What is Cheetah ransomware
Cheetah is a dangerous crypto-virus, that is created with the purpose of blackmailing people. The virus is trying to infiltrate victim’s system with the help of trojans, botnets, exploits and infected spam emails attachments. When the virus successfully infiltrates user’s computer, it will immediately run its malicious processes and start the encryption procedure. It will use AES encryption algorithm to encipher all victim’s data, so that these files can not be used or accessed until they are decrypted. The decryption key may unlock all the data and that is exactly why cyber criminals will offer their deal – money in exchange for decryption key. The cost of decryption may be terrifically huge. If you got this virus on your computer, we recommend you to use our guide in order to remove Cheetah ransomware and decrypt .cheetah files.

Cheetah ransomware adds .cheetah to the name of all the encrypted files. When the encoding process is over, a victim will find out that the files can’t be opened anymore: work documents, any other texts, presentations, photos, videos, databases. Once all the data is encrypted, the ransomware will drop How to recover your files.txt file, the ransom note:
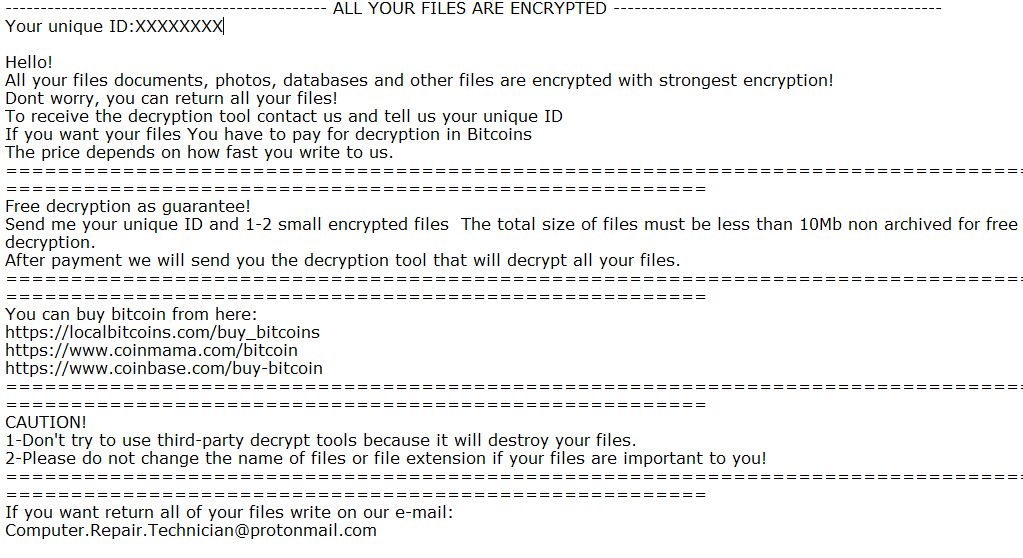
———————————————- ALL YOUR FILES ARE ENCRYPTED ———————————————–
Your unique ID:XXXXXXXX
Hello!
All your files documents, photos, databases and other files are encrypted with strongest encryption!
Dont worry, you can return all your files!
To receive the decryption tool contact us and tell us your unique ID
If you want your files You have to pay for decryption in Bitcoins
The price depends on how fast you write to us.
========================================================================================================================================
Free decryption as guarantee!
Send me your unique ID and 1-2 small encrypted files The total size of files must be less than 10Mb non archived for free decryption.
After payment we will send you the decryption tool that will decrypt all your files.
========================================================================================================================================
You can buy bitcoin from here:
https://localbitcoins.com/buy_bitcoins
https://www.coinmama.com/bitcoin
https://www.coinbase.com/buy-bitcoin
========================================================================================================================================
CAUTION!
1-Don’t try to use third-party decrypt tools because it will destroy your files.
2-Please do not change the name of files or file extension if your files are important to you!
========================================================================================================================================
If you want return all of your files write on our e-mail:Computer.Repair.Technician@protonmail.com
There are two solutions of this problem. First is to use special Removal Tool. Removal Tools delete all instances of malware by few clicks and help user to save time. Or you can use Manual Removal Guide, but you should know that it might be very difficult to remove Cheetah ransomware manually without specialist’s help.
Cheetah Removal Guide
- Download Cheetah Removal Tool.
- Remove Cheetah from Windows (7, 8, 8.1, Vista, XP, 10) or Mac OS (Run system in Safe Mode).
- How to restore files
- How to protect PC from future infections.
How to remove Cheetah ransomware automatically:
This anti-ransomware removal tool is able to detect and remove Cheetah ransomware from your system with all leftovers.
Manual Cheetah Removal Guide
Here is step-by-step instructions to remove Cheetah from Windows and Mac computers. Follow this steps carefully and remove files and folders belonging to Cheetah. First of all, you need to run system in a Safe Mode. Then find and remove needed files and folders.
Uninstall Cheetah from Windows or Mac
Here you may find the list of confirmed related to the ransomware files and registry keys. You should delete them in order to remove virus, however it would be easier to do it with our automatic removal tool. The list:
test.exe
bedoneupx.exe
How to recover your files.txt
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Cheetah by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Cheetah by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Cheetah by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Cheetah by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple logo appears;
- Find programs or files potentially related to Cheetah by using Removal Tool;
- Delete found files;
How to restore encrypted files
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
Stellar Data Recovery is able to find and restore different types of encrypted files, including removed emails.
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Restore encrypted files using Recuva
There is an alternative program, that may help you to recover files – Recuva.
- Run the Recuva;
- Follow instructions and wait until scan process ends;
- Find needed files, mark them and Press Recover button;
How to prevent ransomware infection?
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
Malwarebytes
SpyHunter is a reliable antimalware removal tool application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.

