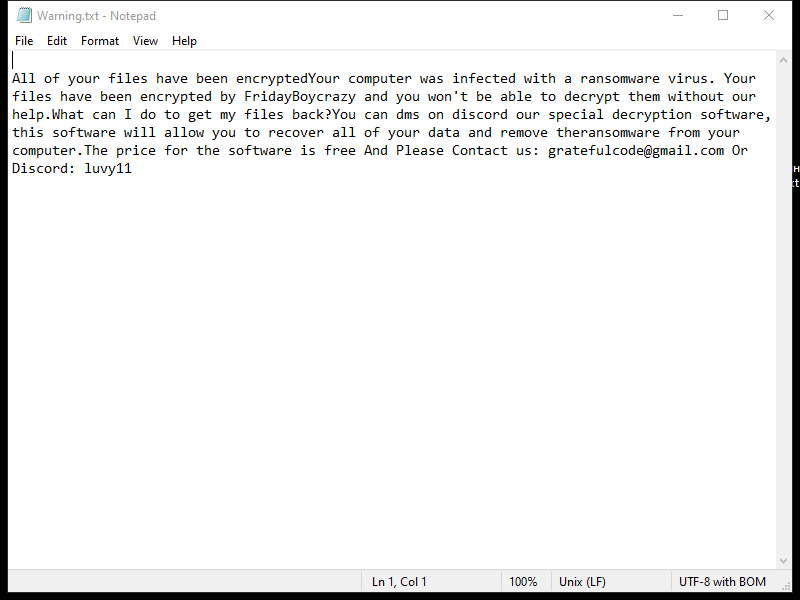
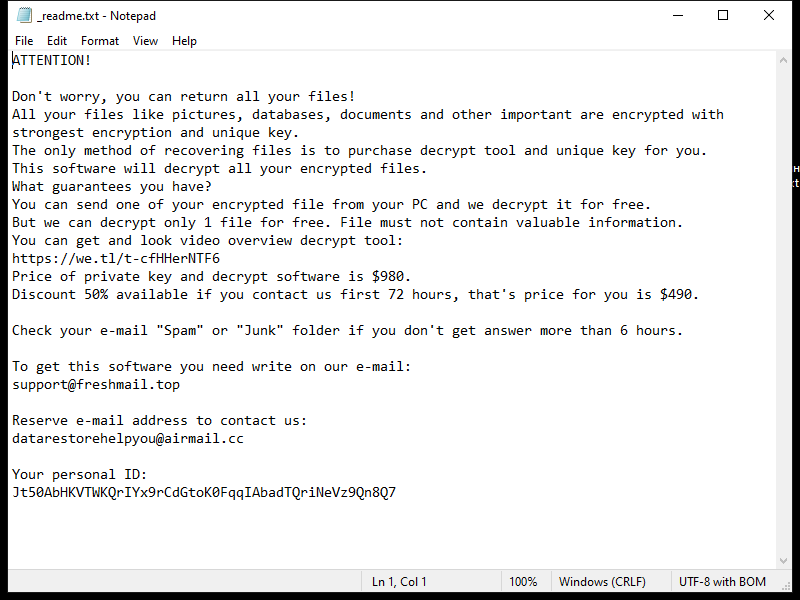
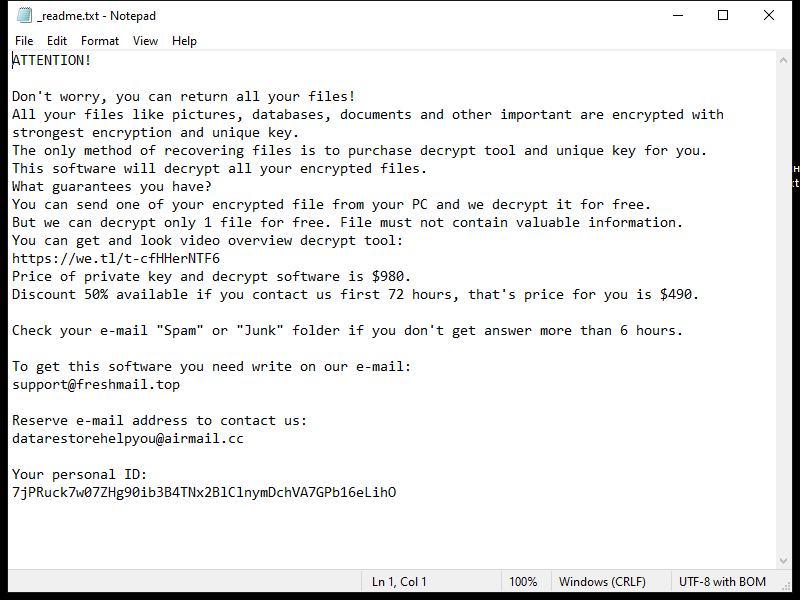
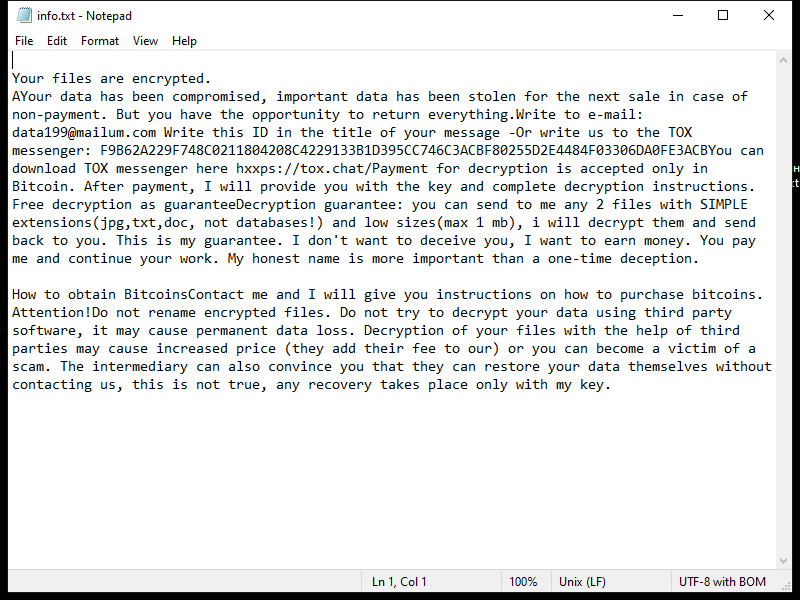
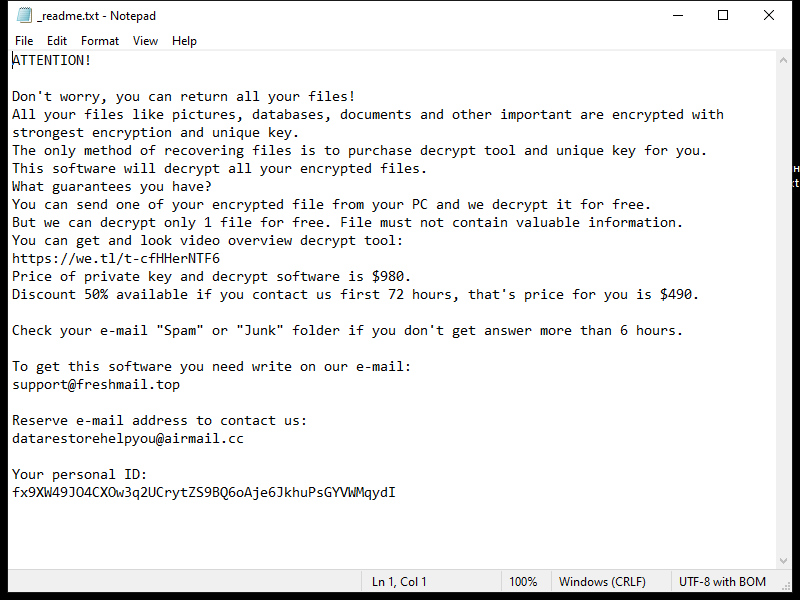
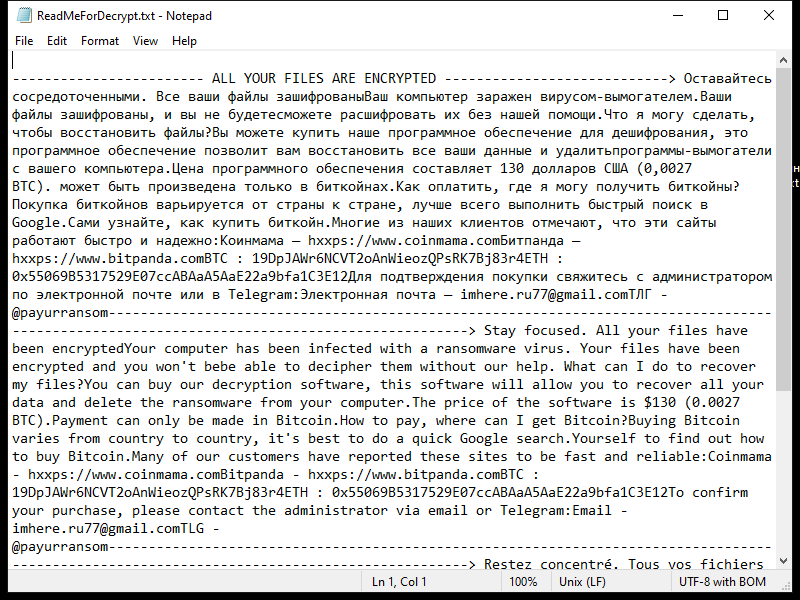
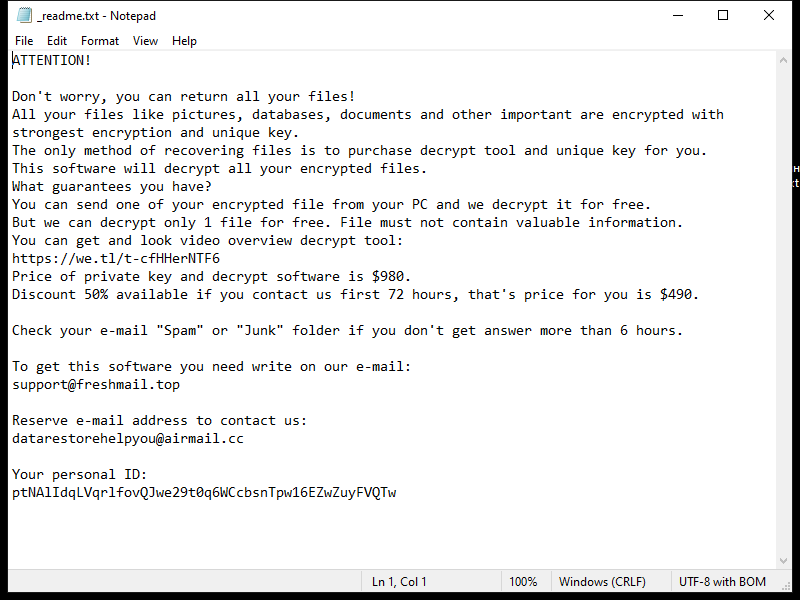
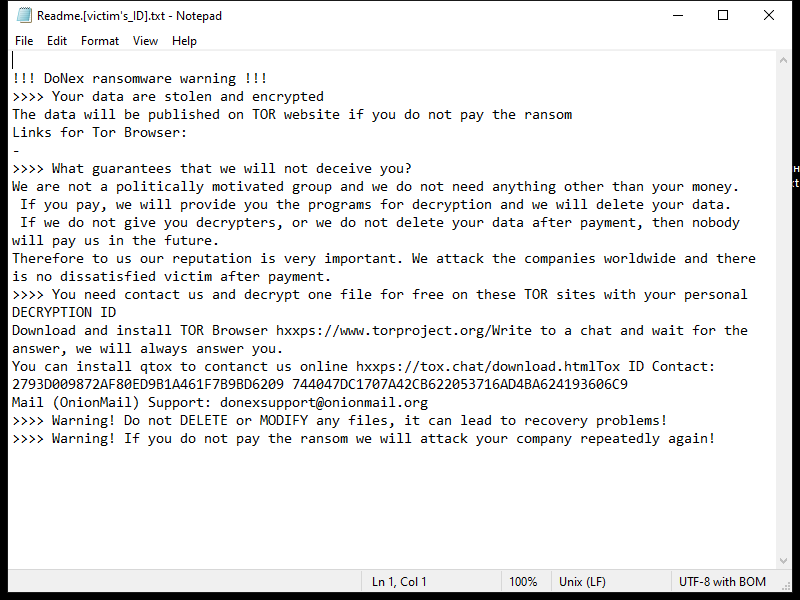
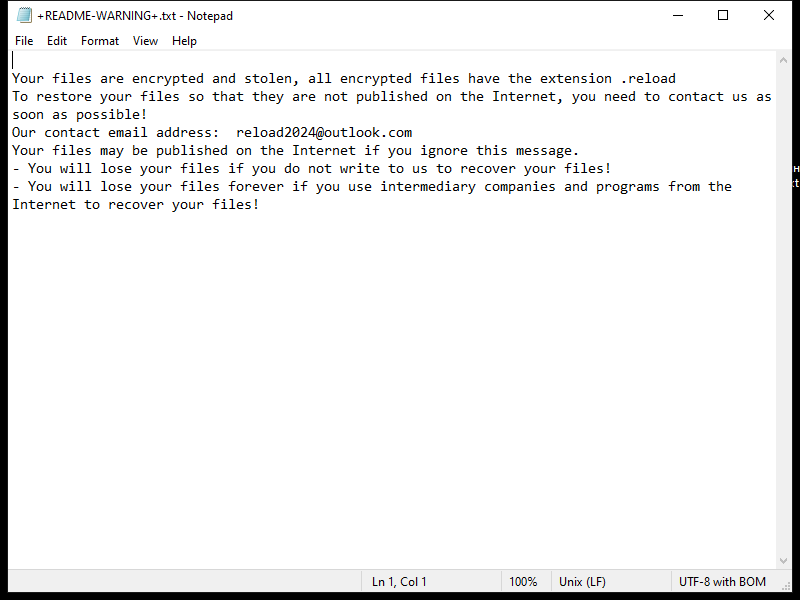
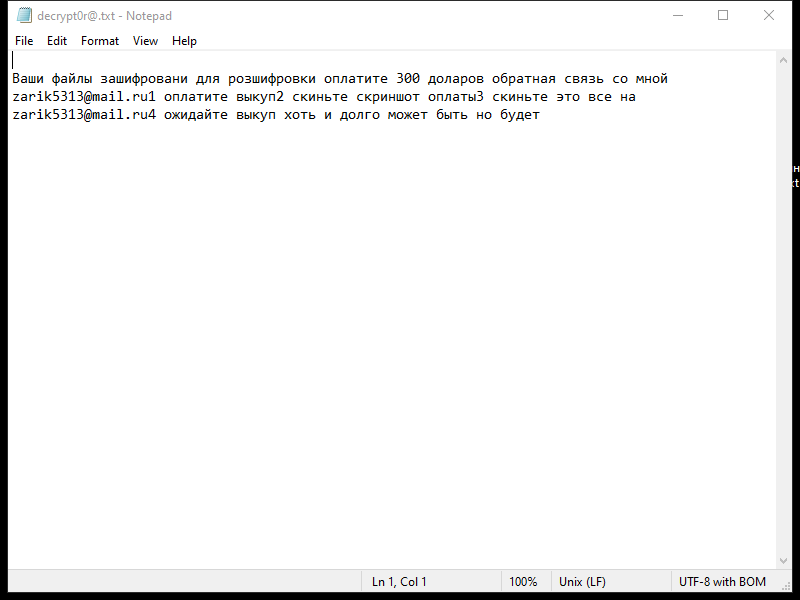
FridayBoycrazy Ransomware is a type of malware that infects computers by exploiting vulnerabilities in the system or tricking users into downloading malicious files. Once installed, it encrypts the files on the infected computer and adds a specific file extension to them, such as “.locked” or “.encrypted”.
The ransomware uses strong encryption algorithms, such as AES or RSA, to lock the files and make them inaccessible to the user. It then creates a ransom note, typically named “README.txt” or “HOW TO DECRYPT FILES.txt”, which contains instructions on how to pay the ransom to get the decryption key.
As of now, there are no decryption tools available for FridayBoycrazy Ransomware. However, there are some methods that may help decrypt random files, such as using data recovery software or trying to restore files from backup if available. It is not recommended to pay the ransom as it does not guarantee that the files will be decrypted, and it only encourages cybercriminals to continue their malicious activities.