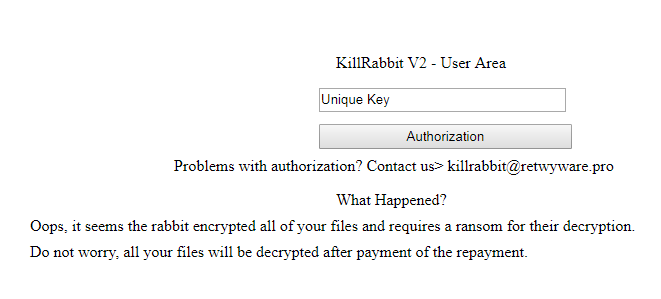
KillRabbit is a crypto-virus, that was created by cyber crooks to generate profit on a brute blackmail. This is the reason why ransomware viruses are so popular amongst cyber criminals, because their victims have to pay for what they are valuing. The encryption is used on photos, videos, audios, text files, documents. It might be something of a personal value or important work data. Once the files are encrypted, cyber crooks ask for money – in this case it is 345$ – to decode these files, because enciphered data can not be used or accessed in any possible way. If you have this ransomware on your computer, we recommend you not to invest into this criminal scheme, as there are no such thing as some kind of guarantee when you communicate with the people who are responsible for the ransomware distribution. You may learn how to remove KillRabbit and restore .gameover files in this article.
Category: Ransomware
How to remove GlobeImposter 2.0 and decrypt .FORESTGUST files
GlobeImposter 2.0 – is an old and notorious ransomware that was quite disastrous some time ago. For now the developers of this ransomware are trying to come into spotlight once again (and ofcourse earn some dirty money). They did some little changes in the virus. We may see new ransom note and extension they use in encryption. GlobeImposter 2.0 will try to find a way into a victim’s system by using fraudulent downloads, botnets, spam emails attachments (don’t ever open them!). When the virus is in a victim’s system, it will start encrypting procedure and encode all the important files (any type of documents, photos, videos, audio files), then ask for money for decryption. A user can’t use the files until they are decrypted, that’s why a lot of their victims pay for the decryption. We recommend you not to pay cyber crooks as it may result in big money loss, the people behind ransomware viruses are usually ignore their victims. Still, you can remove GlobeImposter 2.0 ransomware and decrypt .FORESTGUST files without paying anything.
How to remove XiaoBa 2.0 Ransomware and decrypt .XIAOBA files
XiaoBa 2.0 ransomware is a crypto-virus, that has developed from an older version of XiaoBa ransomware. The virus is encrypting all victim’s data and ask for money to decode them so that a victim may use these files again. Interesting fact: the developers of XiaoBa 2.0 ransomware have truly worldwide ambitions – their ransom note contains 20 available languages, including Chinese as the first one (possibly means that cyber criminals operate from China), English, German, Russian. This ransomware is trying to infiltrate victim’s system by using fake Adobe Flash Player installer, it may also use variety of methods like spam emails attachments, botnets, fraud downloads and so on. In case you have this virus on your computer, you can use this guide to remove XiaoBa 2.0 Ransomware and decrypt .XIAOBA files.
How to remove Bin 2 ransomware and decrypt .bin2 files
Bin 2 is the newer version of Bin ransomware from Scarab ransomware developers. This ransomware works quite the same way as an older one: it will search for vulnerabilities in a victim’s system in order to use them and infect a PC. Once it is in a system, it will encode all the personal files so that a user unable to use them anymore. To get control over these files, a victim have to pay to the cyber crooks for decryption. In case your PC infected with this ransomware, we recommend you to use this guide to remove Bin 2 ransomware and decrypt .bin2 files.
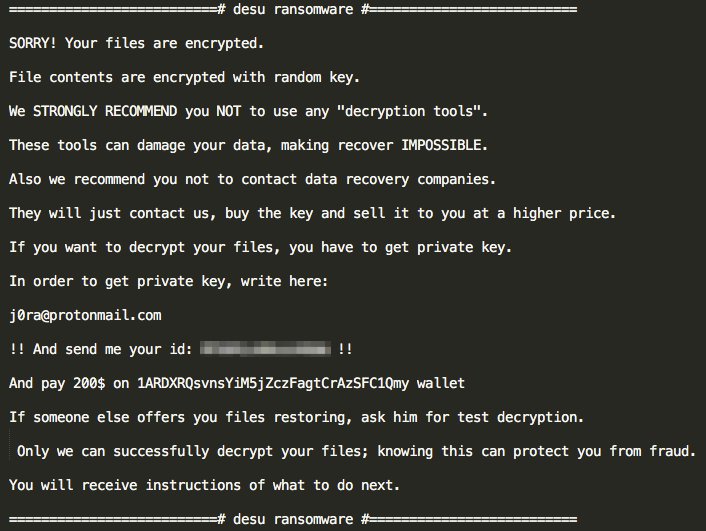
How to remove Desu ransomware and decrpyt .desu files
Desu ransomware is a crypto-virus, that will encode all the files on a victim’s PC and blackmail for ransom money. It works quite the same way as any other ransomware. Their scheme is to break into victim’s system, block anything that may stop the virus, do the encryption process, then ask for payment to fix the issue like they are offering some kind of legitimate service and some lifesavers. The thing is, a lot of people do pay to cyber crooks, because encrypted files (all the photos, audios, videos, any type of documents and so on) can’t be used until they are decrypted. But, unfortunately, there are a lot of cases where cyber criminals do not help their victims, even if they pay up. If your computer is infected, learn how to remove Desu ransomware and decrypt .desu files in this user-friendly guide.
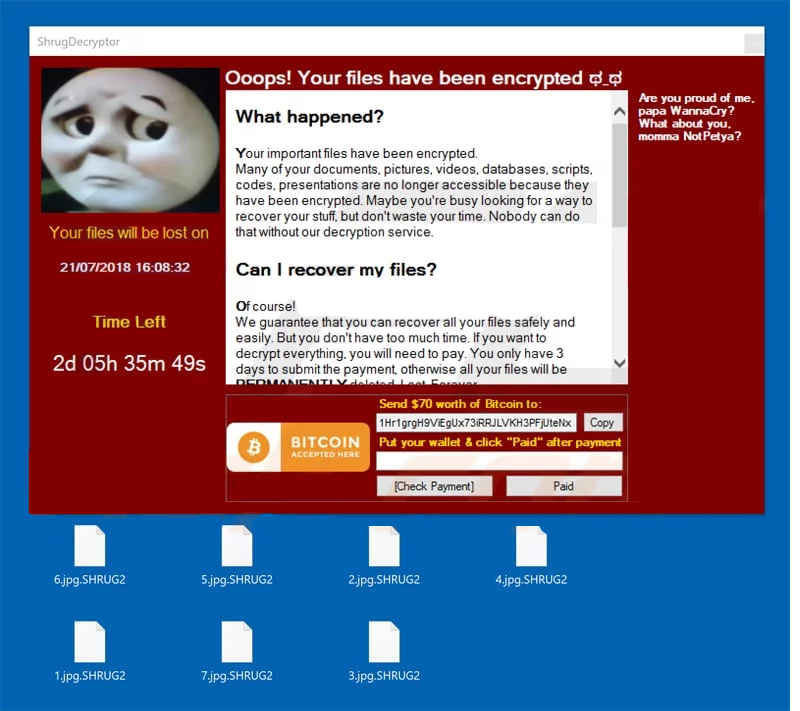
How to remove SHRUG ransomware and decrypt .SHRUG2 files
SHRUG – is a new ransomware, that was released in July, 2018. It can be distributed by hacking through an unprotected RDP configuration, email spam and malicious attachments, fraudulent downloads, exploits, web injections, fake updates, repackaged and infected installers. SHRUG ransomware is able to use encryption on all important files, then ask for money to decrypt. In fact, no one can tell for sure if they would decrypt these files. Most of cyber criminals ignore their victims, some of them even have no idea how to decrypt encrypted data. That;s why if your computer is infected with SHRUG ransomware, you should not pay for decryption of your files. Still, you can remove SHRUG ransomware and decrypt .SHRUG2 files without paying anything.
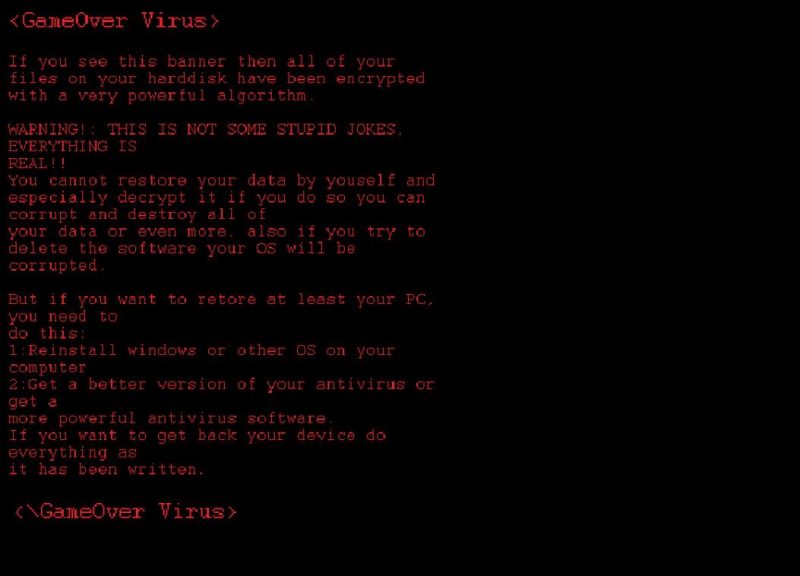
How to remove GameOver Virus and restore .gameover files
GameOver Virus – is a ransomware, that has one quite unique feature. It will not ask a victim to pay ransom, so basically we can call this virus “ransomware” only because of the way it works. GaveOver Virus ransomware will use any vulnerabilities to sneak into victim’s computer. Once it is in the system, the virus will start encryption of the files, and when it is finished a user will see lock-screen window with the message. Nobody can tell why this kind of viruses exist, it would not even generate any profit to someone. Still, if you have this ransomware on your computer, you may learn how to remove GameOver Virus and restore .gameover files in this article.
Remove LanRan2.0.5!Demonstration ransomware and decrypt .LanRan2.0.5!Demonstration
LanRan2.0.5!Demonstration is a new crypto-virus, that will encipher vulnerable data like images, audios, texts, documents (you may find more detailed list of vulnerable to this ransomware files below) and blackmail a victim. Cyber crooks will offer their “decryption” service in exchange for big sum of money. More than that, there is no guarantee that they will help their victim. If you have this crypto-virus on your computer, use this guide to remove LanRan2.0.5!Demonstration ransomware and restore .LanRan2.0.5!Demonstration files without paying anything.
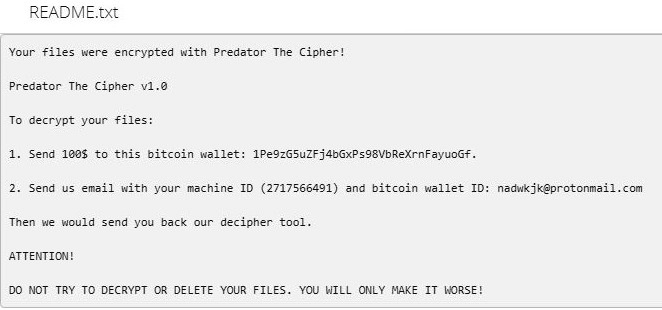
How to remove Predator The Cipher and decrypt .predator files
Predator The Cipher – is an encoder, that has been discovered in the beginning of July, 2018. The workflow of this crypto-virus is quite similar to other ransomware threats. First of all, it will try to find the way to sneak into a victim’s PC, it will use any unprotected connections and vulnerabilities of a system. Then, if it gets onto victim’s computer, it will immediately take control and start malicious processes, one of them is encryption procedure. Encrypting of infected files would not take much time. When the files are encoded they would not be accessible in any possible way. So, in order to be able to use infected files again, a victim need to pay money ransom, in this particular case it is 100$. We recommend you not to pay anything, as there are no guarantees of getting your files back. If you have this crypto-virus on your computer, use this guide to remove Predator The Cipher ransomware and restore .predator files without paying anything.
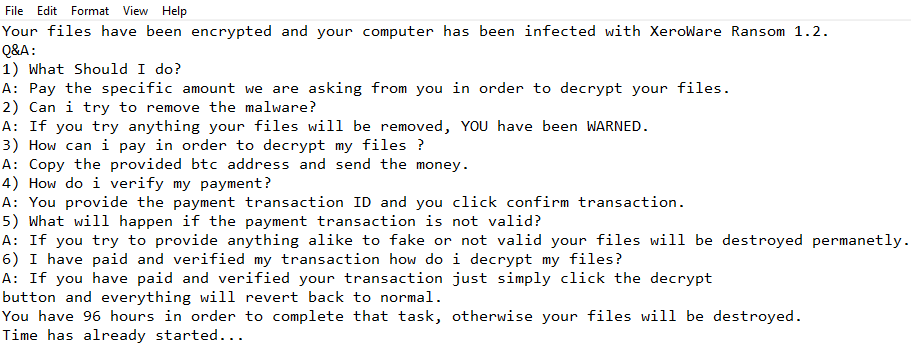
How to remove XeroWare ransomware and decrypt .XERO files
What is XeroWare ransomware XeroWare – is a crypto-virus, that will run AES encryption algorithms on infected computer. After this process, a victim of this