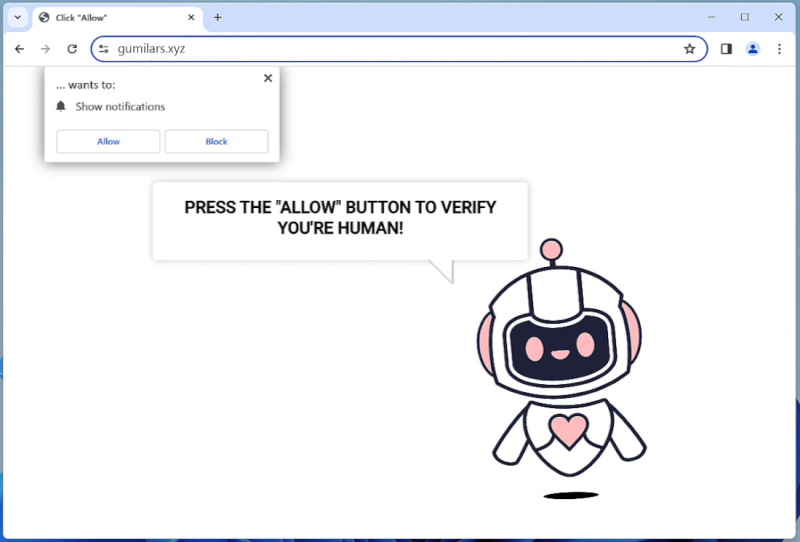
How to remove Gumilars.xyz
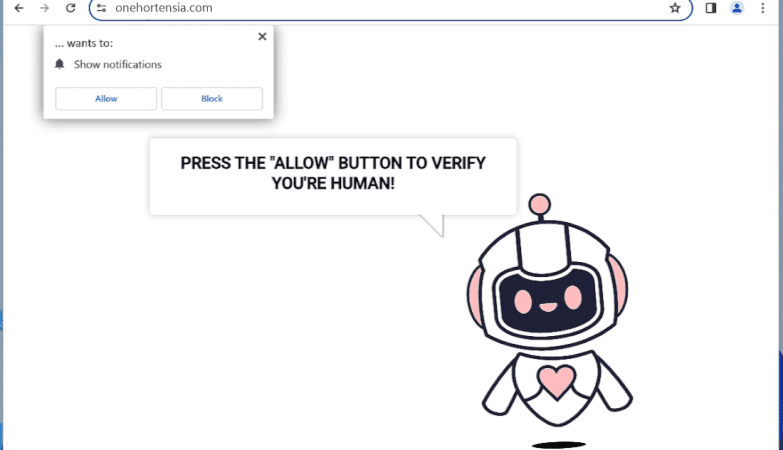
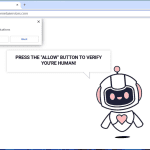
Gumilars.xyz is a malicious website that is known for infecting computers with adware and potentially unwanted programs (PUPs). It typically spreads through deceptive advertising, fake software updates, or bundled with other software downloads. Once a user visits the website, they may be prompted to allow notifications, which can then lead to a barrage of unwanted pop-up ads and notifications on their browsers.
The website exploits browser notifications by tricking users into subscribing to them, claiming that it is necessary to access certain content or download a file. Once granted permission, the site can then push out unwanted notifications that contain misleading or malicious content. Gumilars.xyz primarily targets popular browsers like Google Chrome, Mozilla Firefox, and Safari, and can infect both Windows and Mac devices. It is important for users to be cautious when browsing unfamiliar websites and to avoid clicking on suspicious links or allowing notifications from unknown sources to prevent infections from sites like Gumilars.xyz.