How to remove Moderton.com
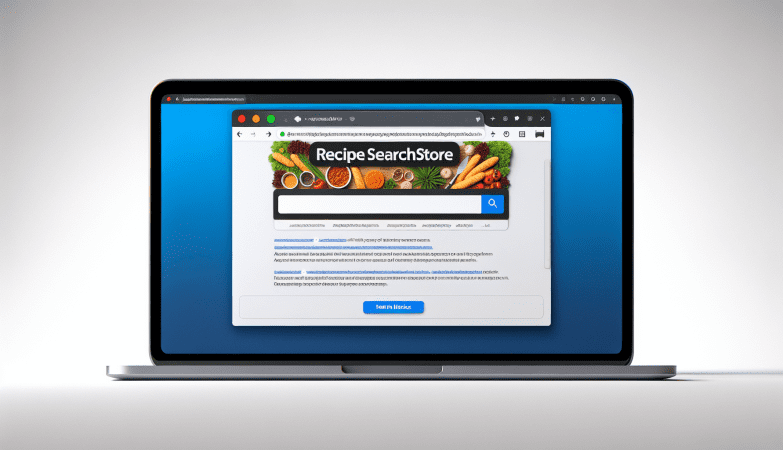
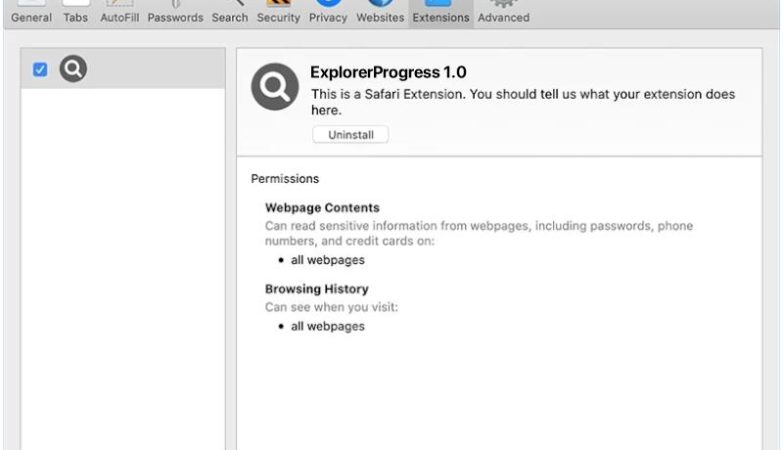
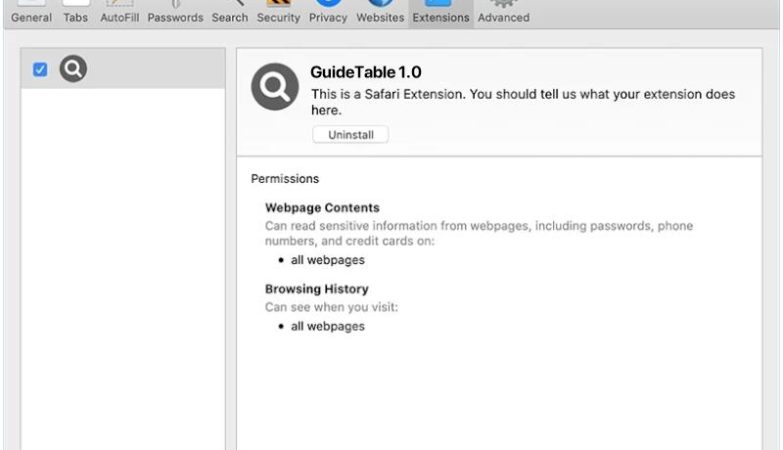
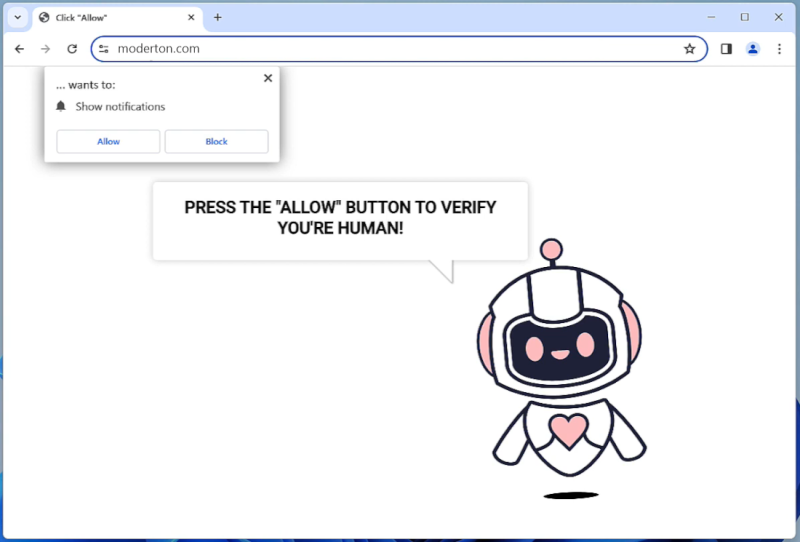
Moderton.com is a malicious website that infects computers by tricking users into allowing notifications through their web browser. Once permission is granted, the website bombards the user with unwanted notifications that can contain malicious links or advertisements. These notifications can be very difficult to get rid of, as they continue to pop up even after closing the browser.
Moderton.com exploits browser notifications by using social engineering tactics to deceive users into clicking on the “Allow” button. The website may claim that notifications are necessary to access certain content or that they are required for security reasons. Once permission is granted, Moderton.com can continue to send notifications even when the browser is closed. This can be very annoying and disruptive for users, as well as potentially exposing them to malware or other online threats. Moderton.com can infect various web browsers such as Google Chrome, Mozilla Firefox, and Safari, and it can target devices running on Windows, MacOS, Android, and iOS. Users should be cautious when visiting unfamiliar websites and avoid granting unnecessary permissions to prevent falling victim to this type of malware.