Napoli Ransomware is a type of malware that infects computers by encrypting the files on the system and then demanding a ransom from the victim in exchange for the decryption key. It typically spreads through malicious email attachments, fake software updates, or compromised websites.
When Napoli Ransomware infects a computer, it adds a “.napoli” file extension to the encrypted files. It uses strong encryption algorithms such as AES or RSA to lock the files, making them inaccessible without the decryption key.
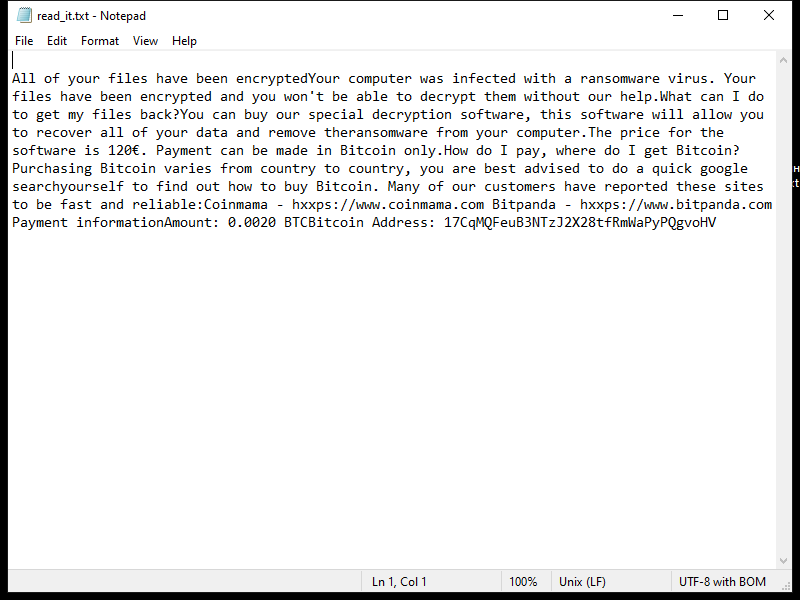
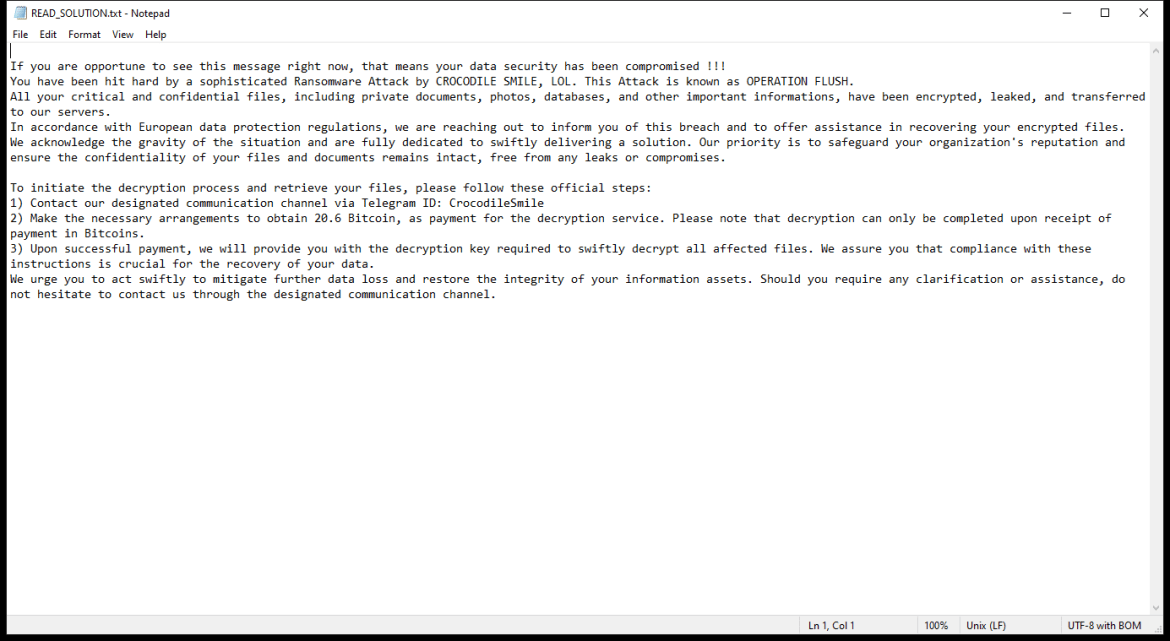
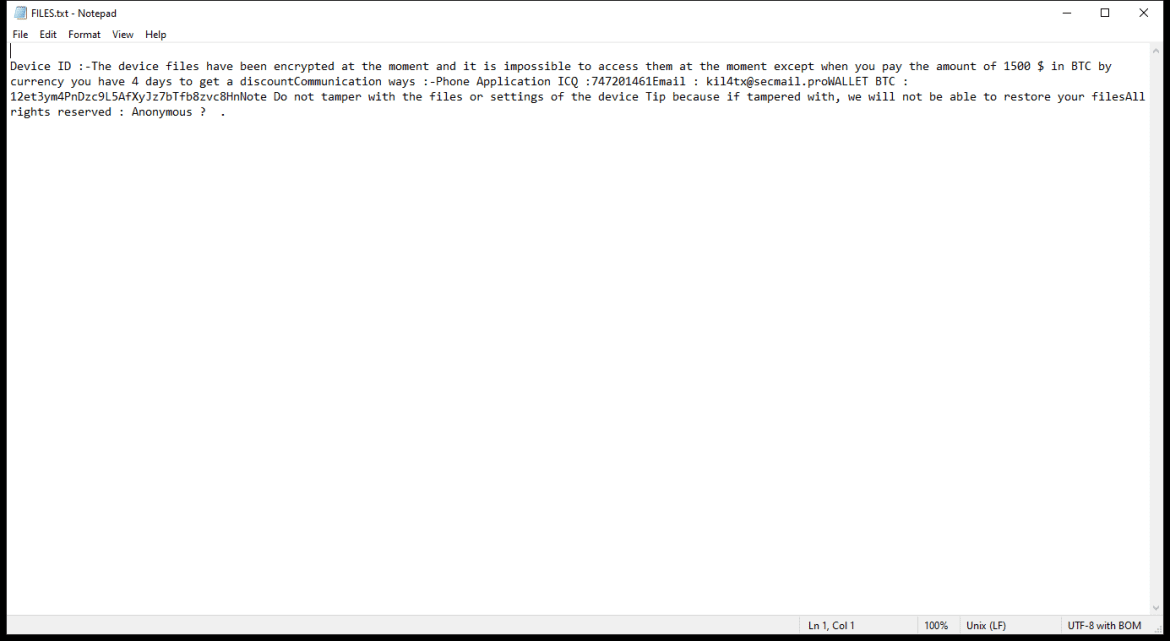
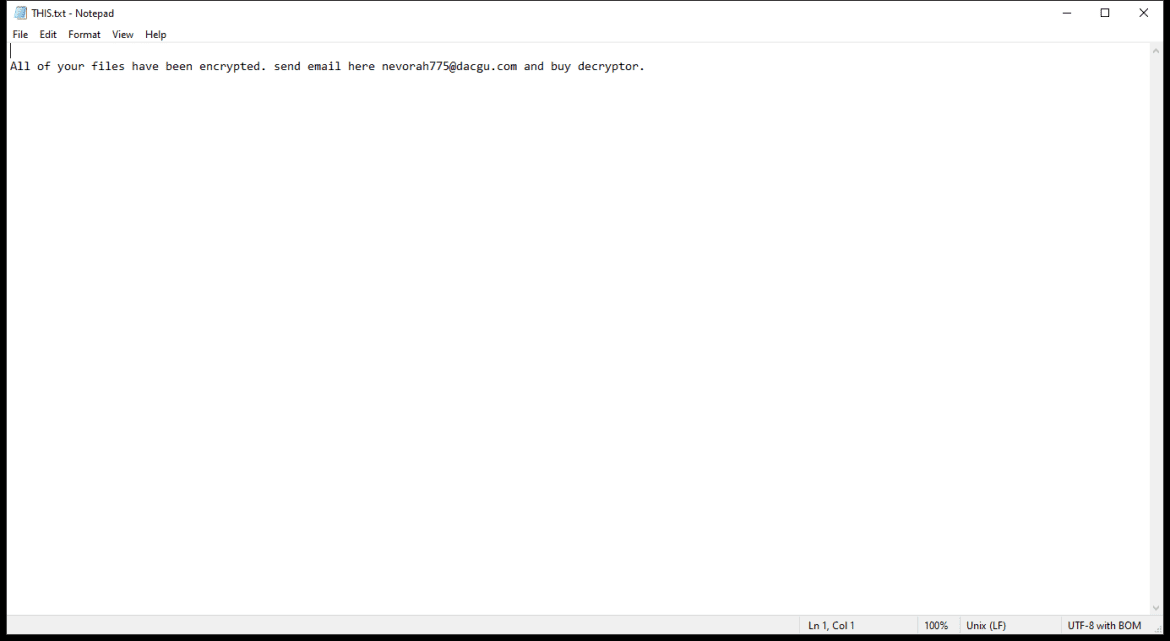
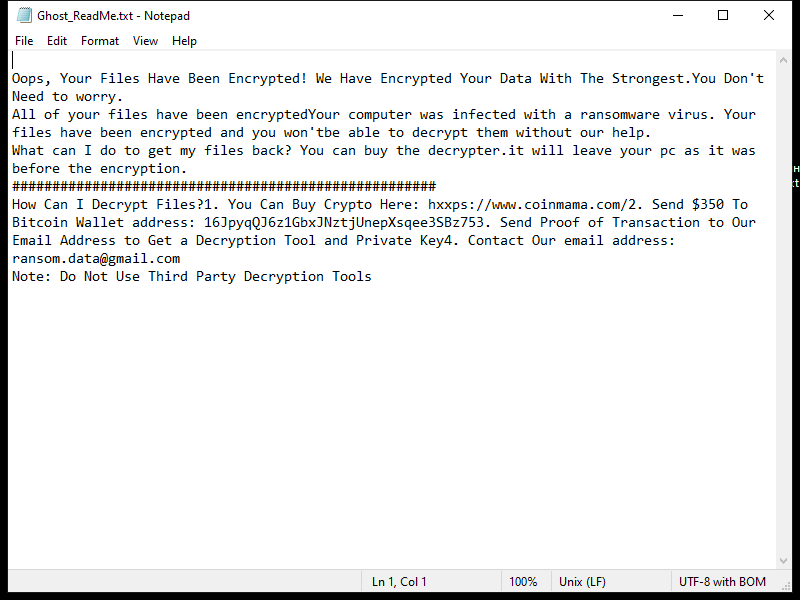
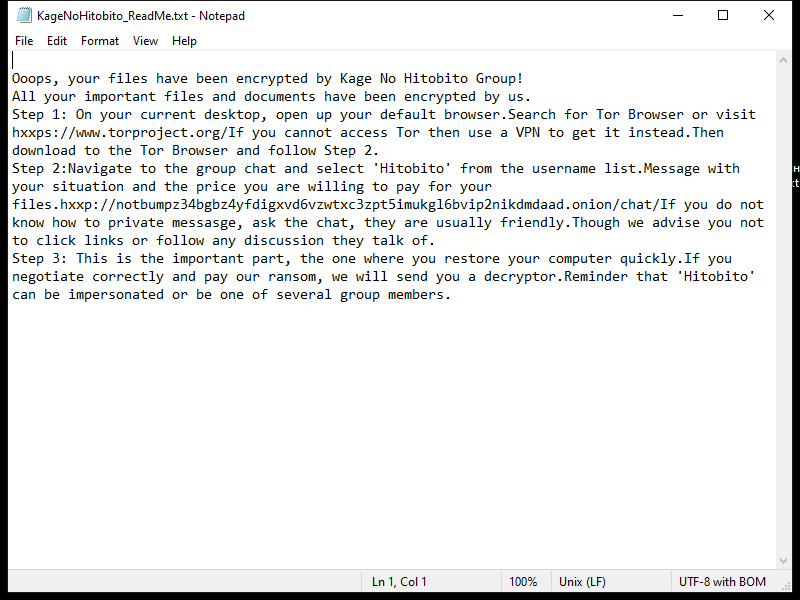
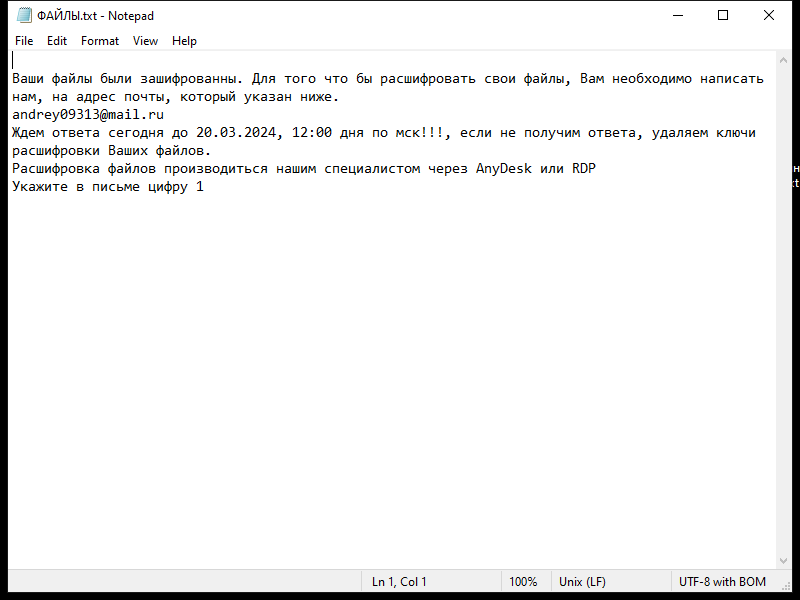
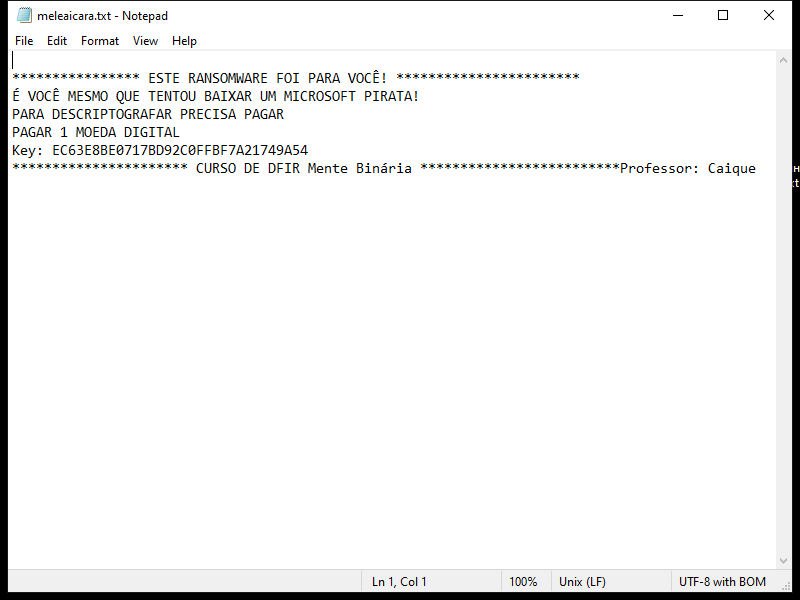
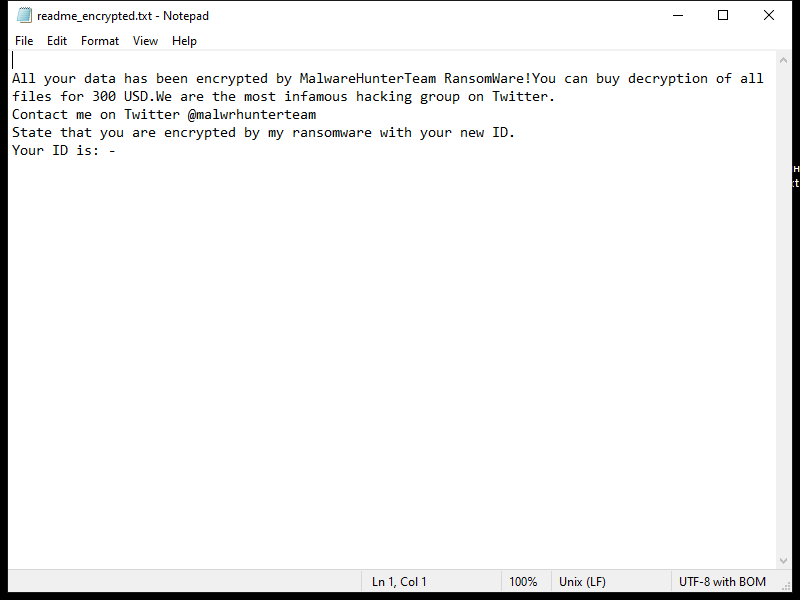
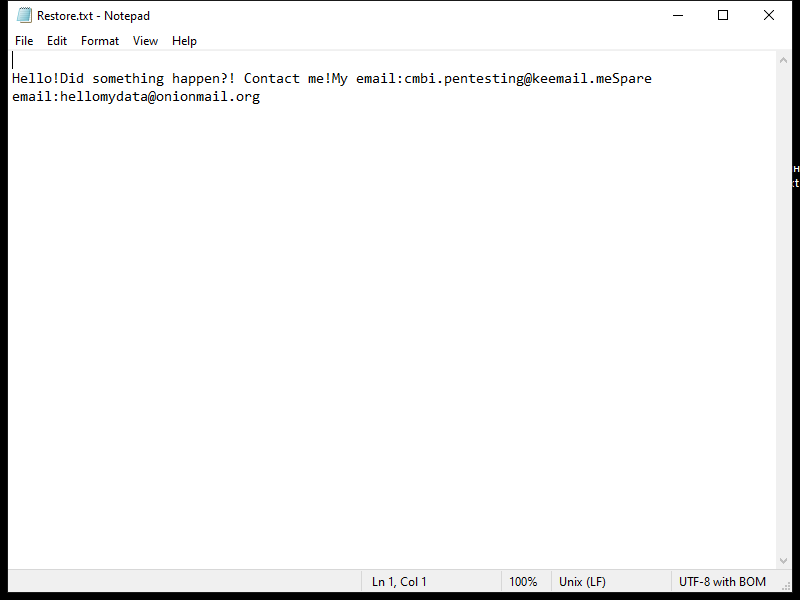
After encrypting the files, Napoli Ransomware creates a ransom note that usually appears on the desktop or in folders containing encrypted files. The note contains instructions on how to pay the ransom and receive the decryption key.
As of now, there are no known decryption tools for Napoli Ransomware. However, victims are advised not to pay the ransom as there is no guarantee that the attackers will provide the decryption key after receiving the payment.
In some cases, security researchers may develop decryption tools for certain ransomware variants, so it is recommended to regularly check reputable sources for updates on decryption options. Additionally, victims can try restoring their files from backups or using data recovery tools to recover their files without paying the ransom.