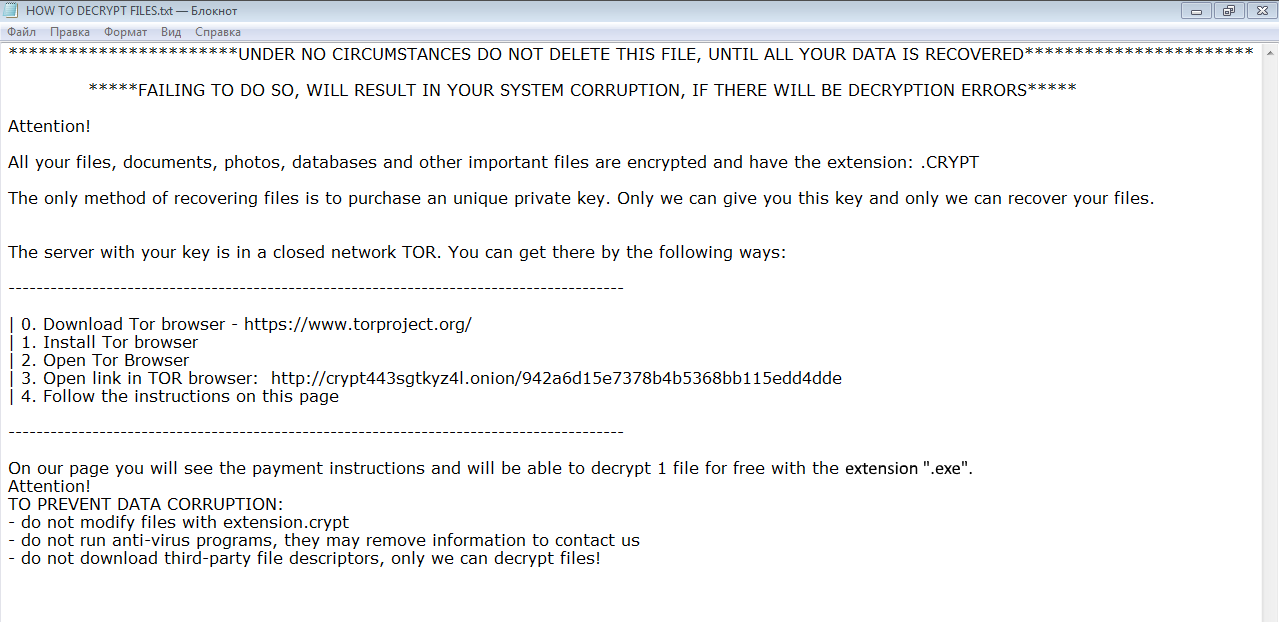
.CRYPT – is a ransomware virus, which means it may cause a lot of headache to any user. In case you are reading this article just because of curiosity – we strongly recommend you not to open any shady spam emails with attachments and keep a proper anti-virus application on your computer. The ransomware can be distributed by hacking through an unprotected RDP configuration, email spam and malicious attachments, fraudulent downloads, exploits, web injections, fake updates, repackaged and infected installers. CRYPT ransomware is able to use encryption on all important files. You can use this guide to remove .CRYPT ransomware and decrypt .CRYPT files.
Category: Ransomware
How to remove Desktop Ransomware and decrypt Lock. files
Desktop – is a ransomware, that can make all the data on a victim’s computer encrypted. This virus have been started to spread at the start of November, 2018. When the encryption process is finished, ransomware will demand for money in order to decode all the files. Most of common file types are endangered by Desktop ransomware, which means all photos, videos, documents and so on are in a perilous predicament. If your computer is infected with Desktop ransomware, we recommend you not to pay anything to these cyber criminals, as there is no guarantee that they will ever respond you. Still, you may use this guide to remove Desktop ransomware and decrypt Lock. files.
How to remove GlobeImposter 2.0 Ransomware and decrypt .docx files
GlobeImposter 2.0 – is an old and notorious ransomware that was quite disastrous some time ago. For now the developers of this ransomware are trying to come into spotlight once again (and of course earn some dirty money). They did some little changes in the virus. We may see new ransom note and extension they use in encryption. GlobeImposter 2.0 will try to find a way into a victim’s system by using fraudulent downloads, botnets, spam emails attachments (don’t ever open them!). When the virus is in a victim’s system, it will start encrypting procedure and encode all the important files (any type of documents, photos, videos, audio files), then ask for money for decryption. A user can’t use the files until they are decrypted, that’s why a lot of their victims pay for the decryption. We recommend you not to pay cyber crooks as it may result in big money loss, the people behind ransomware viruses are usually ignore their victims. Still, you can remove GlobeImposter 2.0 ransomware and decrypt .docx files without paying anything.
How to remove Сrypt888 ransomware and decrypt .crypt888 files
Сrypt888 is a virus, that was developed on the basis of HiddenTear ransomware. It will encipher vulnerable data like images, audios, texts, documents (you may find more detailed list of vulnerable to this ransomware files below) and blackmail a victim. Cyber crooks will offer their “decryption” service in exchange for ransom in BitCoins. If you have this crypto-virus on your computer, use this guide to remove Сrypt888 ransomware and restore .Сrypt888 files without paying anything.
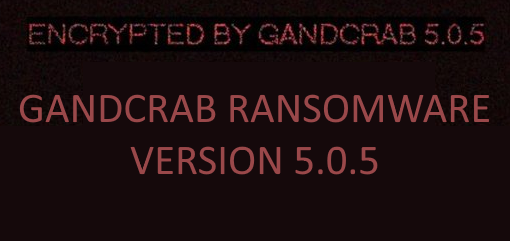
How to remove GANDCRAB 5.0.5 Ransomware and recover your files
GANDCRAB 5.0.5 ransomware is a fifth version of GandCrab 5 ransomware. Cyber criminals create new versions of the ransomware in order to increase their revenue by developing new ways of virus distribution and bypassing of anti-virus applications. GANDCRAB 5.0.5 Ransomware can encode most of important files on a computer. Encryption is blocking any access to the file, that’s why ransomware viruses is critical and considered to be very dangerous. If your computer is infected with GANDCRAB 5.0.5 ransomware, you may use this guide to remove GANDCRAB 5.0.5 ransomware and decrypt GANDCRAB 5.0.5 files.
How to remove HiddenBeer Ransomware and decrypt .beer files
HiddenBeer is a new crypto-virus, that will encipher vulnerable data like images, audios, texts, documents (you may find more detailed list of vulnerable to this ransomware files below) and blackmail a victim. Cyber crooks will offer their “decryption” service in exchange for big sum of money. More than that, there is no guarantee that they will help their victim. If you have this crypto-virus on your computer, use this guide to remove HiddenBeer ransomware and restore .HiddenBeer files without paying anything.
How to remove SOLO Ransomware and decrypt .SOLO files
SOLO is a ransomware, that is mainly targeting German users. It will encrypt all sensitive files (videos, photos, documents) and ask for ransom in order to recover them. The whole point of ransomware viruses is to get money from a victim. In case your computer is infected with this virus, do not worry, in this guide you may find out how to remove SOLO ransomware and restore .SOLO files.
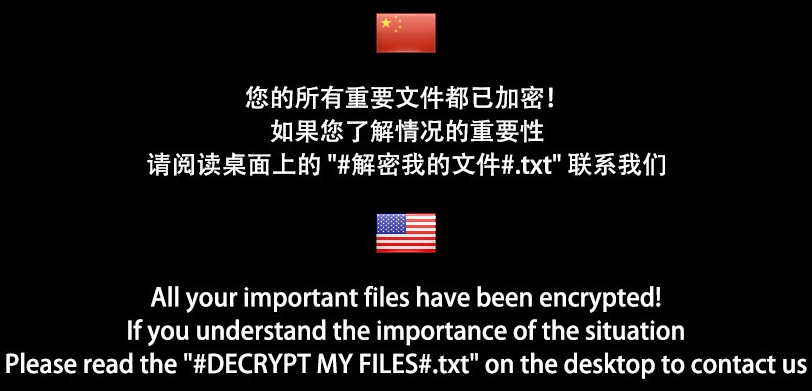
How to remove FilesLocker Ransomware and decrypt .locked files
FilesLocker is a dangerous crypto-virus, that is created with the purpose of blackmailing people. The virus is trying to infiltrate victim’s system with the help of trojans, botnets, exploits and infected spam emails attachments. When the virus successfully infiltrates user’s computer, it will immediately run its malicious processes and start the encryption procedure. It will use AES encryption algorithm to encipher all victim’s data, so that these files can not be used or accessed until they are decrypted. The decryption key may unlock all the data and that is exactly why cyber criminals will offer their deal – money in exchange for decryption key. The cost of decryption may be terrifically huge. In this particular case cyber crooks will demand for 1’152$ in BitCoins (0.18 BTC). Interesting fact – FilesLocker is targeting USA/Eu and Chinese users, there are two available languages for this ransomware: English and Chinese. If you got this virus on your computer, we recommend you to use our guide in order to remove FilesLocker ransomware and decrypt .locked files.
How to remove Yourhope@airmail.cc Ransomware and recover files.
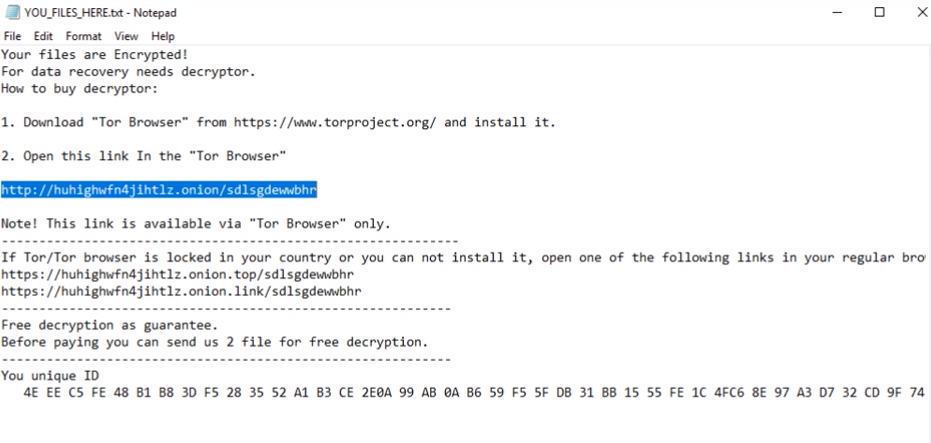
yourhope@airmail.cc is yet another ransomware that was developed by cyber criminals who are in charge of Scarab ransomware family. This ransomware is spreading by using fake updaters, unprotected RDP configuration, fraudulent downloads and spam emails attachments, that’s why it is very important to have any kind of protection on a computer. The encoder is quite similar to others of its kind, once it is in a system, it will encipher the data and ask for money – ransom. This is the reason why this type of viruses are called ‘ransomware’. If you got this virus on your computer, we recommend you to use our guide in order to remove yourhope@airmail.cc ransomware and decrypt .yourhope@airmail.cc files.
How to remove GANDCRAB 5.0.4 Ransomware and recover your files
GANDCRAB 5.0.4 – is the newest version of GANDCRAB 5 ransomware, that was released in October, 2018. It can be distributed by hacking through an unprotected RDP configuration, email spam and malicious attachments, fraudulent downloads, exploits, web injections, fake updates, repackaged and infected installers. GANDCRAB 5.0.4 ransomware is able to use encryption on all important files, then ask for money to decrypt. Use this guide to remove GANDCRAB 5.0.4 ransomware and decrypt GANDCRAB 5.0.4 files.