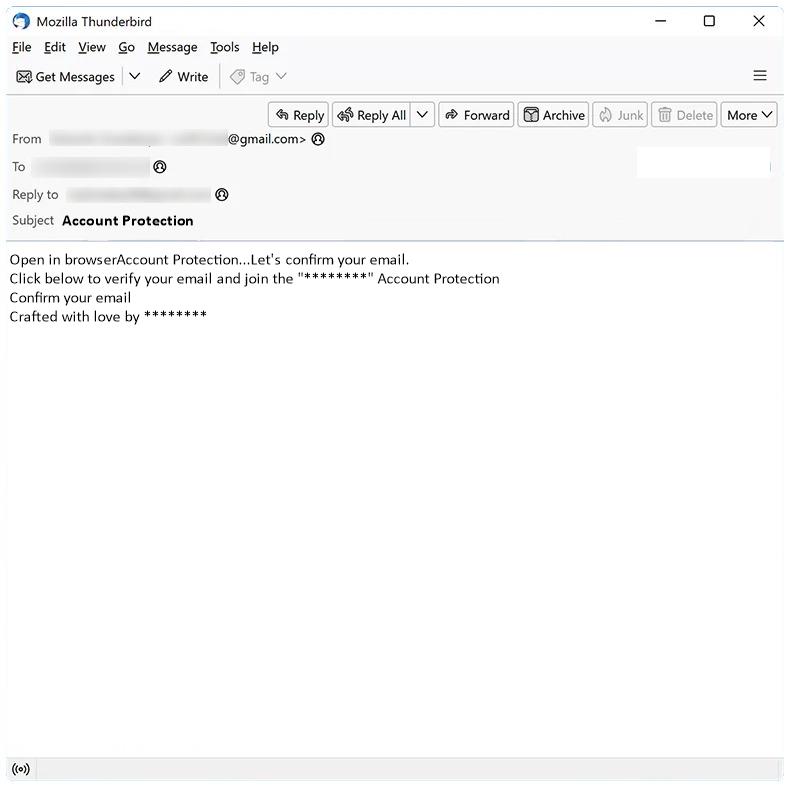
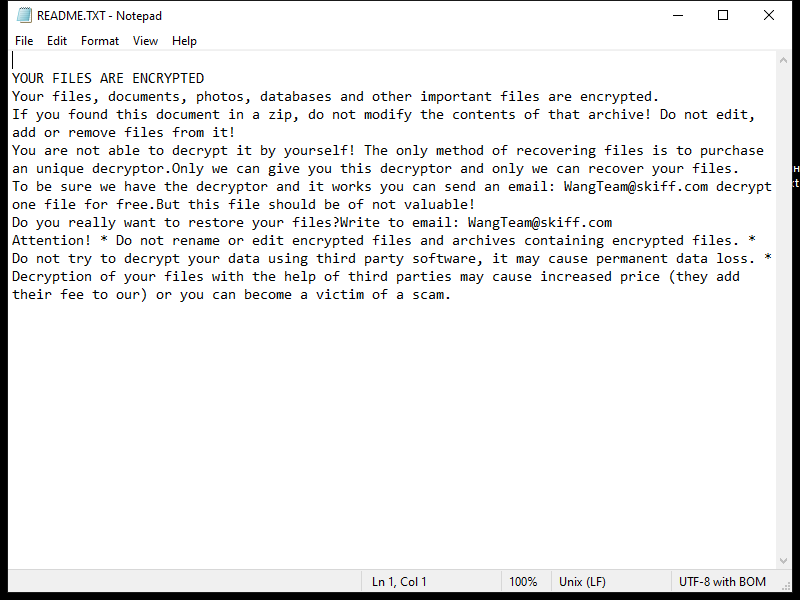
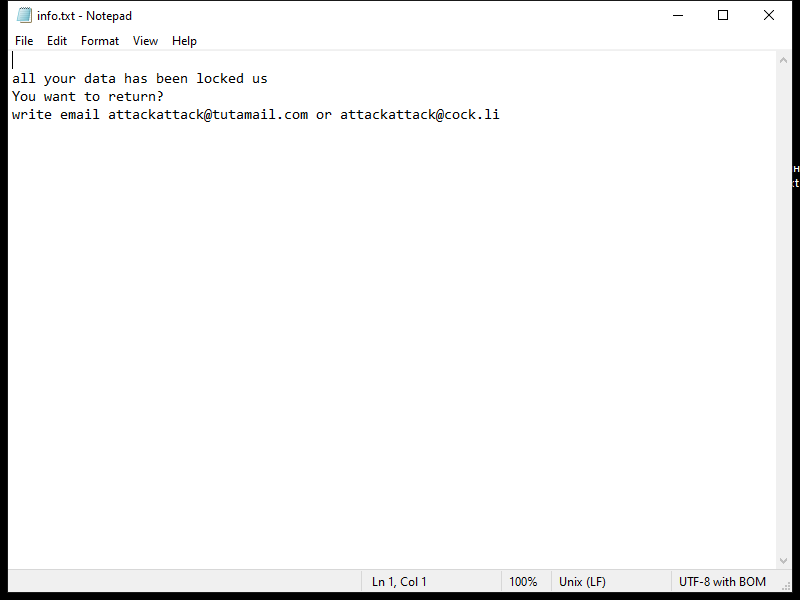
Account Protection email spam is a type of phishing scam that aims to trick recipients into revealing their personal information, such as usernames, passwords, and financial details. These emails usually claim to be from a legitimate source, such as a bank or online service provider, and warn the recipient that their account is at risk of being compromised. The scammer then instructs the recipient to click on a link or download an attachment to verify their account information and secure their account.
Account Protection spam campaigns can infect computers in a number of ways, including:
1. Malware downloads: Scammers may include malicious attachments in their emails that, when opened, download malware onto the recipient’s computer.
2. Phishing websites: Clicking on a link in the email may redirect the recipient to a fake website that looks like a legitimate login page, where the recipient is prompted to enter their account credentials.
3. Social engineering: Scammers may use persuasive language in the email to trick recipients into revealing their personal information willingly.
Interacting with Account Protection email scams can pose several risks, including:
1. Identity theft: Scammers can use the information obtained through these scams to steal the recipient’s identity, access their financial accounts, and commit fraudulent activities.
2. Financial loss: Scammers may use the recipient’s account information to make unauthorized transactions or drain their bank accounts.
3. Malware infections: Clicking on links or downloading attachments in these emails can result in malware infections that can compromise the security and privacy of the recipient’s computer and personal data.
It is important to be cautious when receiving such emails and to verify the legitimacy of any requests for personal information before providing any details. It is advisable to contact the alleged sender through official channels to confirm the authenticity of the email.
Read more