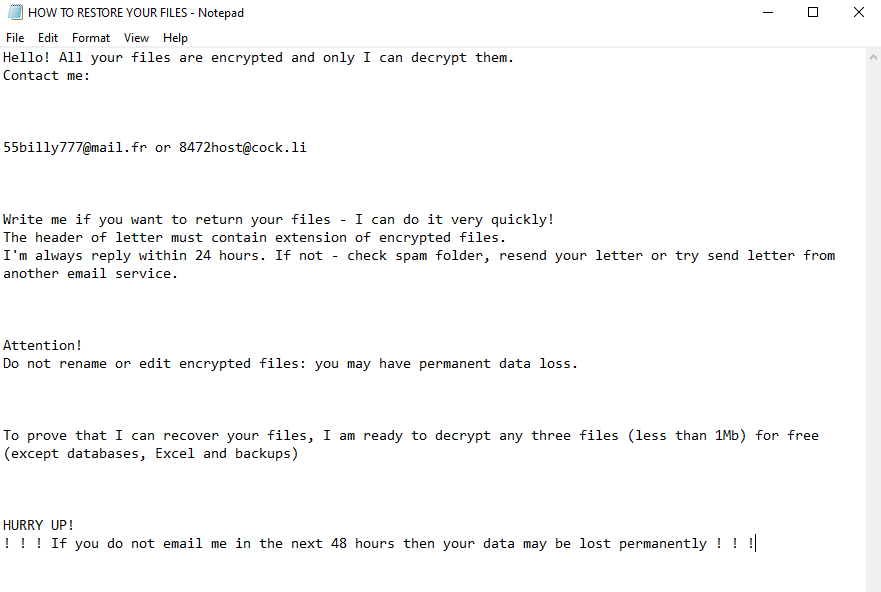
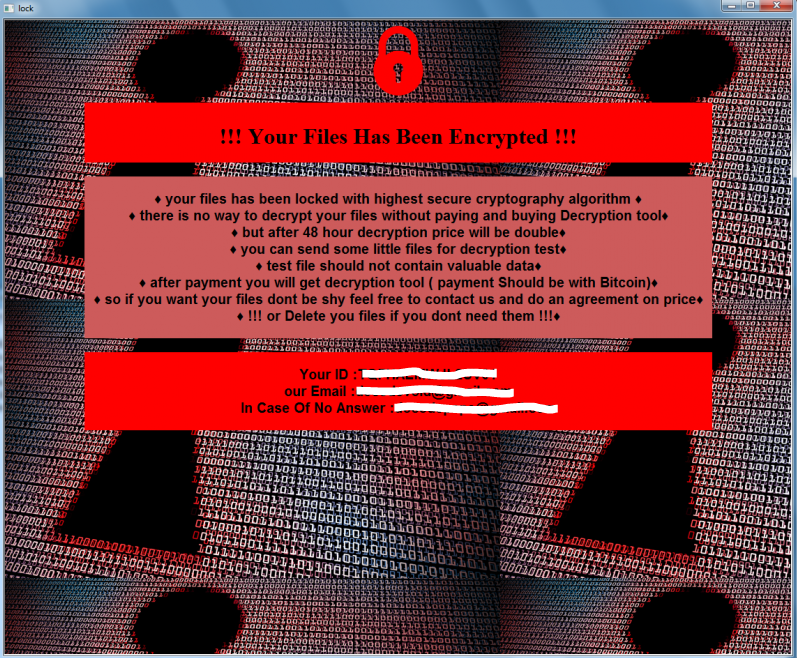
What is Fybtwagknr Ransomware Fybtwagknr is one of the Satch family’s ransomware cryptoviruses, whose activity occurred in the first half of December 2020. This cryptovirus
Author: admin
How to remove Hmmmmm Ransomware and decrypt .hmmmmm files
What is Hmmmmm Ransomware Hmmmmm is another cryptovirus from VoidCrypt family (like .help, Hidden, Dpr, and so on) extorting money from users. Like similar viruses,
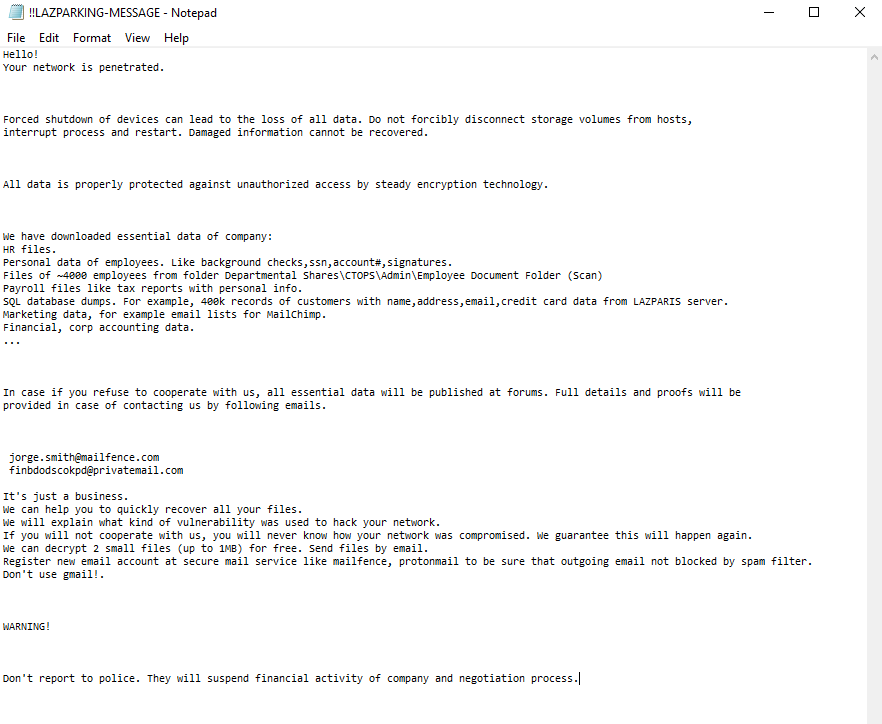
How to remove LAZPARKING Ransomware and decrypt .LAZPARKING files
What is LAZPARKING Ransomware LAZPARKING is ransomware that has spread around the world almost despite the fact that it is initially aimed at English-speaking users.
How to remove .help Ransomware and decrypt .help files
What is .help Ransomware .help is another cryptovirus from VoidCrypt family that encrypts user data. File formats that are subject to encryption may be different,
How to remove Weui Ransomware and decrypt .weui files
What is Weui Ransomware Weui Ransomware is another threat called ransomware, which belongs to a number of crypto-viruses. Genealogically, Weui Ransomware is related to a
How to remove VenomRAT Ransomware and decrypt .venom files
What is VenomRAT Ransomware VenomRAT Ransomware is another encryption of user data, and like analogs, it requires a ransom ($999). It encrypts user files of
How to remove Esexz Ransomware and decrypt .esexz files
What is Esexz Ransomware Esexz is a crypto-extortionist from the Dharma family whose activity came in September of this year. This is a Ransomware that
How to remove Joker Korean Ransomware and decrypt. joker files
What is Joker Korean Ransomware Joker Korean is another crypto-hijacker, encrypting user data and extorting money for decryption. Like analogs, it encrypts data using an
How to remove MXX Ransomware and decrypt .mxx files
What is MXX Ransomware MXX Ransomware is a cryptovirus that encrypts user files and requires redemption, however, it is worth noting that in fact, this
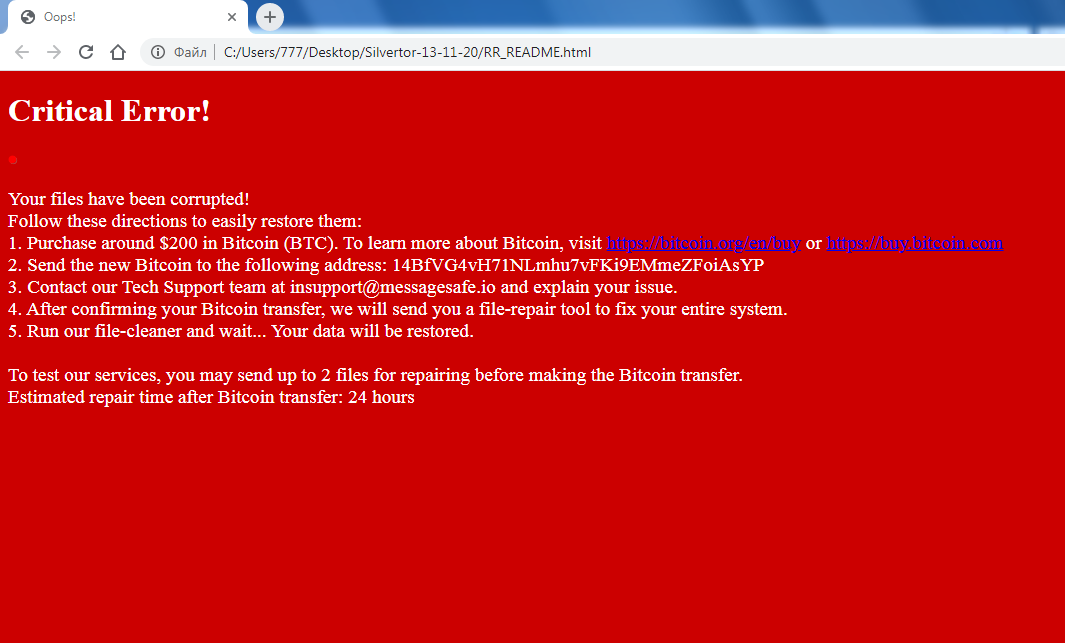
How to remove RedRoman Ransomware and decrypt .REDROMAN files
What is RedRoman Ransomware RedRoman is similar in many ways to similar crypto hackers, for example, it encrypts user files such as photos, videos, audio,