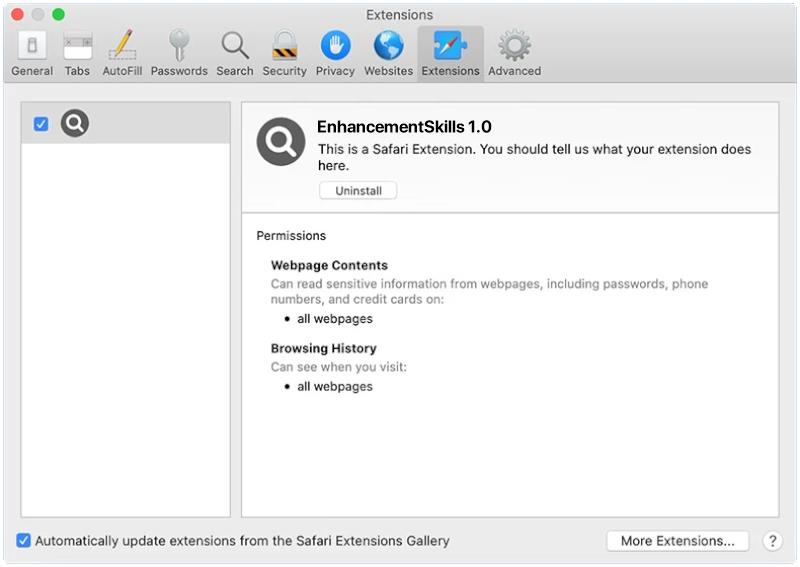
EnhancementSkills is a type of potentially unwanted program (PUP) that is designed to enhance the performance of a Mac computer by claiming to provide various optimization features. However, in reality, EnhancementSkills is considered to be a form of adware that can cause unwanted pop-up ads, redirects to suspicious websites, and other intrusive behavior on the infected system. It may also collect user data and browsing habits to display targeted advertisements.
EnhancementSkills typically infects Mac computers through software bundling, where it is included as a hidden component in freeware or shareware programs. Users may unknowingly install EnhancementSkills when downloading and installing these programs without closely monitoring the installation process. Once installed, EnhancementSkills can be difficult to remove manually and may require the use of specialized anti-malware tools to fully eradicate from the system.