BITCOIN BSC is a cryptocurrency that is built on the Binance Smart Chain (BSC) platform. Binance Smart Chain is a blockchain network that enables developers to create decentralized applications (dApps) and digital assets. BITCOIN BSC is a token that is pegged to the value of Bitcoin, the original cryptocurrency. This means that holders of BITCOIN BSC can benefit from the price movements of Bitcoin without actually owning the cryptocurrency itself.
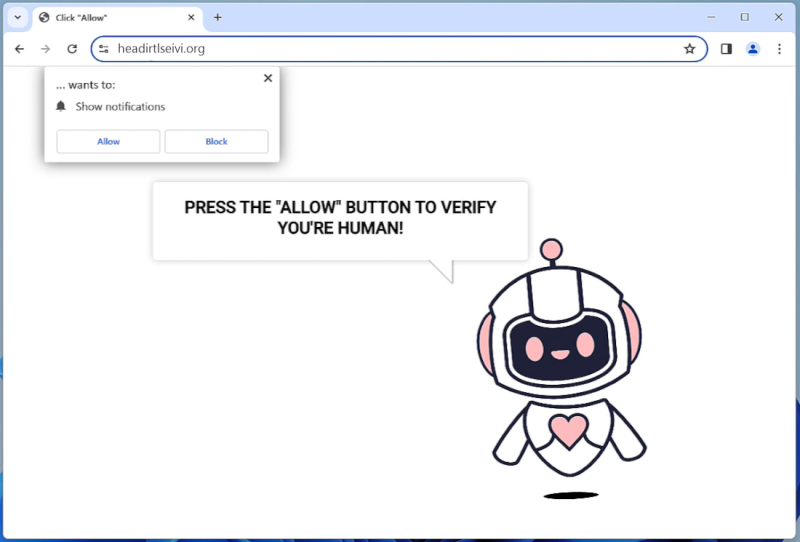
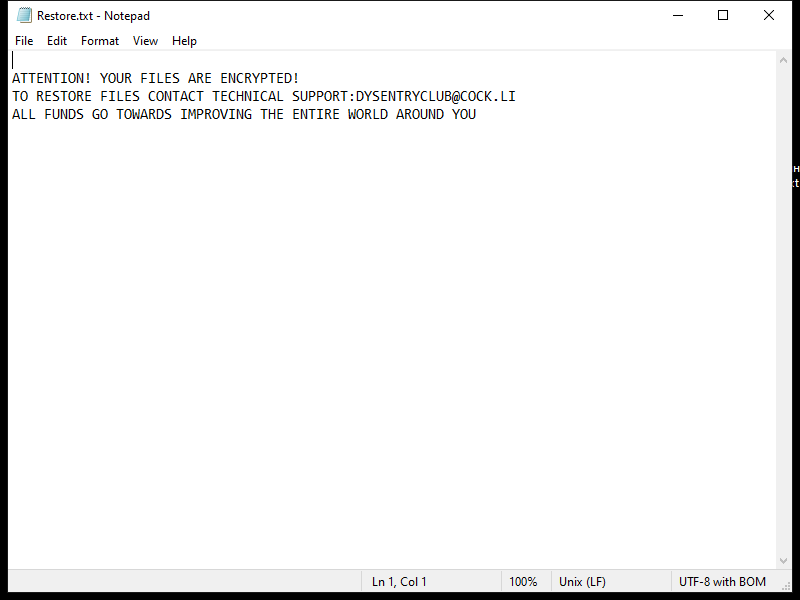
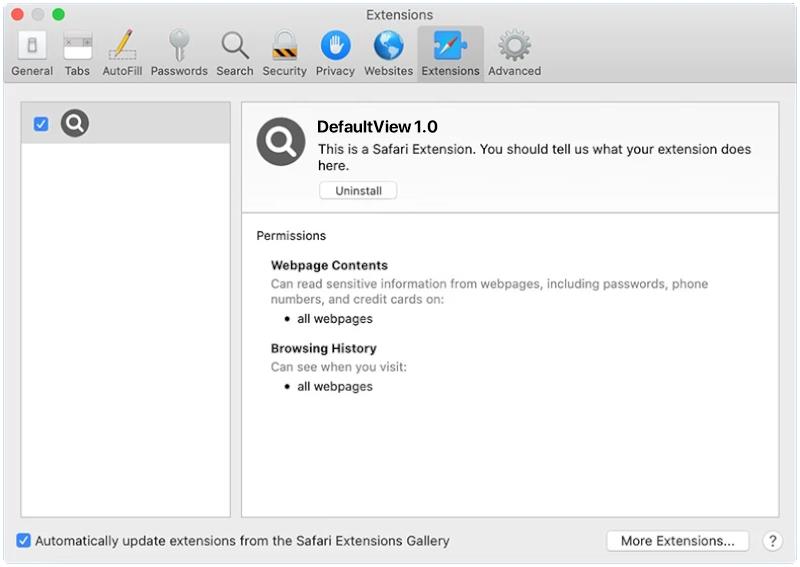
When BITCOIN BSC appears in browsers, it is likely because users are searching for information or trading platforms related to this specific cryptocurrency. Browsers may also display ads or articles about BITCOIN BSC based on the browsing history of the user. It is important for users to exercise caution when interacting with cryptocurrencies like BITCOIN BSC, as the market can be volatile and there is a risk of potential scams or fraud.