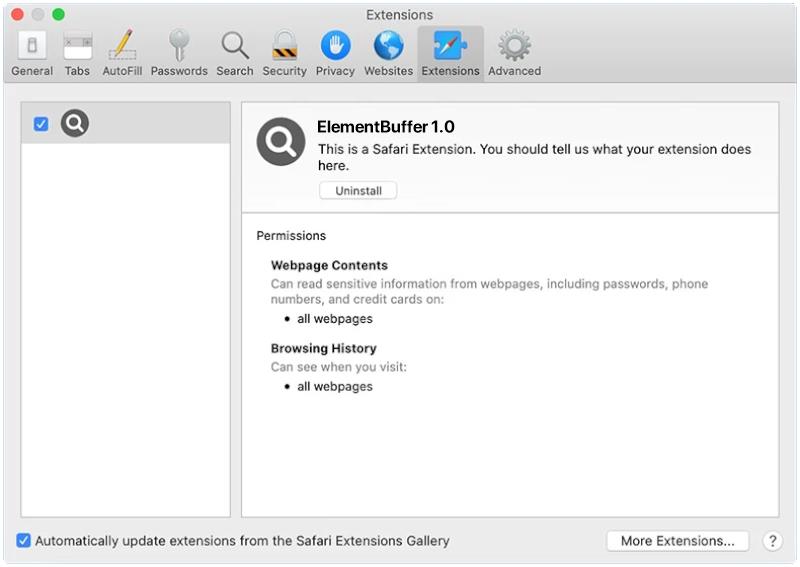
Microsearchers.com is a type of adware that is designed to display unwanted advertisements on users’ computers and browsers. This adware can cause pop-up ads, banners, and other forms of advertising to appear on the screen, disrupting the user’s browsing experience. Microsearchers.com may also track the user’s online activities and gather personal information for marketing purposes.
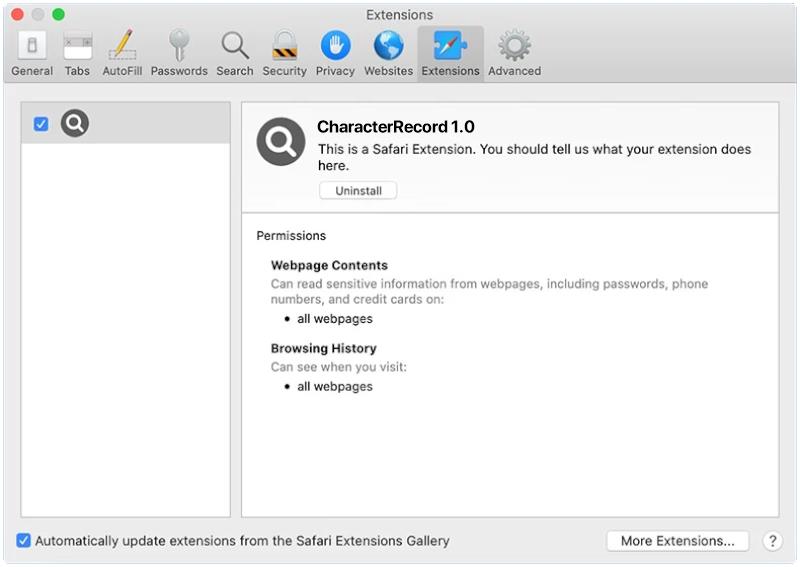
Microsearchers.com typically infects computers and browsers through software bundling, where it is included as an additional component in free software downloads. Users may inadvertently install Microsearchers.com adware when they download and install freeware or shareware programs without paying close attention to the installation process. Once installed, Microsearchers.com can modify browser settings, change the homepage, and redirect the user to sponsored websites, leading to a compromised browsing experience.