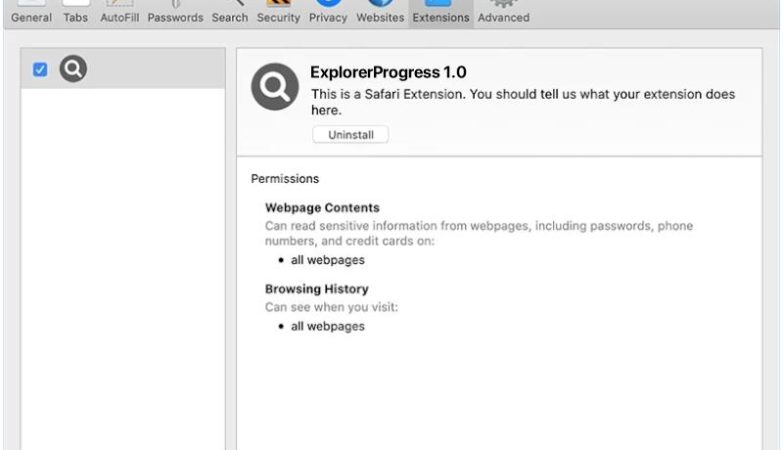
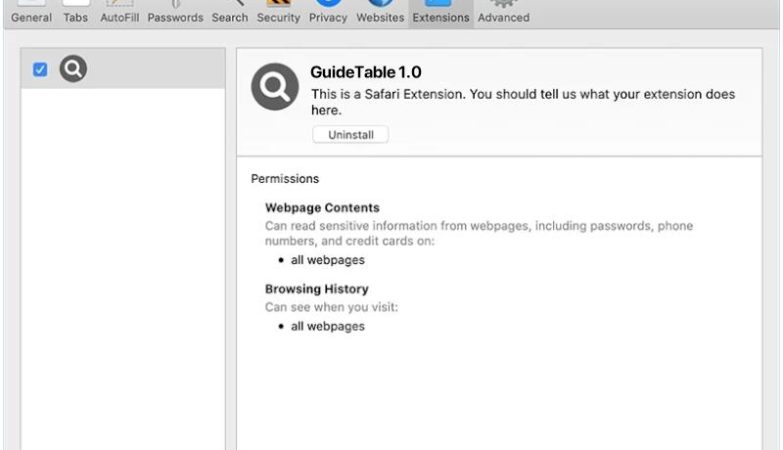
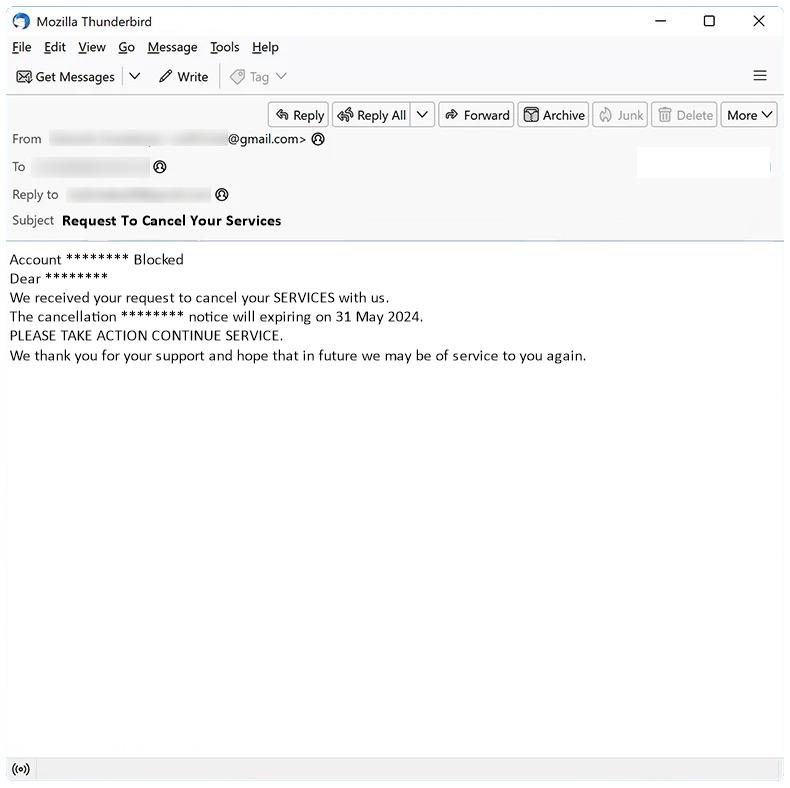
Request To Cancel Your Services email spam is a type of phishing scam where cybercriminals send emails pretending to be from a legitimate company or service provider, requesting the recipient to cancel their services. The email typically contains a link or attachment that, when clicked or opened, can infect the recipient’s computer with malware or lead to a phishing website designed to steal personal information.
Interacting with Request To Cancel Your Services email scam can pose several risks, including:
1. Malware infection: Clicking on links or opening attachments in the email can lead to the installation of malware on your computer, which can steal sensitive information, disrupt your system, or give cybercriminals unauthorized access.
2. Phishing: Visiting a phishing website through the email can result in the theft of personal information, such as login credentials, credit card details, or other sensitive data.
3. Financial loss: Some Request To Cancel Your Services scams may trick recipients into providing payment information or making unauthorized transactions, leading to financial loss.
To protect yourself from Request To Cancel Your Services email spam, it is important to be cautious and follow these tips:
1. Do not click on links or open attachments in unsolicited emails, especially if they are requesting sensitive information or seem suspicious.
2. Verify the legitimacy of the email by contacting the supposed sender through their official website or customer service number.
3. Use up-to-date antivirus software and spam filters to help detect and block malicious emails.
4. Report any suspicious emails to your email provider or relevant authorities to help prevent others from falling victim to the scam.
Read more