HWABAG Ransomware is a type of malicious software that encrypts files on a computer, making them inaccessible to the user. It typically infects computers through phishing emails, malicious websites, or exploiting vulnerabilities in software.
When HWABAG Ransomware infects a computer, it adds a specific file extension to encrypted files, such as “.hwabag“. It uses strong encryption algorithms, such as AES or RSA, to encrypt the files, making it virtually impossible to decrypt them without the encryption key.
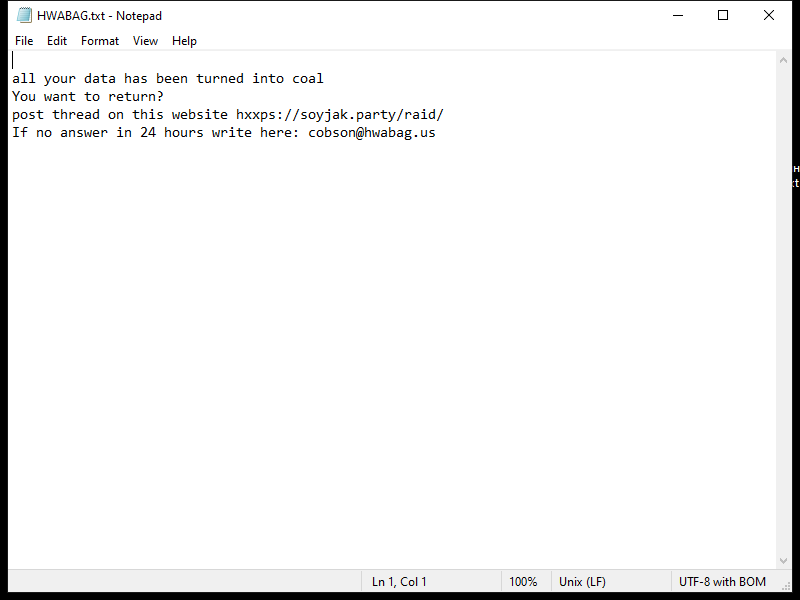
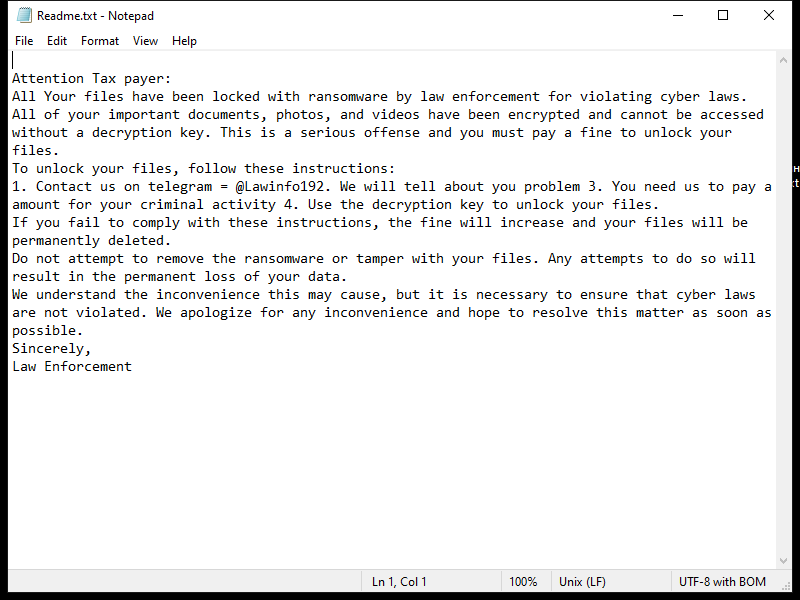
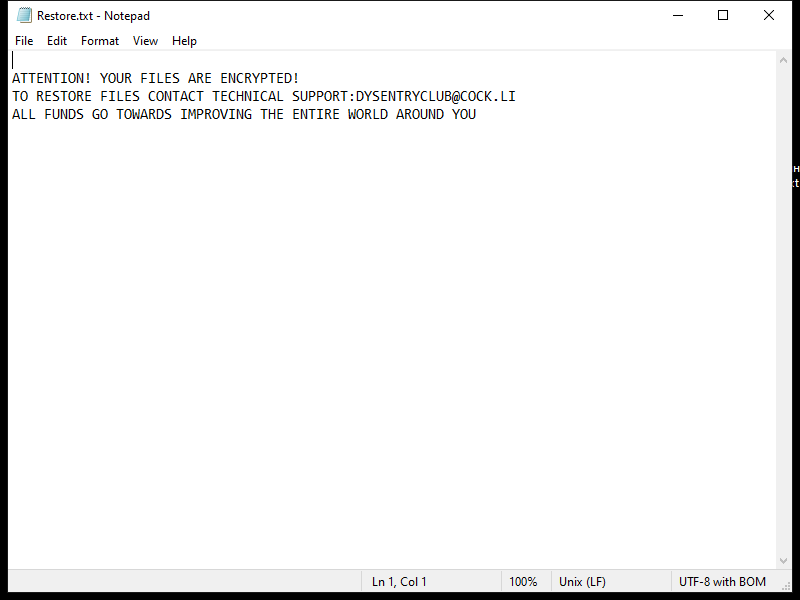
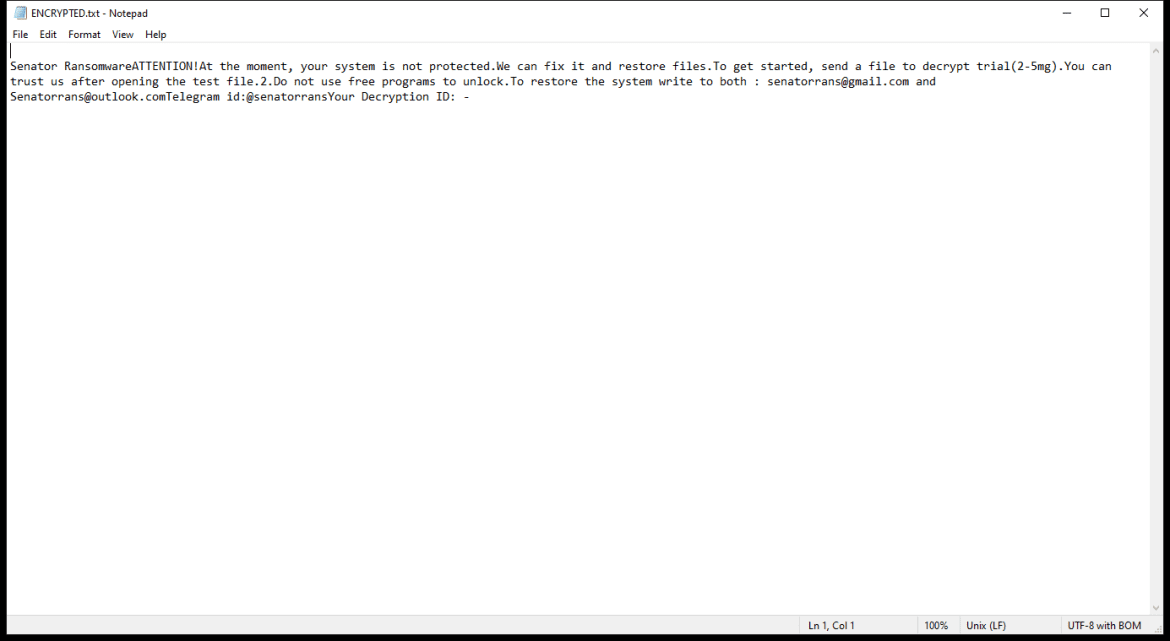
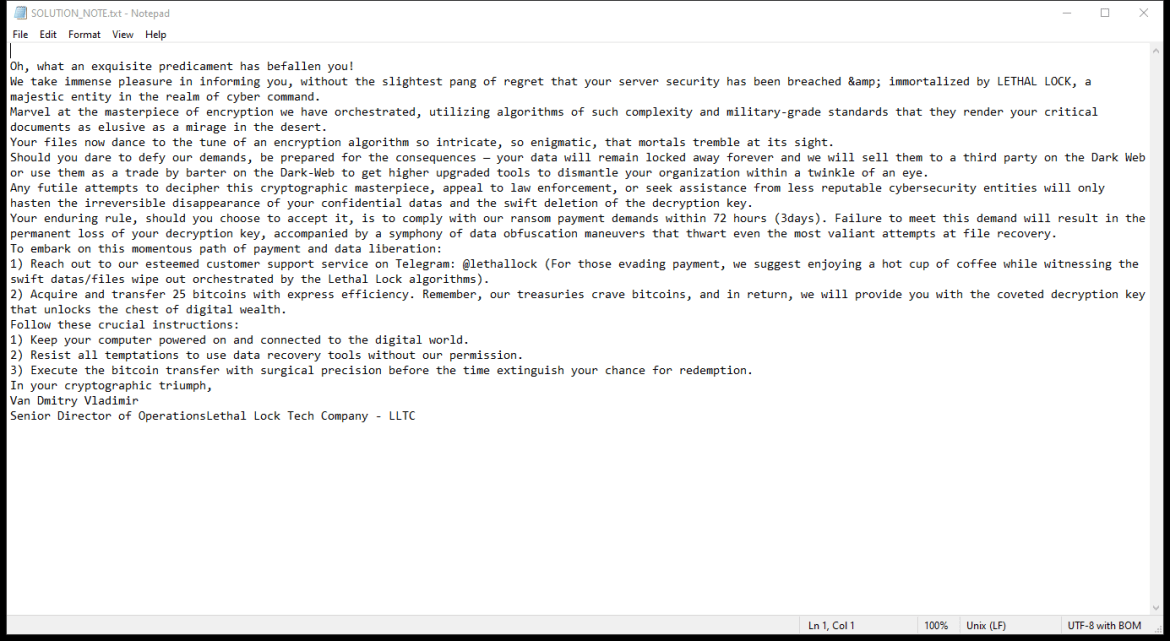
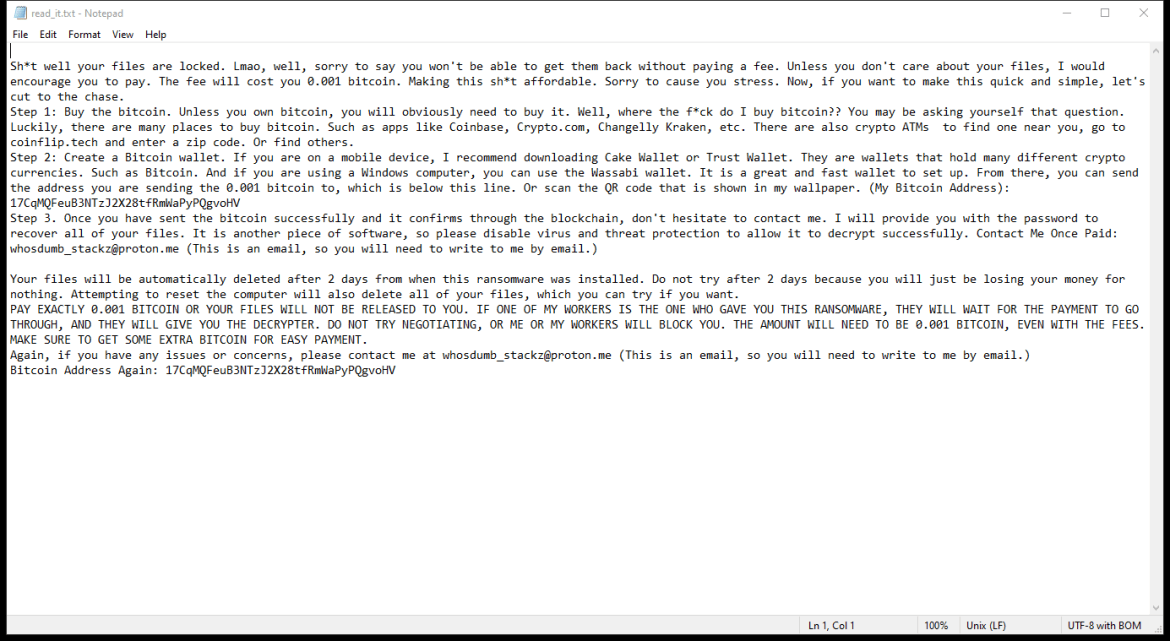
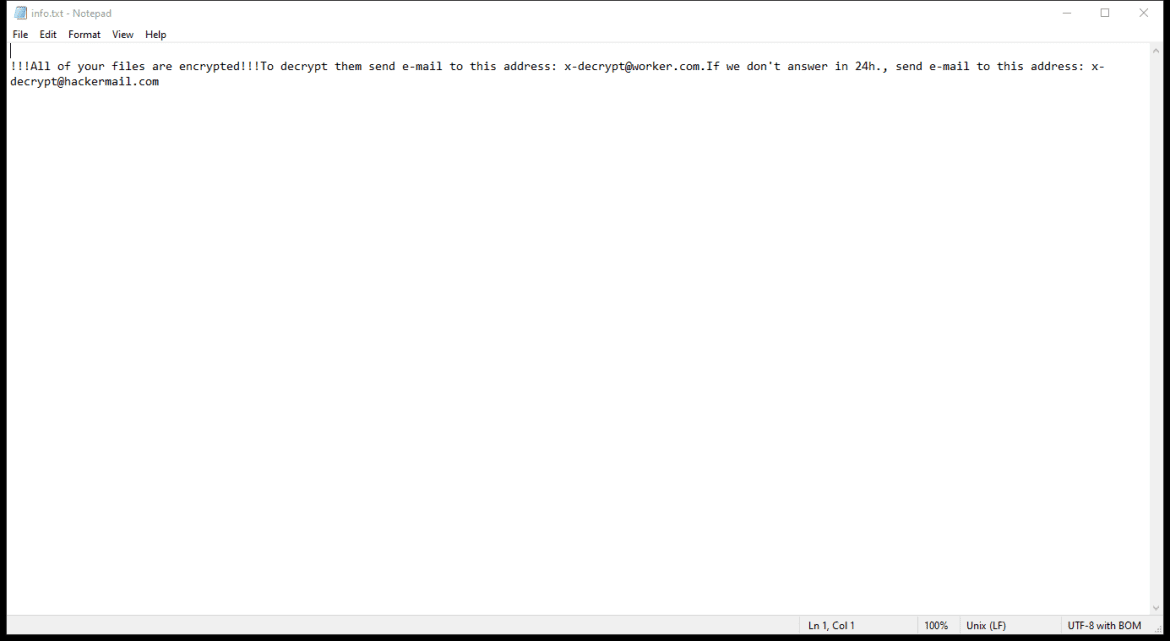
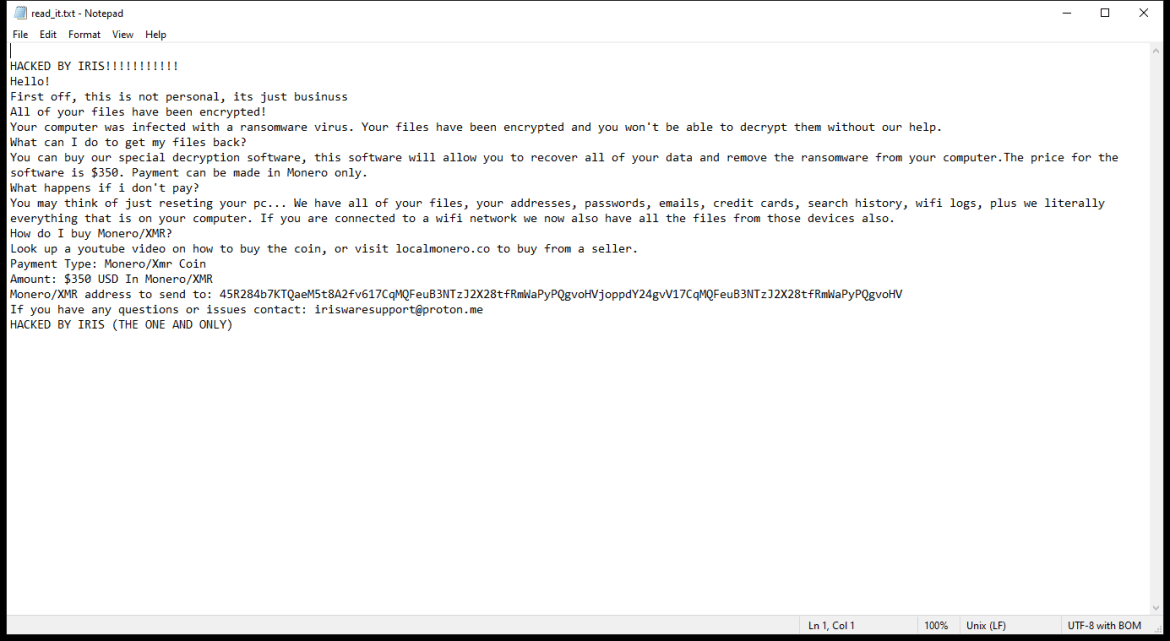
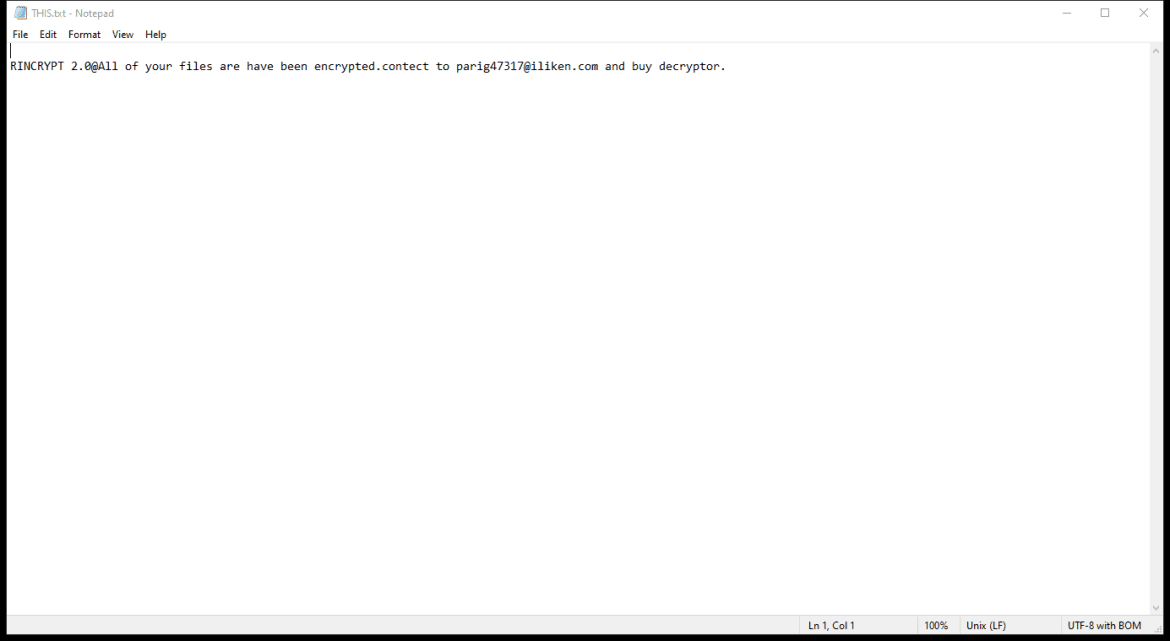
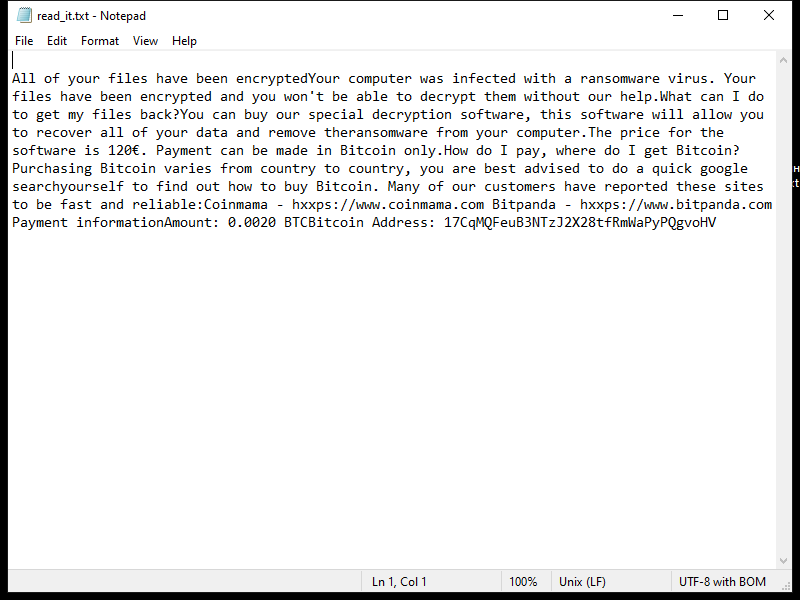
After encrypting the files, HWABAG Ransomware creates a ransom note on the desktop or in the folders containing the encrypted files. The ransom note usually contains instructions on how to pay the ransom to get the decryption key.
As of now, there are no decryption tools available for decrypting .hwabag files. The best way to recover your files is to restore them from a backup if you have one. It’s important to regularly backup your files to prevent data loss in case of a ransomware attack.