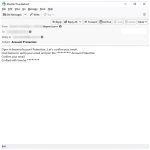
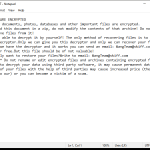
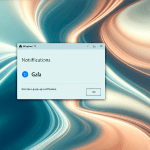
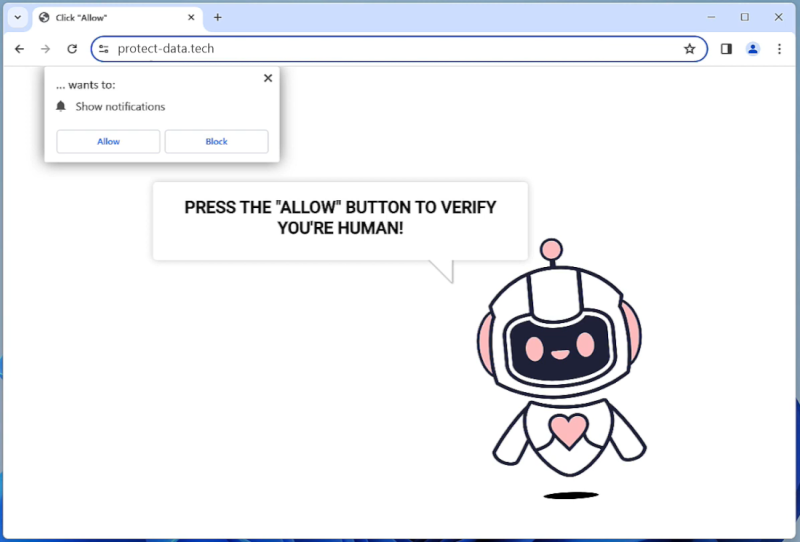
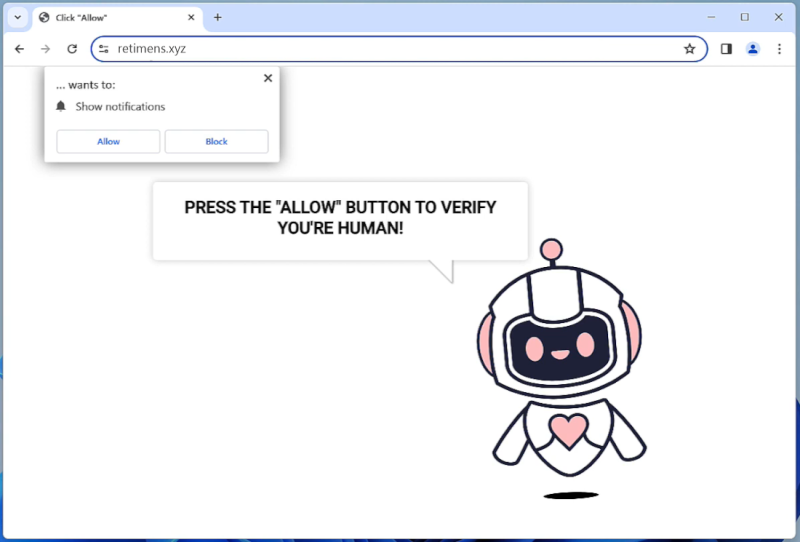
How to remove Protect-data.tech
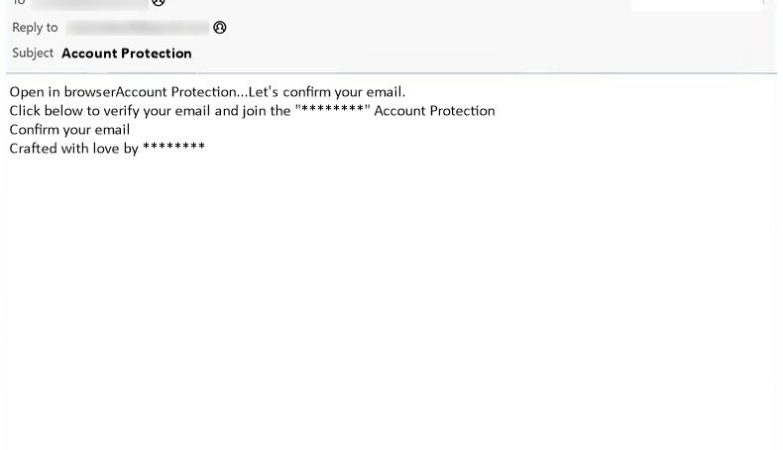
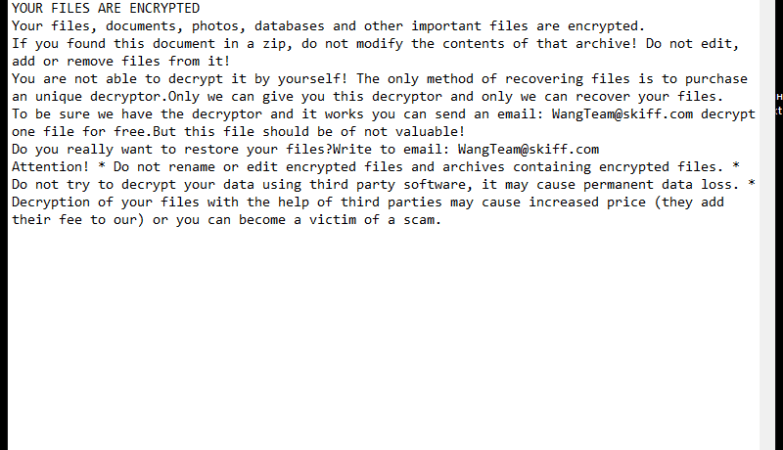
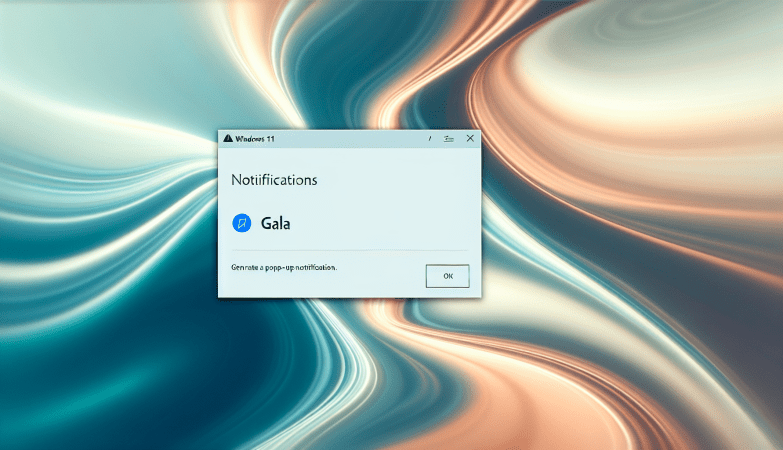
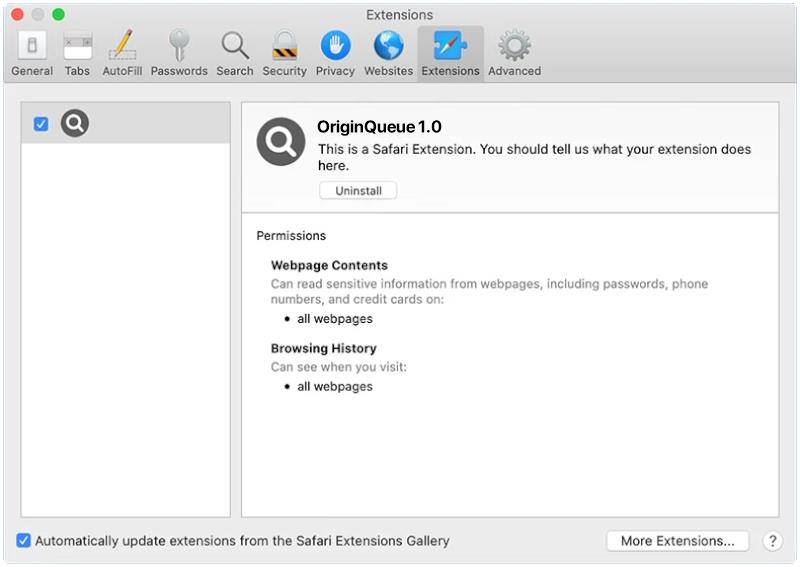
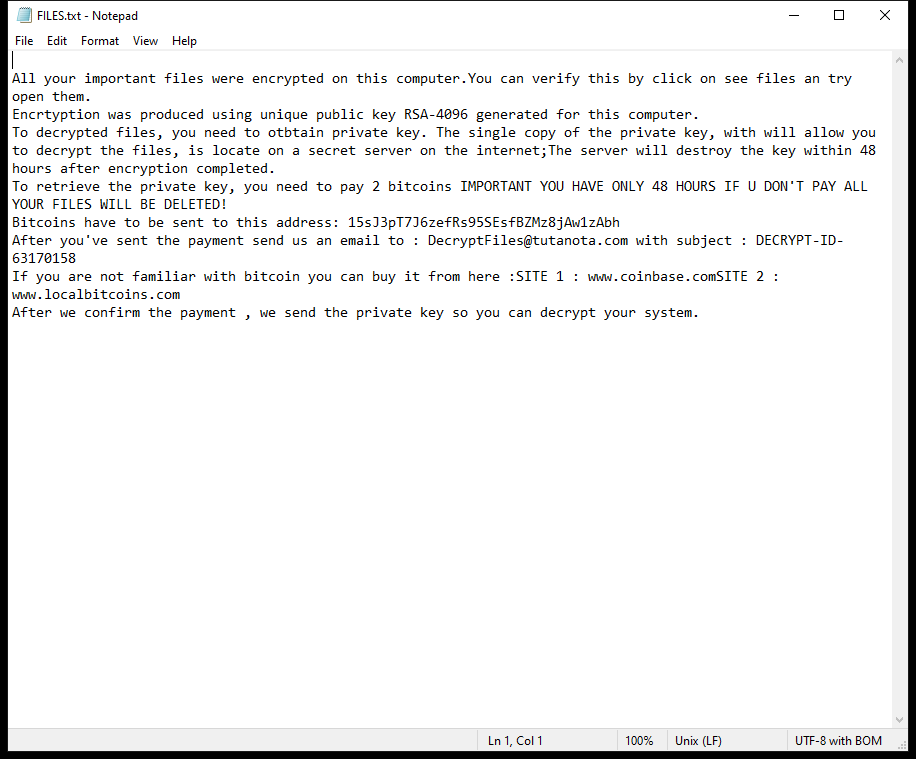
Protect-data.tech is a malicious website that tricks users into allowing browser notifications, claiming that they need to do so to access content or download files. Once granted permission, the website starts bombarding users with unwanted notifications, often containing malicious links or advertisements. This can lead to further infections or expose users to scams and phishing attacks.
Protect-data.tech typically infects computers through deceptive online tactics, such as fake software updates, malicious email attachments, or bundled with freeware downloads. It can exploit vulnerabilities in popular browsers such as Google Chrome, Mozilla Firefox, and Microsoft Edge to display intrusive notifications. It is not limited to a specific device or operating system, as it can infect Windows, Mac, Android, and iOS devices, making it a widespread threat to internet users across various platforms. Users should be cautious when encountering websites like Protect-data.tech and avoid granting unnecessary permissions to prevent their devices from being compromised.