it to third parties. To avoid getting infected by Pua:Win32/Fusioncore or similar PUAs, it’s crucial to only download software from trusted sources, pay attention during the installation process, and regularly update and run your antivirus software.
Author: admin
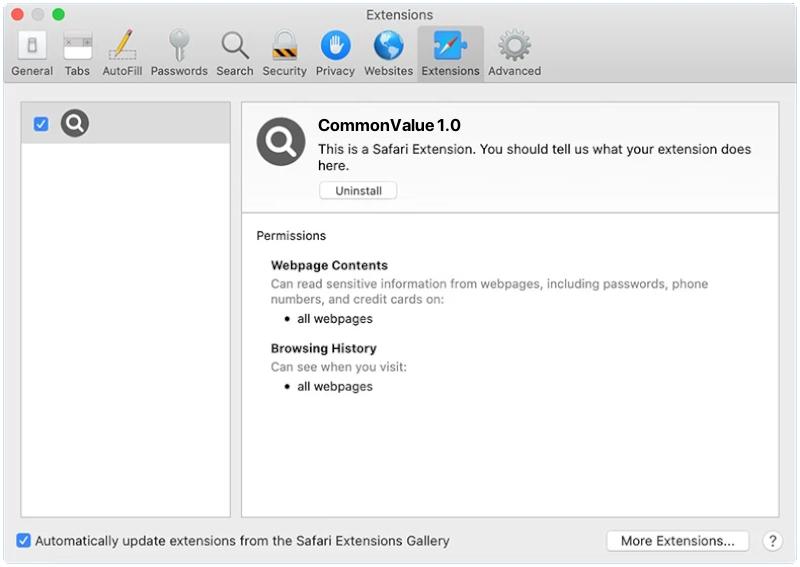
How to remove CommonValue (Mac)
CommonValue is a type of adware that targets Mac systems. It is a potentially unwanted program (PUP) that infiltrates systems without the user’s consent and initiates various system modifications, typically changing browser settings to promote fake search engines. CommonValue is also known for displaying intrusive ads and collecting browsing-related data, which could lead to serious privacy issues or even identity theft. Users often unknowingly download and install CommonValue when it is bundled with other software or hidden in the advanced settings of free software installation processes.
The infection process of CommonValue in Mac usually starts when a user downloads freeware or shareware that has this adware bundled into it. It can also infiltrate the system through deceptive pop-up ads or fake alerts prompting users to update an application. Once installed, it typically starts to make unwanted changes to the browser settings, replacing the default search engine, homepage, and new tab URL with its own. It causes numerous pop-up ads, banners, and redirects, leading to unwanted pages. Additionally, CommonValue can collect personal data about the user’s browsing habits, potentially leading to privacy issues.
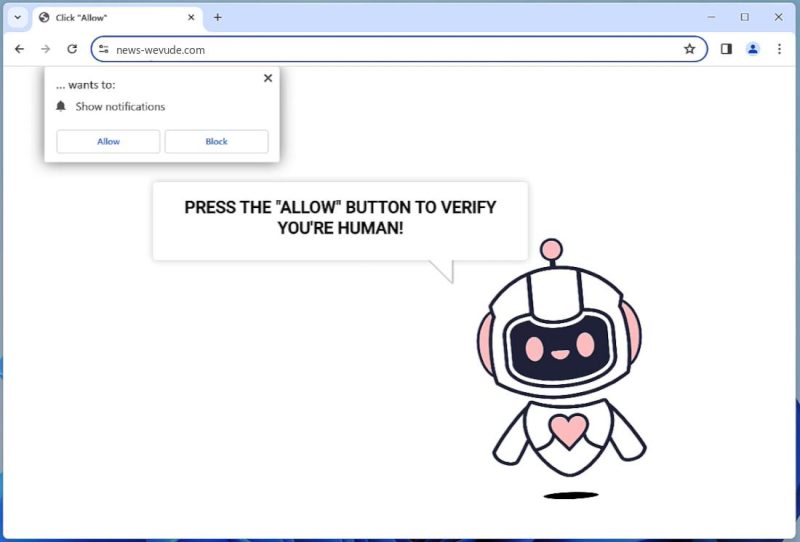
How to remove News-wevude.com
News-wevude.com is a potentially harmful website that is typically categorized as a browser hijacker or adware. It is infamous for its stealthy infiltration methods, often sneaking into a computer system without the user’s knowledge or consent. News-wevude.com primarily infects computers through bundled software, deceptive ads, or infected websites. Once in the system, it modifies browser settings, changes the default search engine, and triggers unwanted pop-up ads and redirects.
The website exploits browser notifications by tricking users into allowing them. It typically displays a prompt asking users to confirm that they are not a robot, and when the user clicks ‘Allow’, they inadvertently agree to receive push notifications from News-wevude.com. These notifications can be intrusive and may contain links to malicious sites. The browsers commonly affected by News-wevude.com include Google Chrome, Mozilla Firefox, and Internet Explorer. It can infect devices running on major operating systems including Windows, macOS, and even Android.
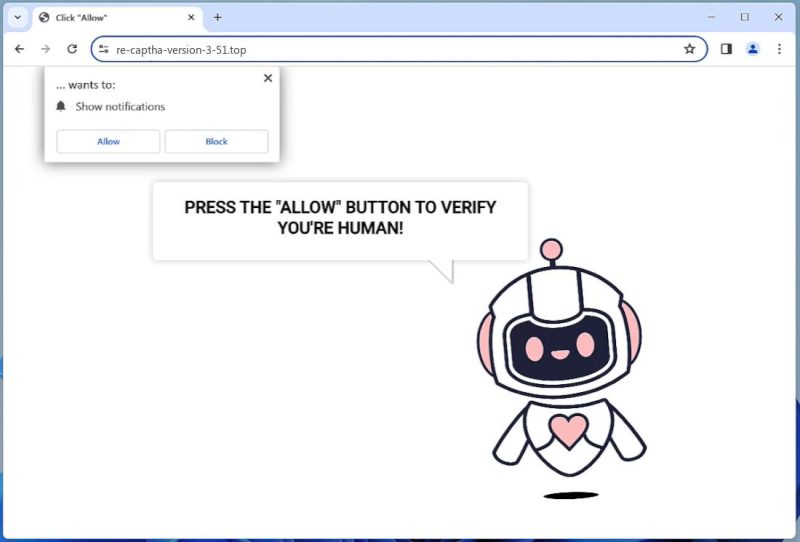
How to remove Re-captha-version-3-51.top
Re-captha-version-3-51.top is a form of malware, typically characterized as a browser hijacker. It is known for infecting computers by deceiving users into subscribing to its push notifications, so that it can send unwanted advertisements directly to the desktop. This is usually done by tricking users into believing they’re passing a bot detection test, in which they’re prompted to click a button to prove they’re not a robot. After the user clicks, the malware gains permission to send push notifications.
The Re-captha-version-3-51.top malware exploits browser notifications to deliver intrusive advertisements and potentially harmful links. These notifications can be disruptive and could lead to further malware infections if users click on them. The malware typically affects popular browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge. It can infect various devices, including computers, smartphones, and tablets, regardless of the operating system.
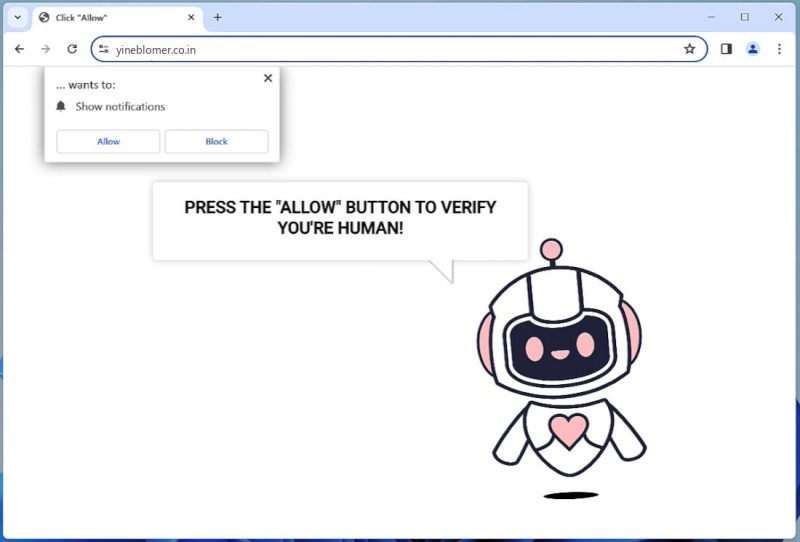
How to remove Yineblomer.co.in
Yineblomer.co.in is a deceptive website known for spreading potentially unwanted programs (PUPs) and initiating unauthorized changes to browser settings. It typically infiltrates computers through freeware installations, spam emails, and malicious websites. Once inside, it exploits browser notifications to display intrusive pop-ups, ads, and other unwanted content. It encourages users to click on “Allow” button to show notifications, after which it starts to flood the computer with various ads and even redirects users to dubious sites.
Yineblomer.co.in can infect all popular browsers, including Google Chrome, Mozilla Firefox, Internet Explorer, Safari, and others, spreading across different operating systems such as Windows, macOS, and even mobile platforms like Android and iOS. Therefore, all devices using these browsers and operating systems are susceptible to this invasive behavior. Its primary aim is to generate revenue through ad clicks and traffic redirection, often compromising user privacy and system security in the process.
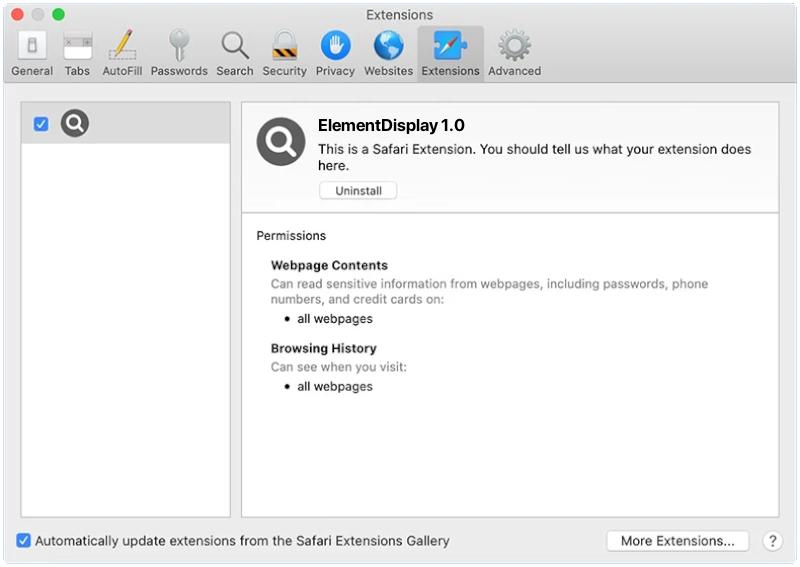
How to remove ElementDisplay (Mac)
ElementDisplay is a type of adware that specifically targets Mac users. It is a potentially unwanted program (PUP) that infiltrates the system without the user’s notice and starts delivering intrusive advertisements. This adware tends to change the browser’s settings to promote fake search engines and can lead to serious privacy issues or even identity theft. It can significantly diminish the performance of the device, causing it to slow down or freeze.
ElementDisplay typically infects a Mac through bundling, a technique where the unwanted software is hidden in the custom/advanced settings of the regular software. Users often rush through the installation process without noticing the additional downloads. Once installed, it begins to display pop-up ads, banners, and sponsored links in your web browser, and these ads are often very difficult to close. It can also redirect you to potentially harmful websites, collect personal data, or even download other malware onto your device.
How to remove S3rch.com
S3rch.com adware is a type of potentially unwanted program (PUP) that targets computer systems and web browsers. As an adware, it primarily exhibits intrusive advertising behavior, such as displaying pop-up ads, banners, and sponsored links within web pages. This adware could also redirect your search queries to its own search engine or other dubious websites. In addition, it may collect personal data about the user, like search queries and browsing history, which can be used for targeted advertising or sold to third parties.
S3rch.com typically infects computers and browsers through deceptive distribution methods, such as bundling. It is often packaged with free software downloaded from the internet, and users unknowingly install the adware when they install the primary software. Other times, it may be disguised as a legitimate extension or add-on for your web browser. In some cases, users may be tricked into downloading the adware through misleading advertisements or fake software updates. Once installed, it can affect the performance of your computer and significantly degrade your browsing experience.
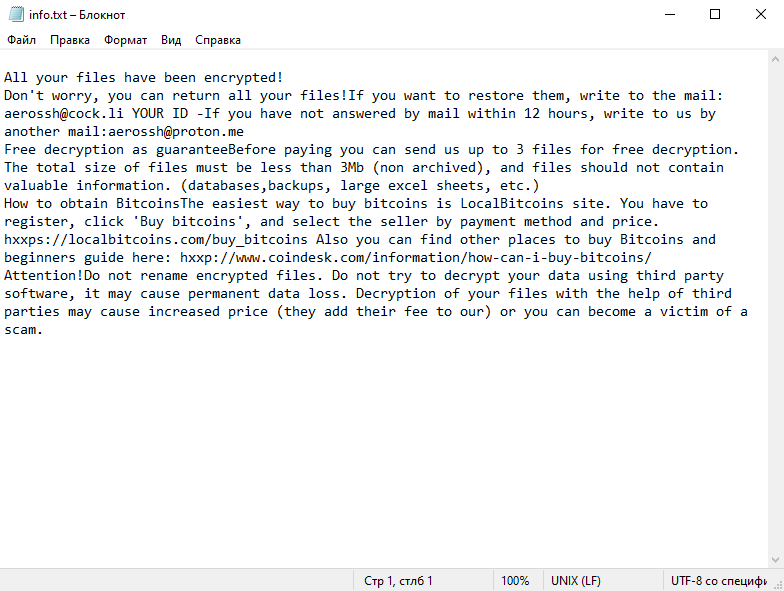
How to remove AeR Ransomware and decrypt .aer files
AeR Ransomware is a type of malicious software that infects computers, encrypts the user’s files, and then demands a ransom payment to restore access to these files. This type of malware is often spread through spam emails, malicious downloads, or infected websites.
Once installed, AeR Ransomware starts scanning the computer for files to encrypt. It typically targets a wide range of file types, such as documents, images, videos, databases, etc. The exact file extensions it adds to the encrypted files can vary, but it typically uses a custom extension related to the ransomware name (like .aer or .locked).
The encryption method used by AeR Ransomware is typically RSA or AES encryption, which are very secure encryption algorithms. This makes it difficult, if not impossible, to decrypt the files without the unique decryption key held by the cybercriminals.
After the encryption process is completed, AeR Ransomware generates a ransom note, usually in the form of a text file or a pop-up window. This note provides instructions on how to pay the ransom, usually in Bitcoin, and promises to provide the decryption key upon payment.
As of now, there’s no guaranteed decryption tool available for AeR Ransomware. Cybersecurity companies and independent researchers are constantly working on developing decryption tools for various types of ransomware, but the success rate varies greatly.
Decrypting .aer files (where .aer is the extension added by the ransomware) is not straightforward. If a decryption tool is not available, the victim has few options:
1. Restore files from a backup: If the user has a recent backup of their files, they can restore them after removing the ransomware from their system.
2. Try using a file recovery tool: In some cases, file recovery tools may be able to restore some of the original files.
3. Negotiate with the cybercriminals: While not recommended, as it encourages more attacks and there’s no guarantee the criminals will provide the decryption key even after payment.
In all cases, it’s important to first remove the ransomware from the system using a reliable antivirus or antimalware tool to prevent further file encryption. Users should also keep their systems updated and avoid suspicious emails or websites to reduce the risk of infection.
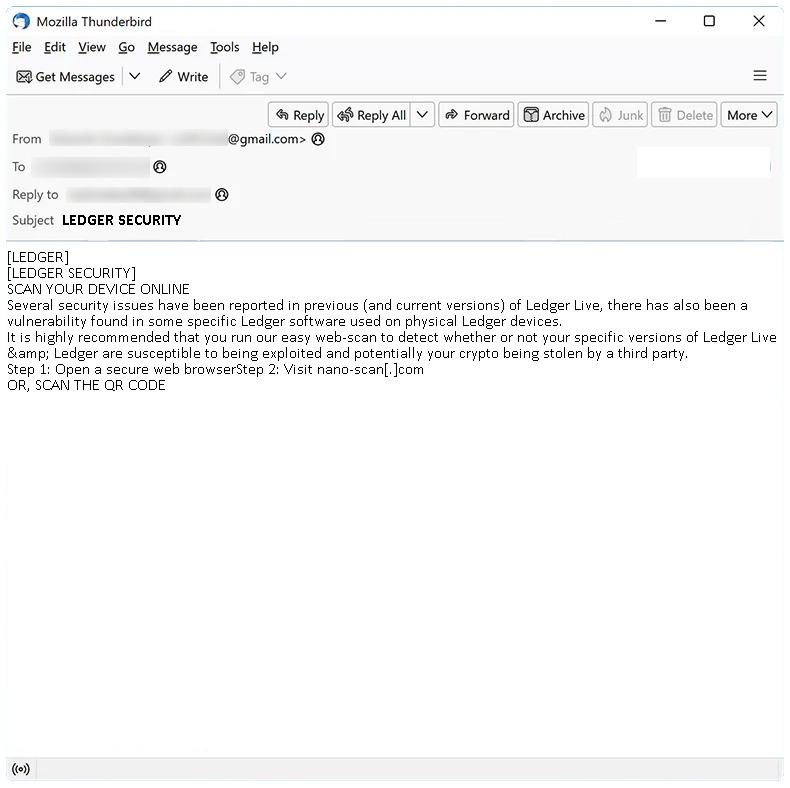
How to stop LEDGER SECURITY email scam
Ledger Security email spam is a type of phishing scam targeting users of Ledger, a popular cryptocurrency wallet. Scammers send fake emails pretending to be from Ledger’s security team, often stating that there has been a security breach and asking the recipient to provide sensitive information or download software supposedly to secure their account.
These spam campaigns infect computers through various methods, often through social engineering techniques. They may trick users into opening malicious attachments or clicking on links that lead to websites containing malware. These viruses can then infect the user’s computer, stealing personal information or taking control over the system.
Interacting with a Ledger Security email scam presents several risks:
1. Malware Infection: If you click on a link or download an attachment from the scam email, you might unknowingly install malware on your computer. This can lead to data theft, system damage, or even control of your device being handed over to cybercriminals.
2. Theft of Sensitive Information: These scams often aim to steal sensitive information such as your Ledger account details, passwords, or even your cryptocurrency funds.
3. Privacy Breach: By gaining access to your personal information, scammers can commit identity theft or sell your information on the dark web.
4. Financial Loss: If the scammers gain access to your Ledger account or other financial accounts, they can steal your funds directly.
To protect yourself, be cautious of any emails demanding immediate action, asking for personal information, or containing unsolicited attachments. Always verify the sender’s email address, and contact the company directly through their official website if you’re unsure. Never download attachments or click on links from suspicious emails.
How to remove Backdoor:Win32/Cycbot!Pz
Backdoor:Win32/Cycbot!Pz is a malicious software, often referred to as a Trojan or backdoor virus, that infiltrates your computer system without you being aware. It is classified under the family of Win32/Cycbot. The primary goal of this malware is to disrupt the normal functioning of your computer and gather your personal information for malicious purposes.
Backdoor:Win32/Cycbot!Pz is typically delivered through spam emails, malicious or hacked web pages, Internet Relay Chat (IRC), peer-to-peer networks, etc. It may arrive on your computer as a component of other malware or as a file downloaded unknowingly by users when visiting malicious sites.
Once it gets into your system, it creates a backdoor that allows the hacker to gain control of your computer remotely. It can steal personal information, such as passwords, login details, and credit card numbers. It also can download and install additional malicious software, modify system settings, and severely compromise system performance.
Backdoor:Win32/Cycbot!Pz is designed to remain undetected by mimicking legitimate processes or embedding itself deep into your system files. It is crucial to maintain updated antivirus software to detect and remove such threats, and always practice safe browsing habits to prevent such infections.