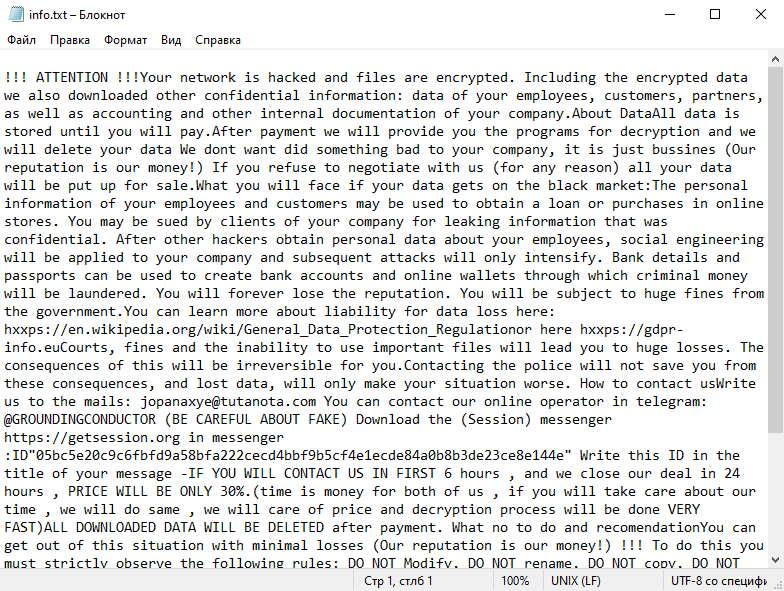
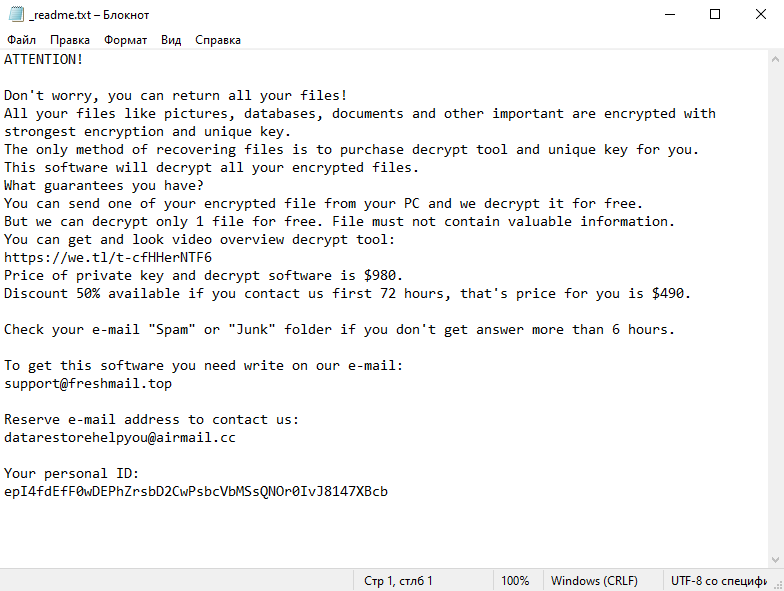
Secles Ransomware is a type of malicious software that infects computers and encrypts files, demanding a ransom from the victim to regain access to the files. Below are answers to your specific questions without references or links:
1. Infection Method: Secles Ransomware usually infects computers through deceptive email attachments, malicious downloads, or exploiting vulnerabilities in outdated software.
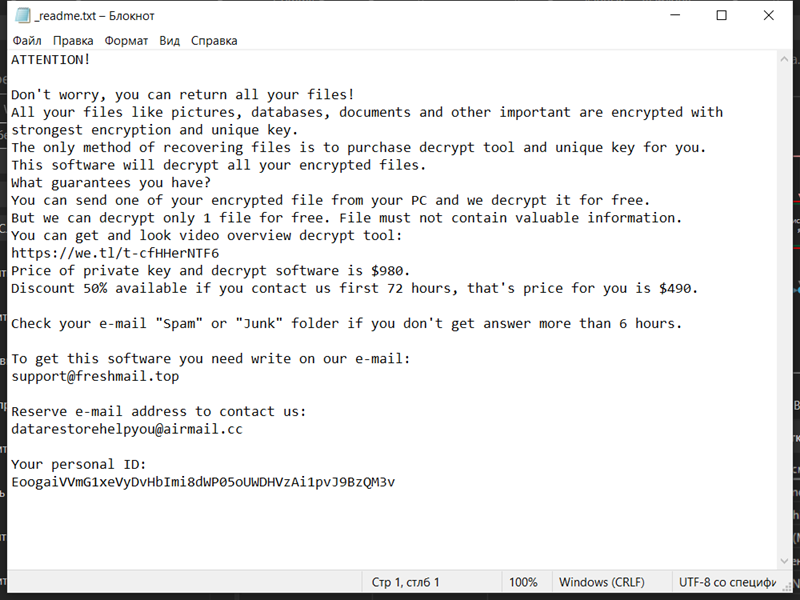
2. File Extensions: Secles Ransomware appends a “.secles” extension to the encrypted files. For example, a file named “document.txt” would become “document.txt.secles” after encryption.
3. File Encryption: Secles Ransomware employs a strong encryption algorithm (such as AES or RSA) to encrypt the files, making them inaccessible without the decryption key.
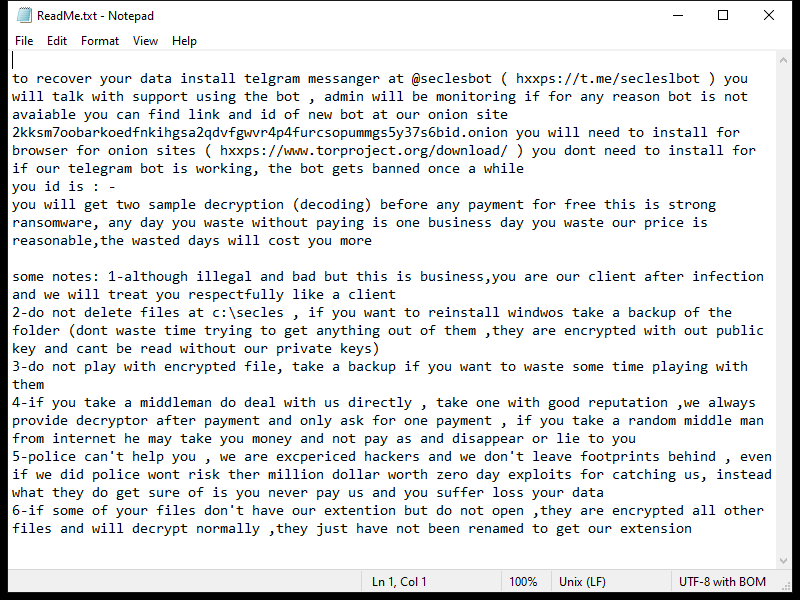
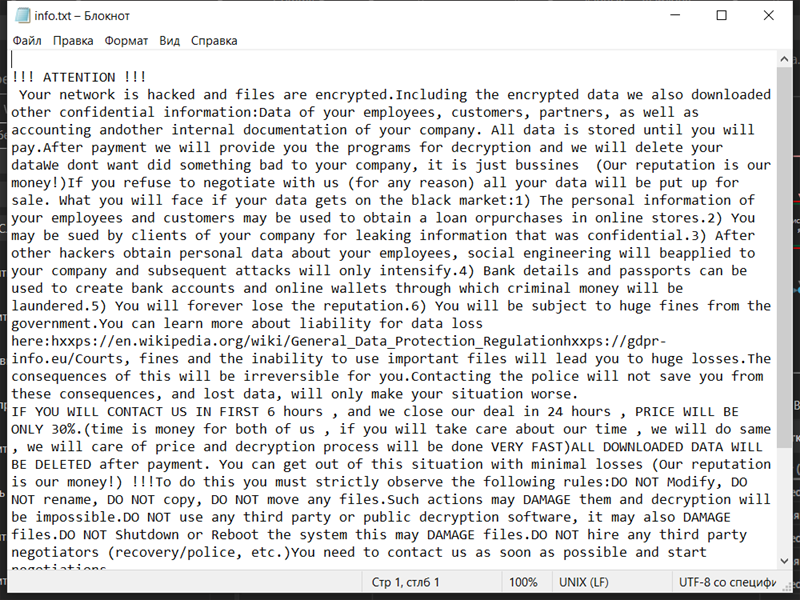
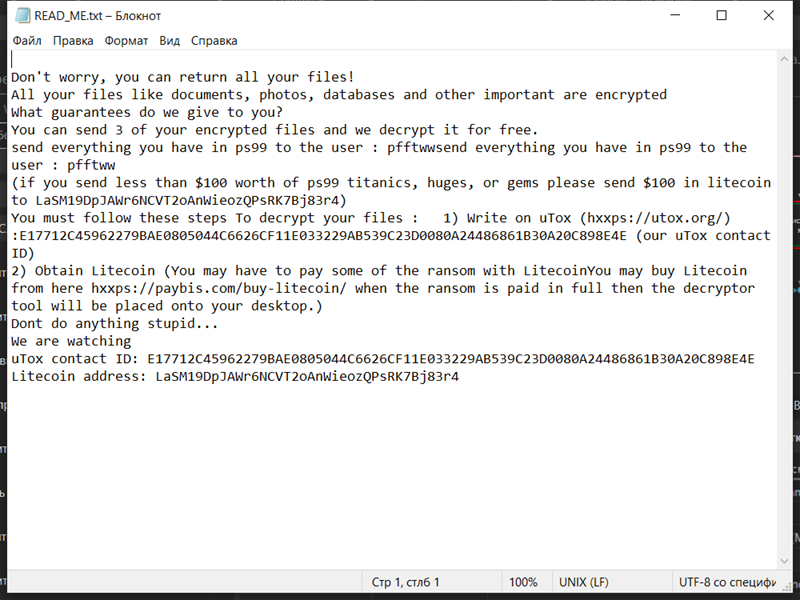
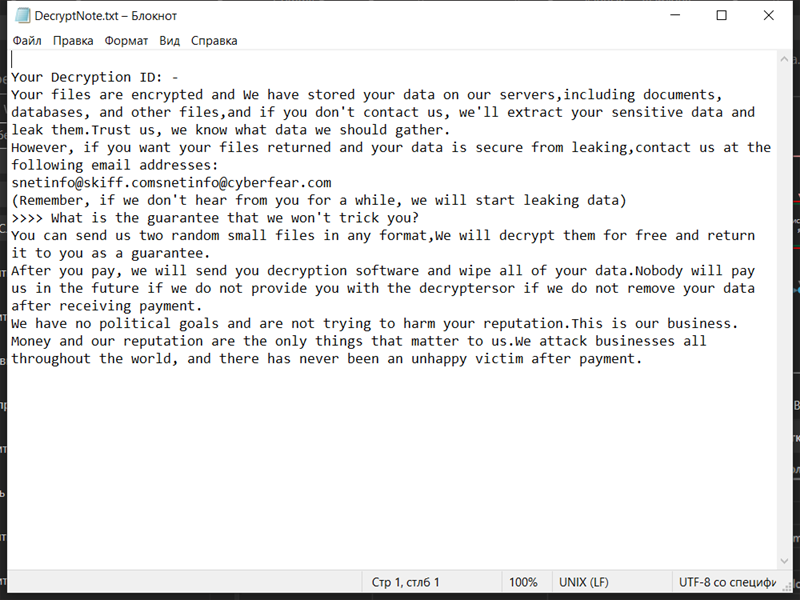
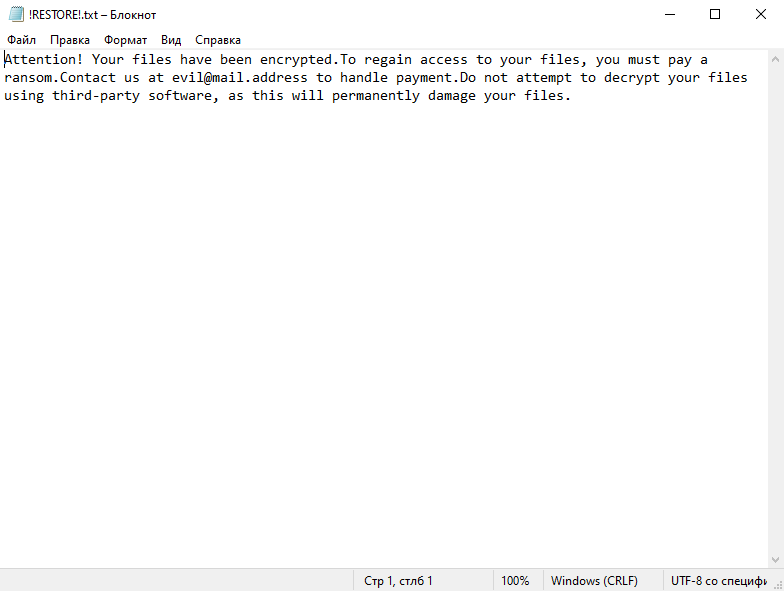
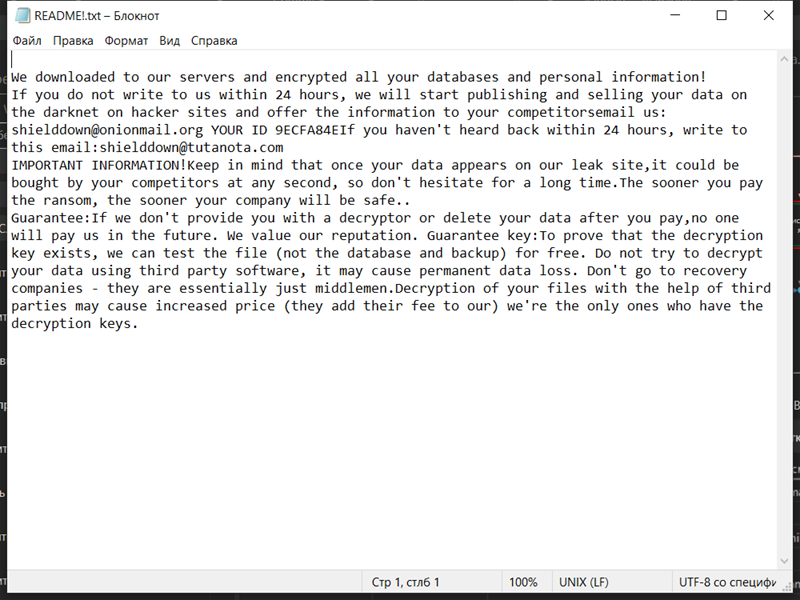
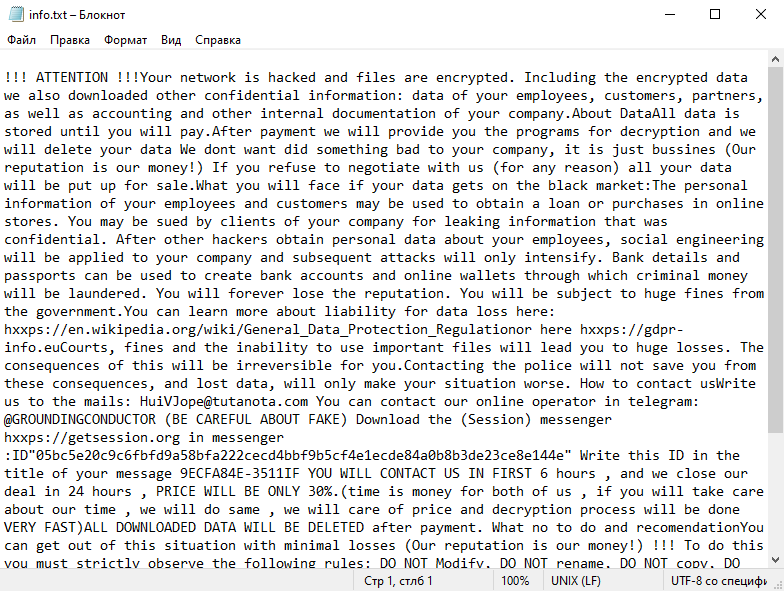
4. Ransom Note: The ransomware creates a text file (usually named “README.txt” or “HOW-TO-DECRYPT.txt”) containing instructions on how to pay the ransom and obtain the decryption key. It is typically placed in multiple directories or on the desktop.
5. Decryption Tools: At the time of this response, there are no known decryption tools available for Secles Ransomware. It is recommended to avoid paying the ransom, as it does not guarantee file recovery and may encourage further criminal activities.
6. Decrypting .Secles Files: Without a decryption tool, restoring files encrypted by Secles Ransomware can be challenging. However, there are a few potential methods to try:
– Restore files from a backup if you have regularly backed up your data.
– Check if security researchers or antivirus companies have released any decryption tools specific to Secles Ransomware.
– Consult with a professional cybersecurity firm for possible decryption solutions.
Please note that dealing with ransomware requires expertise, and it is crucial to take preventive measures like regularly backing up your files and maintaining up-to-date security software to avoid such infections.