How to remove T.ajump2.com
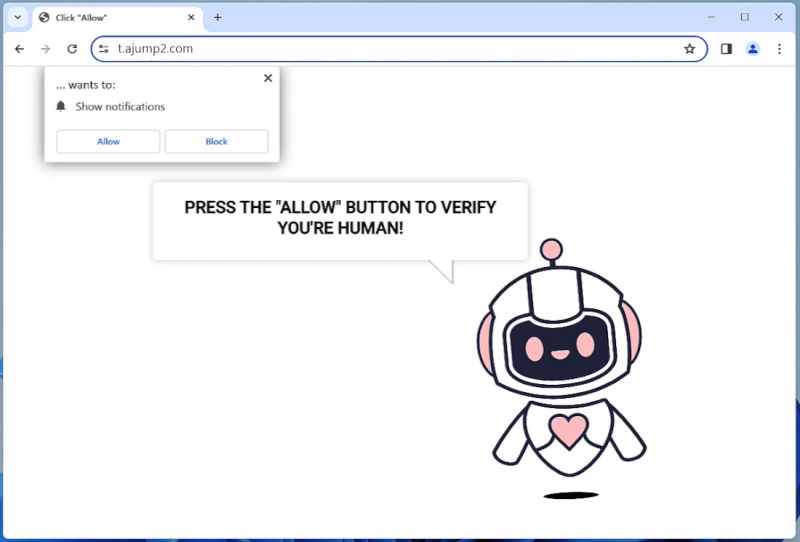
T.ajump2.com is a malicious website that infects computers by tricking users into allowing browser notifications. This typically happens when a user visits a compromised website or clicks on a malicious link, which prompts a notification asking for permission to show notifications from T.ajump2.com. Once granted, the website can then display intrusive and potentially harmful pop-up notifications on the user’s browser.
T.ajump2.com exploits browser notifications to push unwanted ads, fake software updates, or even redirect users to phishing websites. It can infect a wide range of browsers, including Chrome, Firefox, and Safari, on various devices such as desktop computers, laptops, and mobile phones. Users should be cautious when granting permission for browser notifications and should always be wary of suspicious websites that request such permissions.