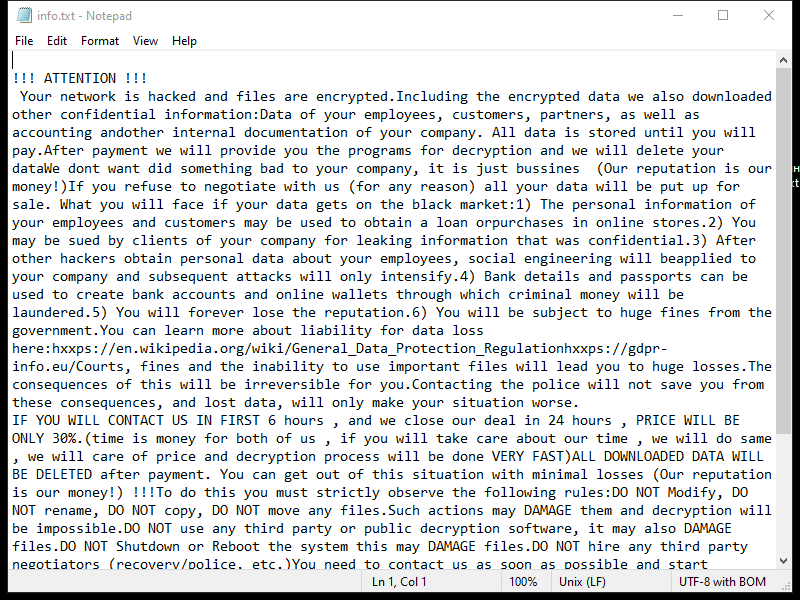
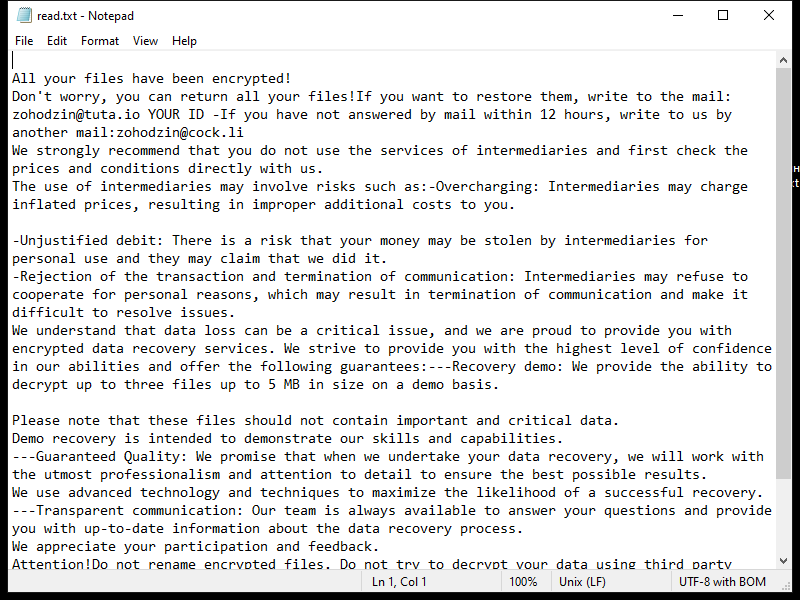
Z1n Ransomware is a type of malicious software that infects computers and encrypts files, making them inaccessible to the user. Here is some information about Z1n Ransomware:
1. Infection: Z1n Ransomware typically infects computers through various methods, including phishing emails, malicious attachments, fake software updates, or exploiting vulnerabilities in outdated software.
2. File Extensions: Z1n Ransomware adds the “.z1n” extension to encrypted files. For example, a file named “document.doc” will be renamed as “document.doc.z1n” after encryption.
3. File Encryption: Z1n Ransomware uses strong encryption algorithms like AES or RSA to encrypt the victim’s files. This encryption makes the files unreadable without the decryption key.
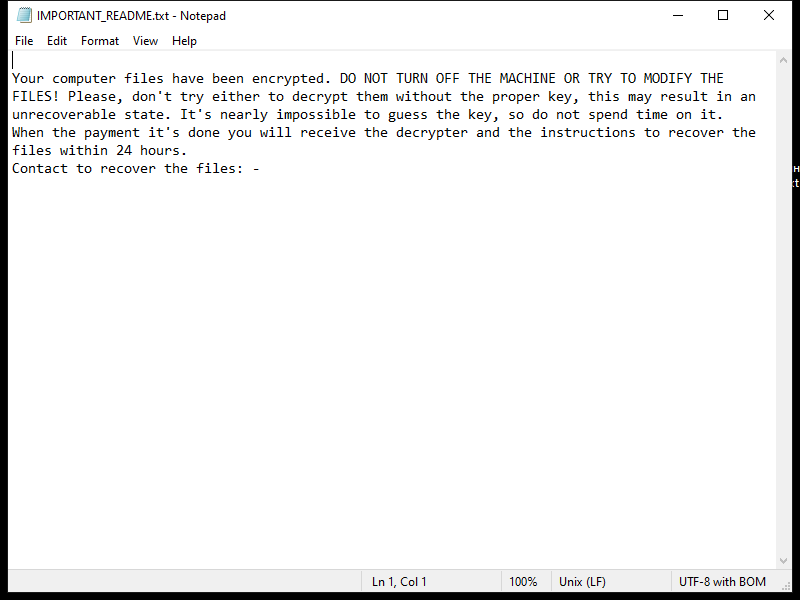
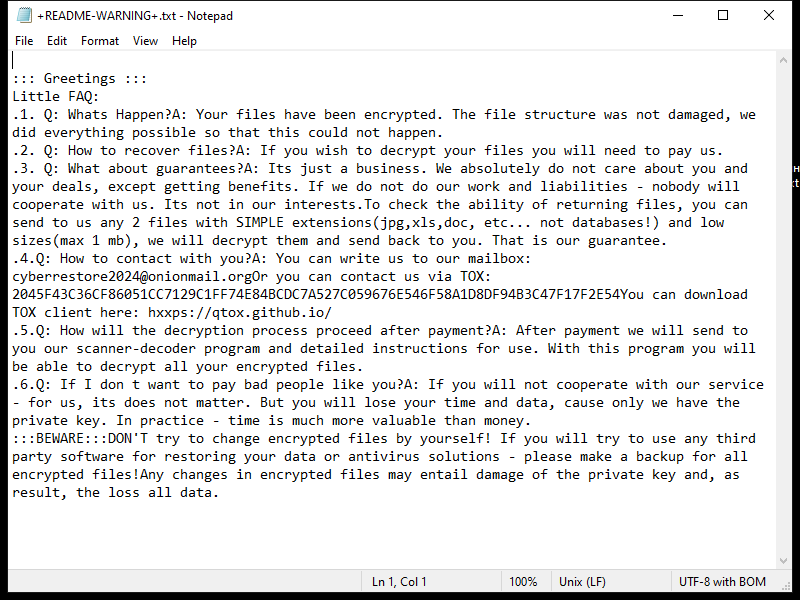
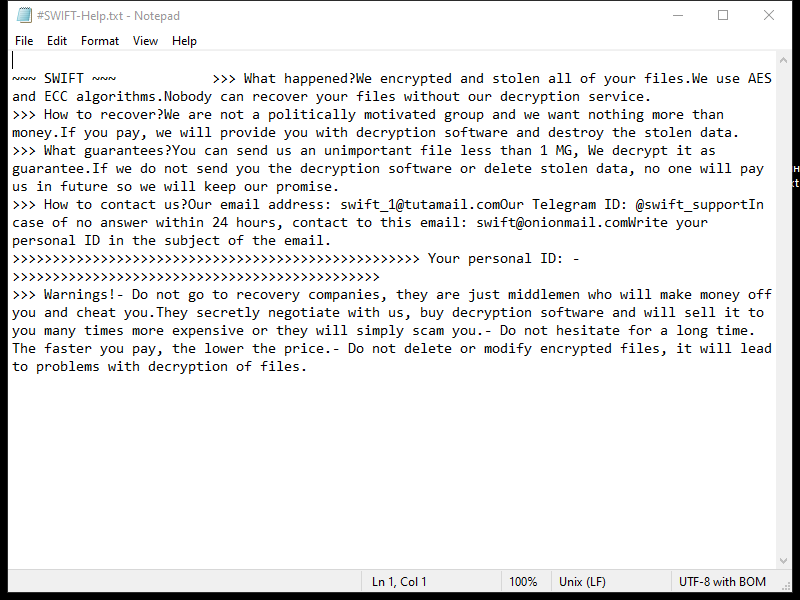
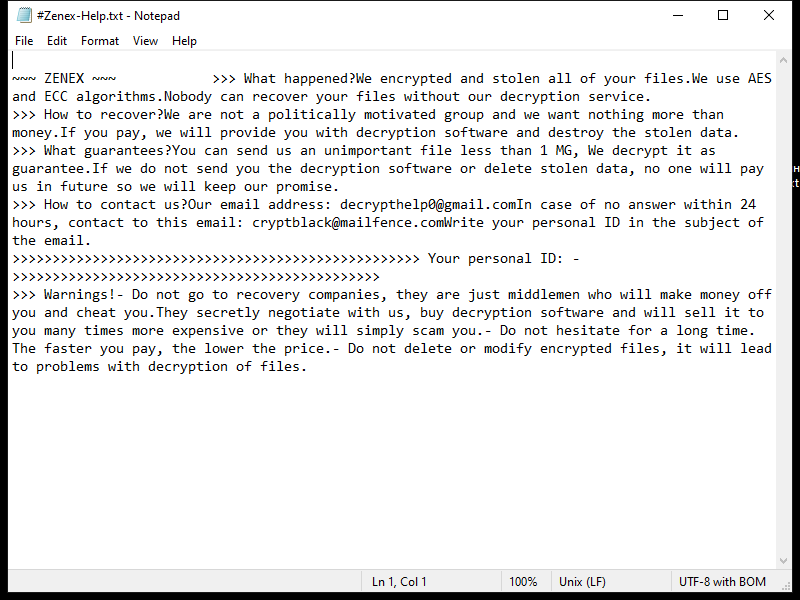
4. Ransom Note: Z1n Ransomware usually creates a ransom note in the form of a text file or a pop-up message. The note contains instructions on how to pay the ransom to obtain the decryption key. The location and name of the ransom note may vary, but it is often placed on the user’s desktop or within folders containing encrypted files.
5. Decryption Tools: At the time of writing, there are no known decryption tools available for Z1n Ransomware. It is always recommended to avoid paying the ransom, as it does not guarantee the recovery of your files, supports criminal activities, and encourages further development of ransomware.
6. Decrypting .z1n Files: Since no decryption tools are available, restoring files encrypted by Z1n Ransomware can be challenging. However, you may try the following steps:
a. Remove the ransomware: Use an up-to-date antivirus program to scan and remove the Z1n Ransomware from your computer.
b. Restore from backup: If you have a recent backup of your files, you can restore them after ensuring that the ransomware is completely removed from your system.
c. Consult professionals: In some cases, data recovery professionals may be able to decrypt your files or provide alternative solutions. However, this can be costly and may not guarantee success.
Remember, prevention is key to avoid ransomware infections. Regularly update your operating system and software, use reliable antivirus software, avoid opening suspicious emails or downloading files from untrusted sources, and maintain secure backups of your important files.
Read more