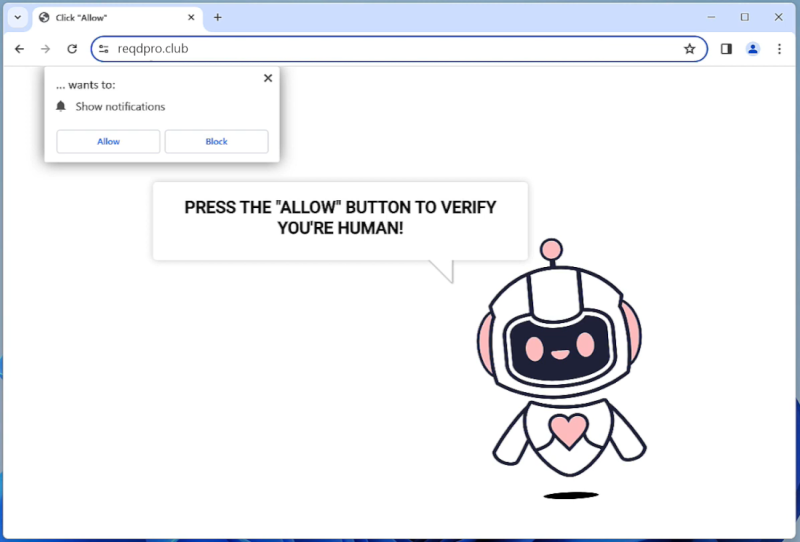
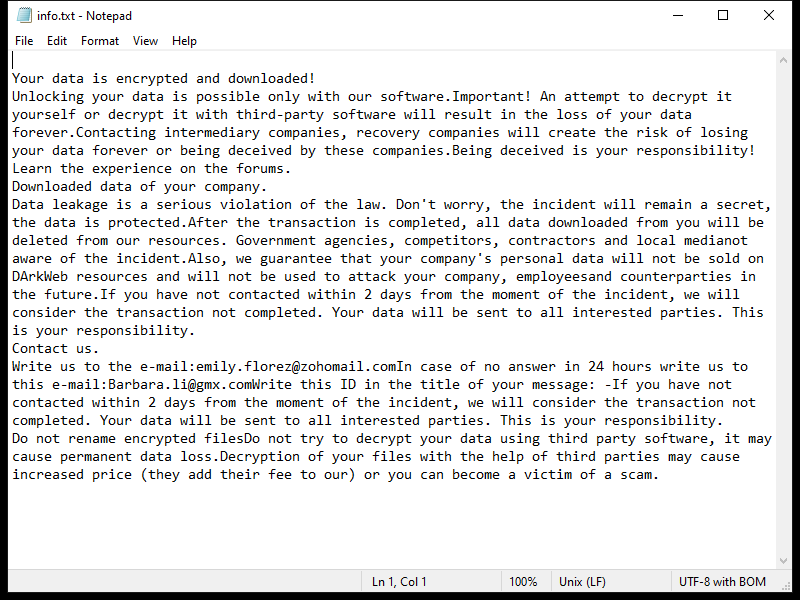
Exploreahoy.com is a type of adware that infects computers and web browsers by displaying intrusive and unwanted advertisements to users. This adware can be installed on a computer through deceptive methods such as bundled software downloads, fake updates, or clicking on malicious links. Once installed, Exploreahoy.com will start showing pop-up ads, banners, and sponsored links on the infected computer, redirecting users to potentially harmful websites.
Exploreahoy.com adware can also collect information about users’ browsing habits and online activities, such as websites visited, search queries, and IP addresses. This data is then used to generate personalized ads and target users with specific products or services. In addition, Exploreahoy.com may also slow down the infected computer and consume system resources, leading to a decrease in performance and overall user experience. It is important for users to be cautious when browsing the internet and to regularly scan their computers for adware and other potentially harmful programs.