How to remove Dynamitedojo.com
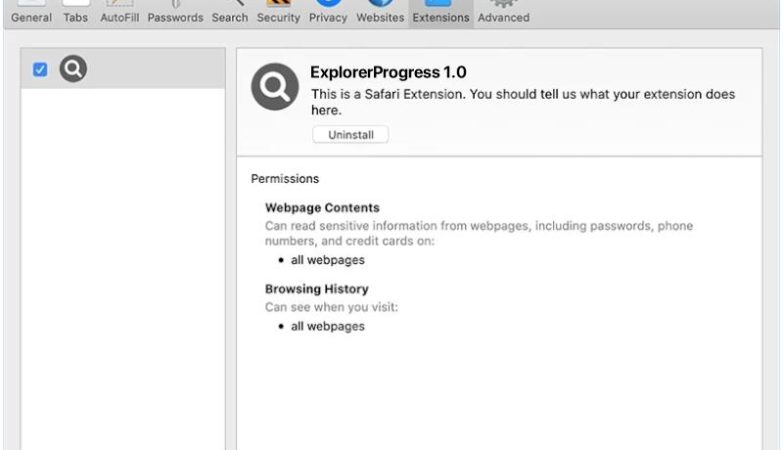
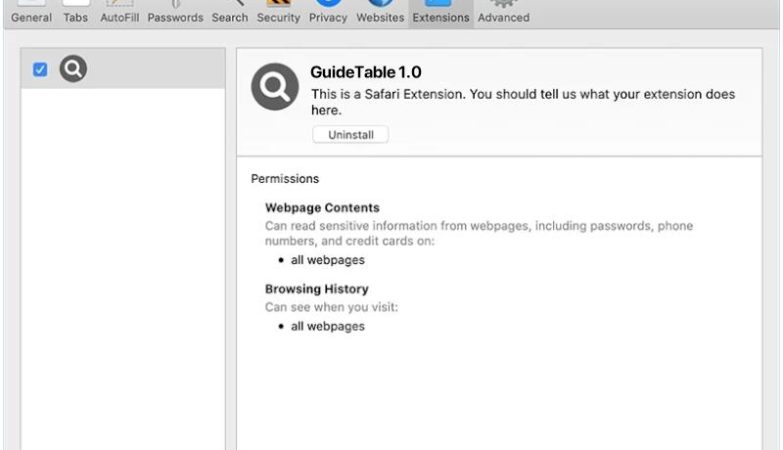
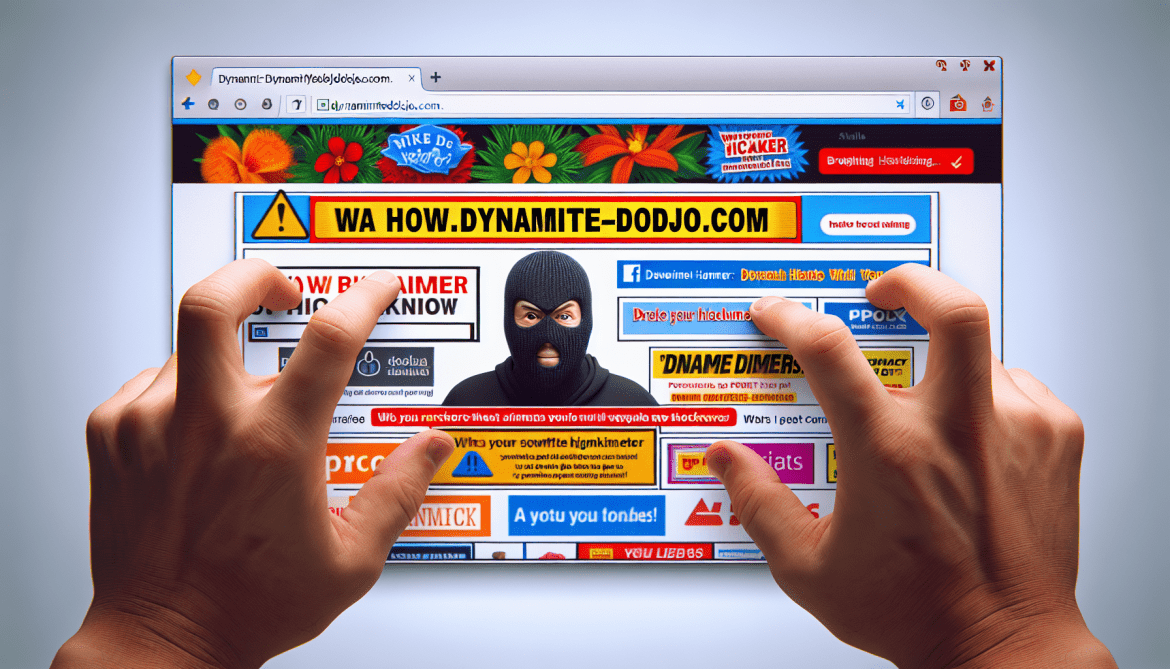
Dynamitedojo.com is a type of adware that is designed to display unwanted and intrusive advertisements on a user’s computer or browser. These ads can appear in the form of pop-ups, banners, or in-text links, and can be very disruptive to the user’s browsing experience. Dynamitedojo.com adware is often bundled with other software or downloaded unknowingly by the user, making it difficult to detect and remove.
Dynamitedojo.com typically infects computers and browsers through deceptive methods, such as through freeware or shareware downloads, fake software updates, or malicious websites. Once installed, the adware can track the user’s browsing habits and display targeted ads based on their interests. Dynamitedojo.com can also collect sensitive information such as browsing history, search queries, and even personal data, putting the user’s privacy at risk.