How to remove Internationalen Lotteriekommission pop-ups
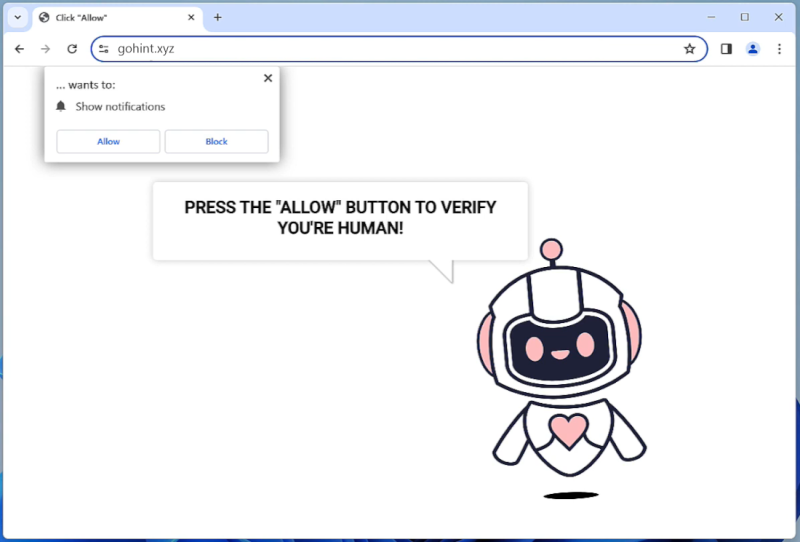
The Internationalen Lotteriekommission, also known as the International Lottery Commission, is an organization that claims to conduct international lotteries and award cash prizes to winners. However, it is important to note that the Internationalen Lotteriekommission is not a legitimate or recognized lottery authority.
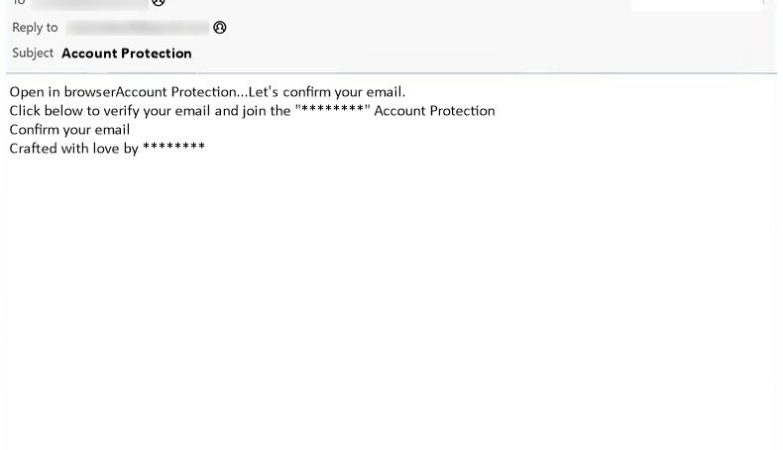
The appearance of the Internationalen Lotteriekommission in browsers is often associated with online scams or fraudulent activities. Users may encounter pop-up windows or advertisements claiming that they have won a substantial amount of money in an international lottery organized by the Internationalen Lotteriekommission. These messages often request personal information, such as bank account details or payment of fees, in order to process the supposed winnings. However, providing such information can lead to identity theft or financial losses, as the organization is not genuine and there is no actual lottery taking place. It is important to be cautious and skeptical of any claims made by the Internationalen Lotteriekommission or similar entities that appear unexpectedly in browsers.

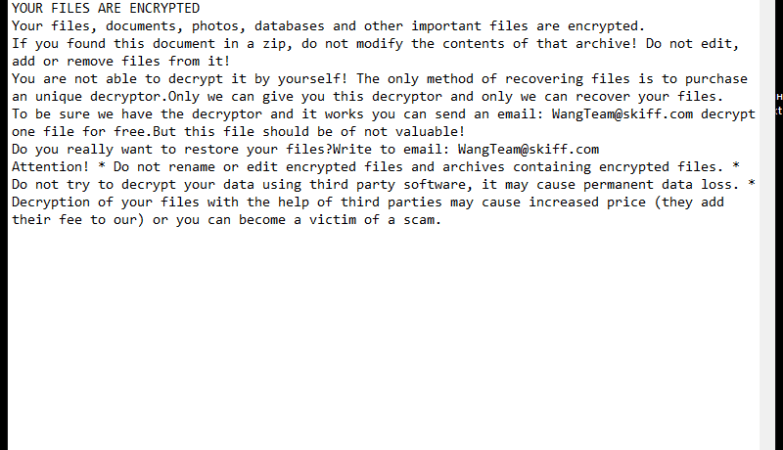





![How to remove Win32:Ransomx-Gen [Ransom]](https://malwarewarrior.com/wp-content/uploads/2024/02/win32-ransomx-gen-ransom--1170x669.png)