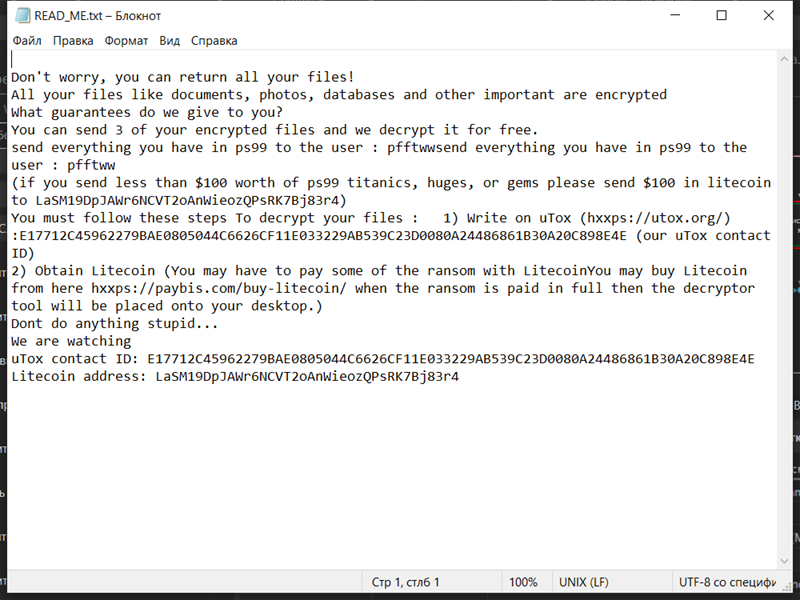
Wessy Ransomware is a type of malicious software that infects computers and encrypts files, making them inaccessible to the user. Here are some details about Wessy Ransomware:
1. Infection Method: Wessy Ransomware primarily spreads through malicious email attachments, software cracks, or fake software updates. It may also exploit vulnerabilities in outdated software or use social engineering techniques to trick users into downloading and executing the malware.
2. File Extensions: Wessy Ransomware appends the “.wessy” extension to the encrypted files. For example, a file named “document.docx” will be renamed to “document.docx.wessy” after encryption.
3. Encryption Algorithm: It is not publicly known what encryption algorithm Wessy Ransomware uses. However, most ransomware variants employ strong encryption algorithms like AES or RSA to secure the files.
4. Ransom Note: Wessy Ransomware creates a ransom note in the form of a text file or a pop-up window. The note usually contains instructions on how to pay the ransom to get the decryption key. The exact location and name of the ransom note may vary depending on the variant of Wessy Ransomware.
5. Decryption Tools: At the time of writing, there are no known decryption tools available for Wessy Ransomware. It is always recommended to avoid paying the ransom as there is no guarantee that the attackers will provide the decryption key or that the key will work properly.
6. Decrypting .wessy Files: Unfortunately, without a decryption tool provided by the ransomware authors, it is extremely difficult to decrypt files encrypted by Wessy Ransomware. Your best course of action is to regularly backup your important files and maintain up-to-date antivirus software to protect against such threats.
It is essential to consistently practice good cybersecurity habits like avoiding suspicious emails, keeping software updated, and regularly backing up important data to minimize the risk of ransomware infections.