Lexus Ransomware is a type of malicious software that encrypts files on a victim’s computer, making them inaccessible until a ransom is paid. It typically infects computers through phishing emails, malicious websites, or software vulnerabilities.
Once infected, Lexus Ransomware adds a “.lexus” extension to encrypted files, making them easily identifiable. It uses a strong encryption algorithm to lock the files, making decryption without the encryption key nearly impossible.
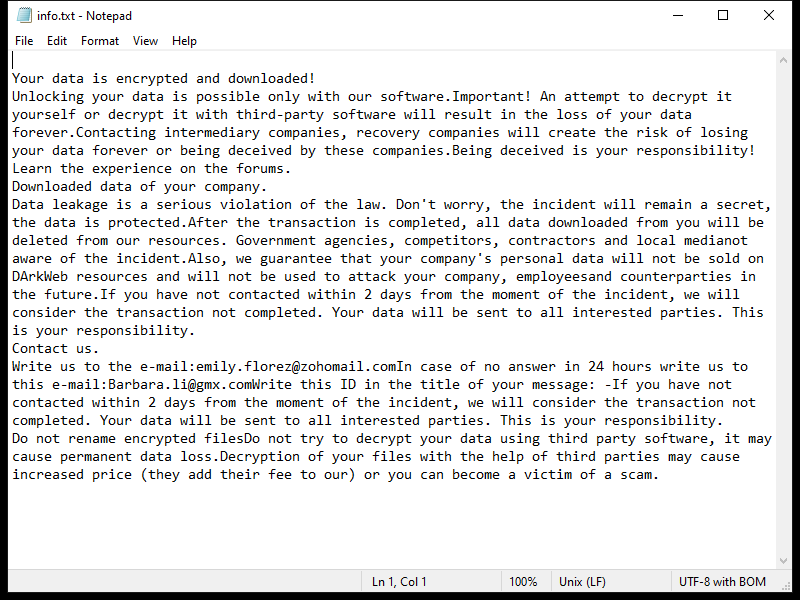
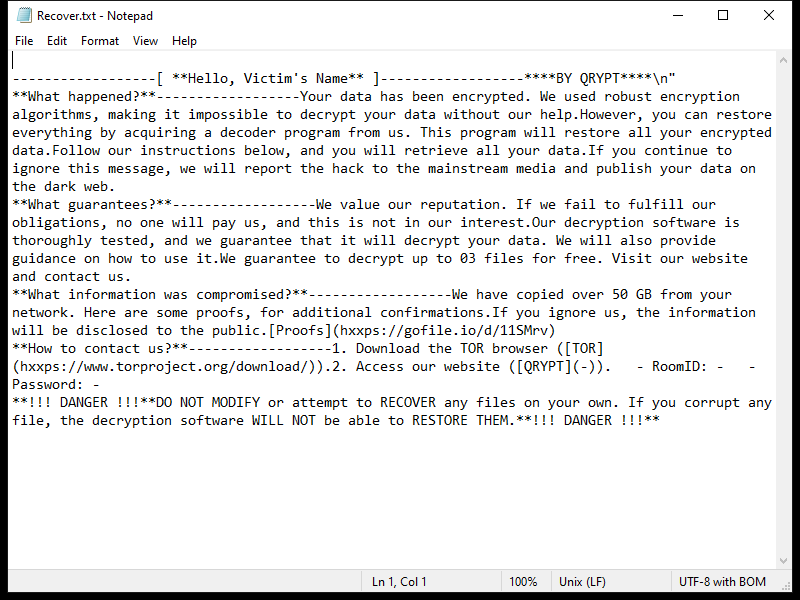
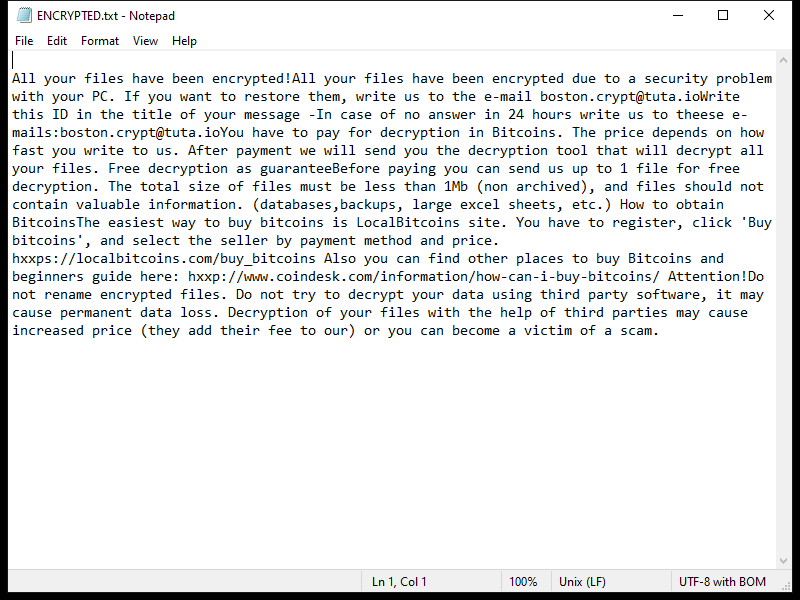
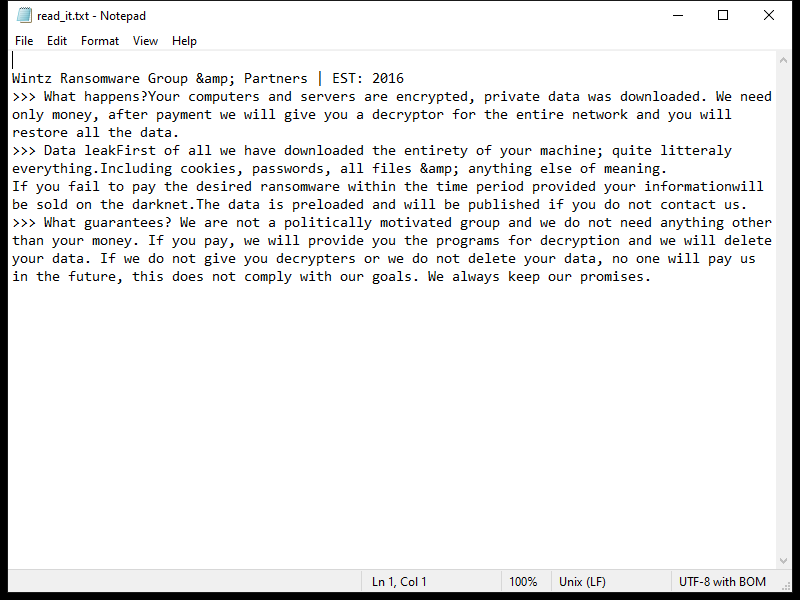
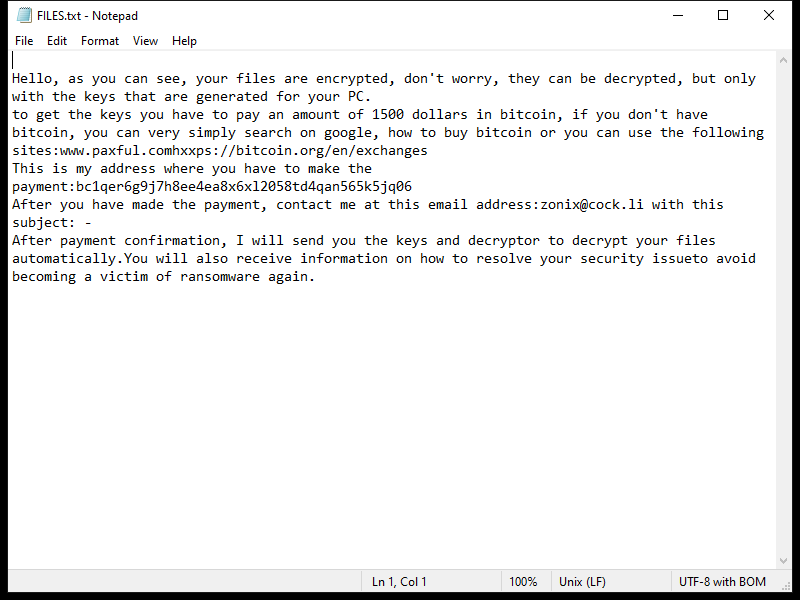
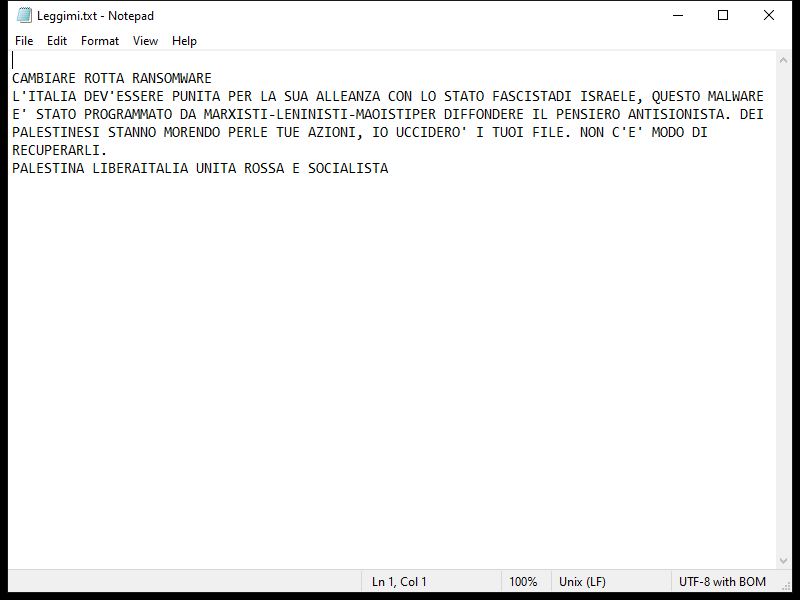
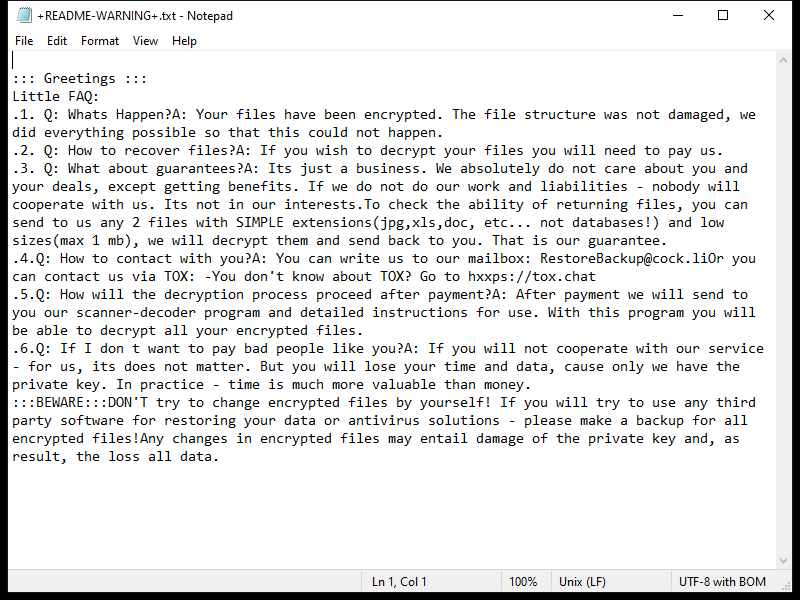
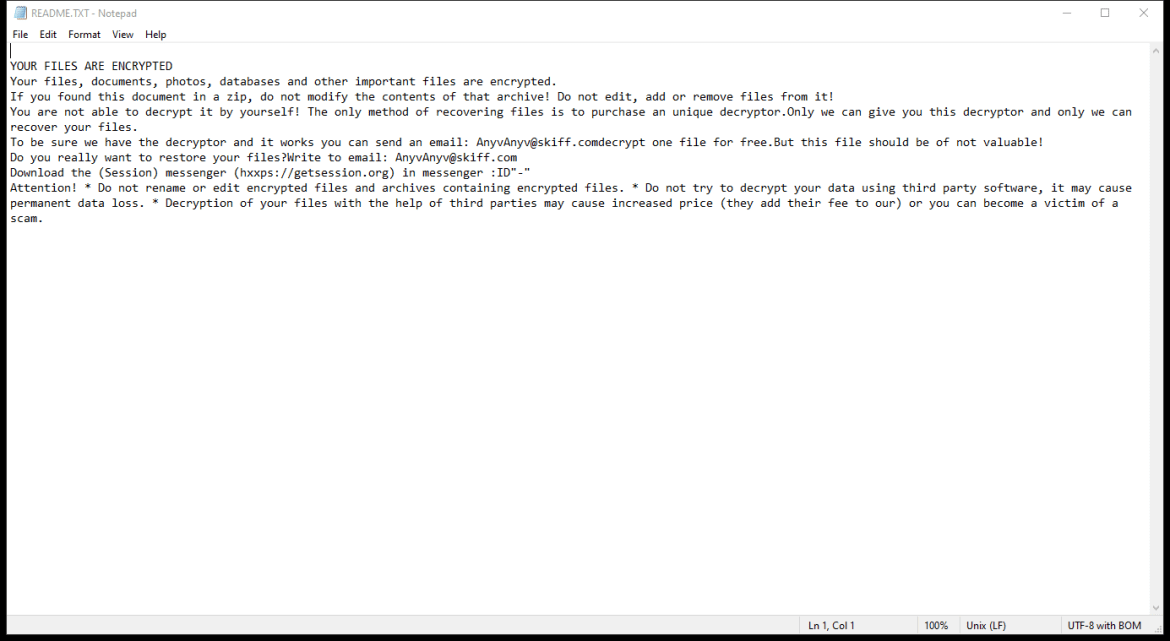
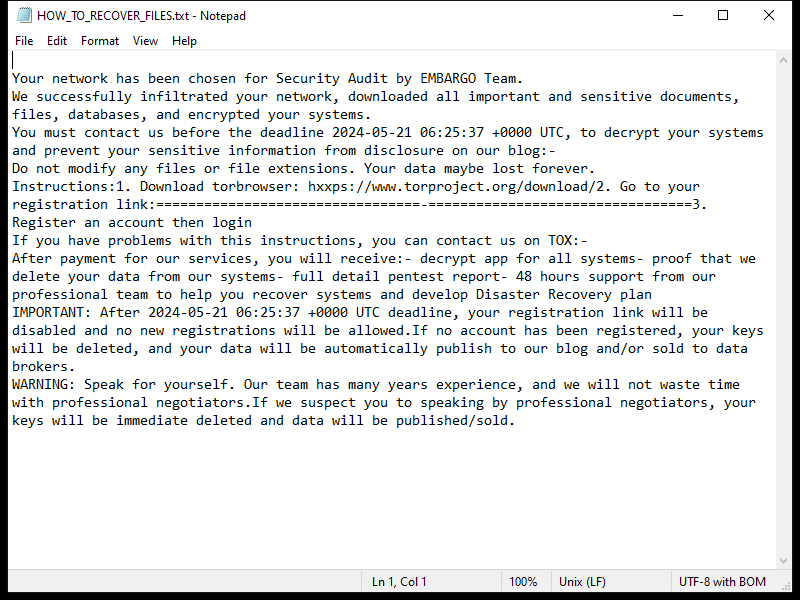
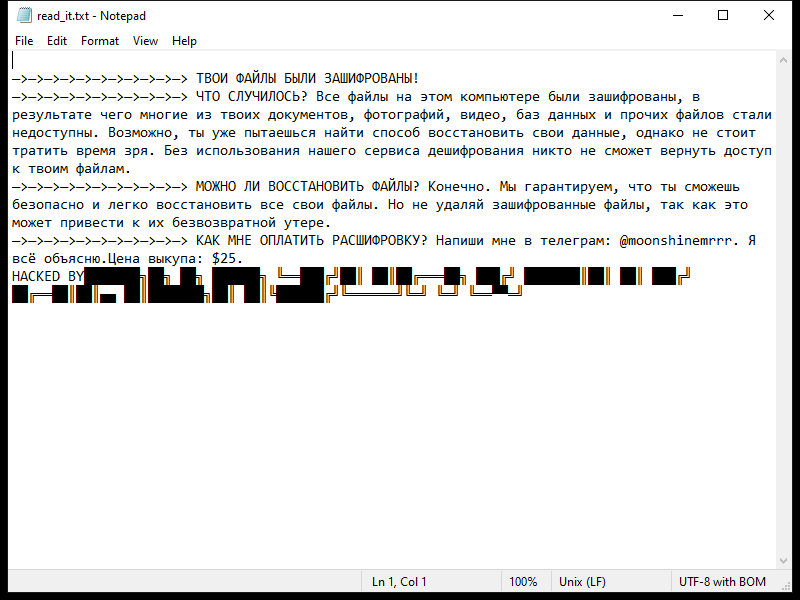
After encrypting the files, Lexus Ransomware creates a ransom note typically named “README_LEXUS.txt” or similar, which contains instructions on how to pay the ransom to get the decryption key.
As of now, there are no decryption tools available for .lexus files. However, it is not recommended to pay the ransom as there is no guarantee that the cybercriminals will provide the decryption key or that it will work.
If you have been affected by Lexus Ransomware, the best course of action is to remove the malware from your system using reputable antivirus software and restore your files from backups if available.