Trojan.Bulzpmf.S19392755 is a type of Trojan horse malware that is designed to infect computers and steal sensitive information. It can spread through various methods such as email attachments, malicious websites, or through software downloads.
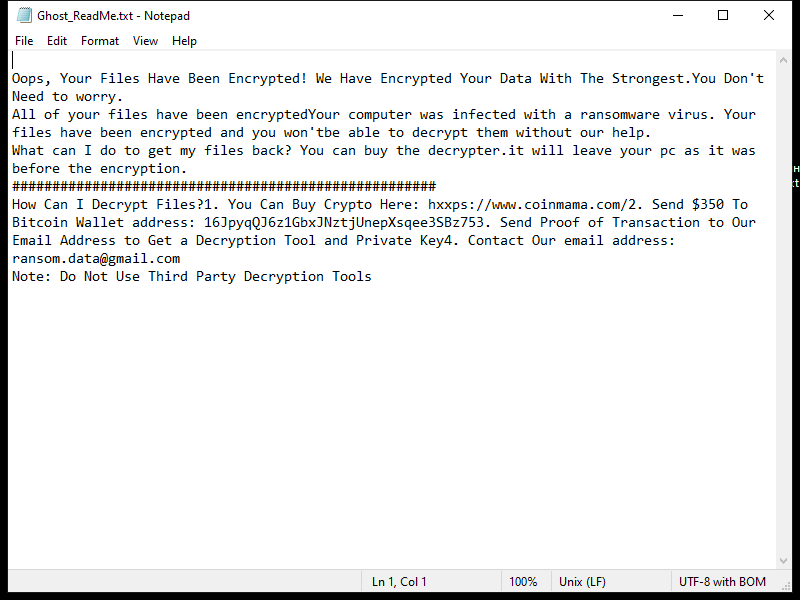
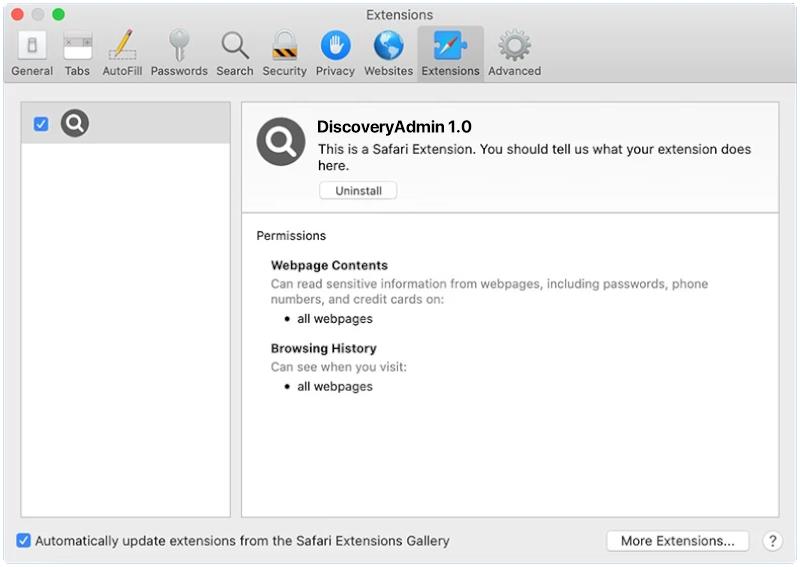
Once installed on a computer, Trojan.Bulzpmf.S19392755 can perform a variety of malicious activities, such as stealing personal information, logging keystrokes, corrupting files, or even taking control of the infected system. It can also create backdoors in the system, allowing remote hackers to access the computer without the user’s knowledge.
To protect your computer from Trojan.Bulzpmf.S19392755 and other types of malware, it is important to keep your operating system and security software up to date, avoid clicking on suspicious links or downloading files from unknown sources, and regularly scan your system for any signs of infection.