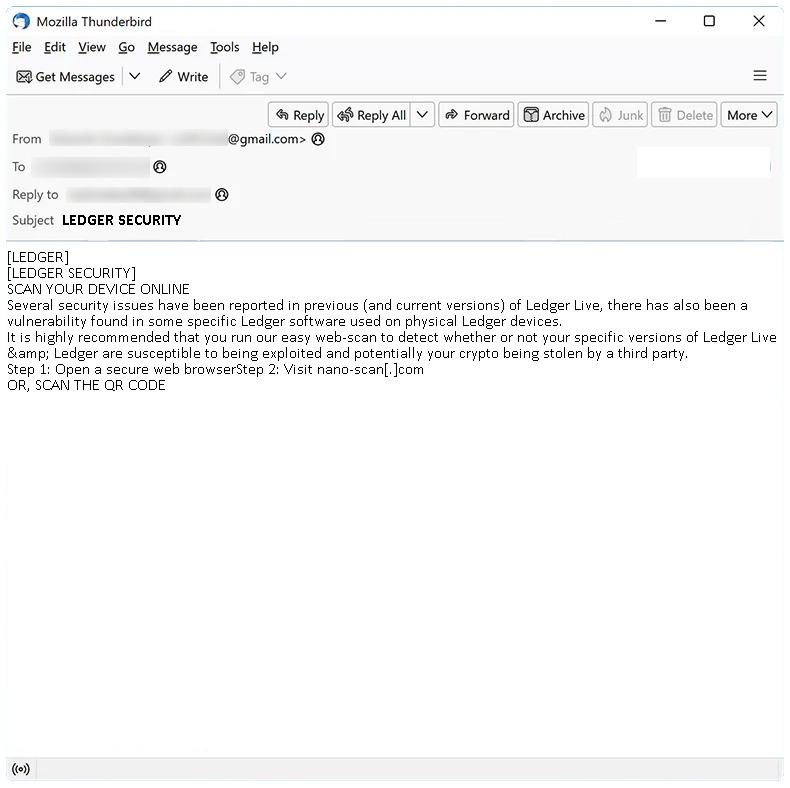
What is “LEDGER SECURITY” e-mail scam
Ledger Security email spam is a type of phishing scam targeting users of Ledger, a popular cryptocurrency wallet. Scammers send fake emails pretending to be from Ledger’s security team, often stating that there has been a security breach and asking the recipient to provide sensitive information or download software supposedly to secure their account.
These spam campaigns infect computers through various methods, often through social engineering techniques. They may trick users into opening malicious attachments or clicking on links that lead to websites containing malware. These viruses can then infect the user’s computer, stealing personal information or taking control over the system.
Interacting with a Ledger Security email scam presents several risks:
1. Malware Infection: If you click on a link or download an attachment from the scam email, you might unknowingly install malware on your computer. This can lead to data theft, system damage, or even control of your device being handed over to cybercriminals.
2. Theft of Sensitive Information: These scams often aim to steal sensitive information such as your Ledger account details, passwords, or even your cryptocurrency funds.
3. Privacy Breach: By gaining access to your personal information, scammers can commit identity theft or sell your information on the dark web.
4. Financial Loss: If the scammers gain access to your Ledger account or other financial accounts, they can steal your funds directly.
To protect yourself, be cautious of any emails demanding immediate action, asking for personal information, or containing unsolicited attachments. Always verify the sender’s email address, and contact the company directly through their official website if you’re unsure. Never download attachments or click on links from suspicious emails.
Download Automated Solutions
Anti-spam solution
Mailwasher is a user-friendly anti-spam tool designed for both individuals and businesses. It stands out for its unique approach to spam management: it allows users to preview emails on the server before they are downloaded to their computer or mobile device. This feature enables users to effectively screen and delete unwanted messages, preventing spam from ever reaching their inbox.
Anti-malware solution
SpyHunter 5 is a powerful malware detection and removal tool developed by EnigmaSoft Limited. It’s designed to provide robust protection against a wide range of malware threats, including viruses, trojans, worms, rootkits, and ransomware. SpyHunter 5 is particularly known for its effectiveness in dealing with complex and evolving malware types that traditional antivirus programs may struggle to detect.
How to set up spam filters manually
1. What Are Spam Filters?
Spam filters are algorithms used by email services to identify and isolate spam emails. They analyze various elements such as the sender’s reputation, message content, and user behavior.
2. How They Work in Popular Services
– Gmail: Uses advanced machine learning algorithms to categorize emails.
– Outlook: Employs a combination of user settings and Microsoft’s smart algorithms.
– Apple Mail: Integrates with macOS and iOS to provide user-controlled filtering.
Enhancing built-in filters, to stop scam like “LEDGER SECURITY”
2. Setting Up filters and rules
Thunderbird
- Go to Tools > Message Filters and choose the email account.
- Click New, name your filter, and specify conditions and actions.
- Set the criteria and choose actions for emails that meet these criteria.
- Click OK to save and activate the filter.
Outlook
- Go to File > Manage Rules & Alerts.
- Click New Rule and follow the prompts to define conditions, actions, and exceptions.
- Choose conditions, specify actions, and set any exceptions.
- Name your rule, click Finish, and Apply.
Gmail
- Click the gear icon and go to See all settings.
- Go to Filters and Blocked Addresses tab and click Create a new filter.
- Create Filter Criteria: Enter criteria and click Create filter.
- Select actions and click Create filter.
Yahoo Mail
- Click the gear icon and go to More Settings.
- Filters: Select Filters and click Add new filters.
- Define Filter: Name your filter, set rules, and choose a folder for the messages.
- Save: Click Save to activate the filter.
Apple Mail
- Go to Mail > Preferences.
- Click the Rules tab and then Add Rule.
- Name your rule, set conditions and actions.
- Click OK to save and activate the rule.
User practices to reduce spam, like “LEDGER SECURITY”
1. Marking Emails as Spam
Consistently marking unwanted emails as spam trains the filter, improving its accuracy over time.
2. Email Address Discretion
Avoid publicly displaying your email address. Consider using disposable email addresses for non-critical sign-ups.
3. Unsubscribe from Newsletters
Regularly unsubscribe from unwanted newsletters and marketing emails.
4. Be Wary of Phishing Attempts
Spam can be a gateway to phishing. Never click on suspicious links or download attachments from unknown sources.
5. Regularly Update Your Email Client
Keeping your email client updated ensures you benefit from the latest spam-fighting features.
Conclusion
Combating spam requires a multifaceted approach that includes the effective use of built-in spam filters, third-party tools, and vigilant personal practices. By regularly fine-tuning your email settings, staying educated on the latest spam trends, and employing smart email management practices, you can significantly reduce the impact of spam on your digital life. Remember, a clutter-free inbox not only enhances productivity but also contributes to a safer online environment.
