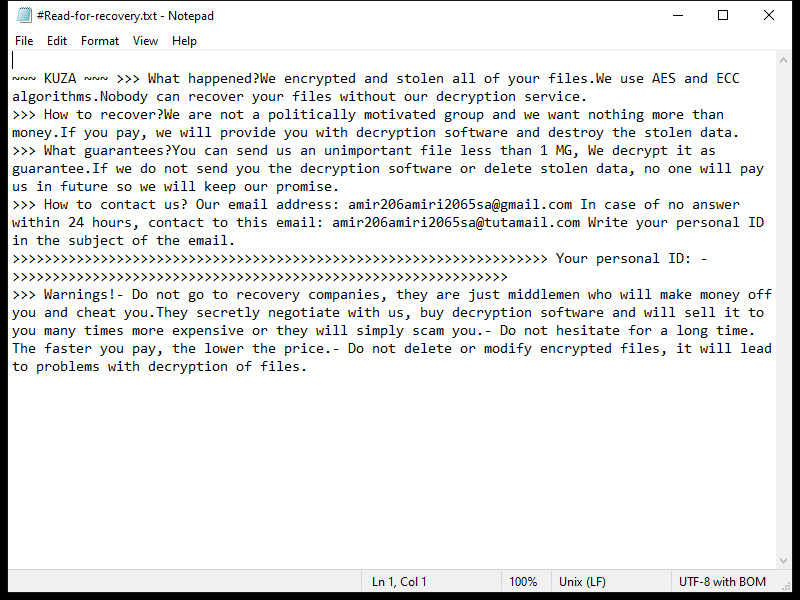
Renzo ($REZ) Token Allocation refers to the distribution of the total supply of Renzo tokens among various stakeholders such as investors, team members, advisors, and the community. This allocation is usually outlined in the project’s whitepaper or official documentation, detailing how many tokens will be allocated to each party and under what conditions they can be accessed or traded.
When Renzo Token Allocation appears in browsers, it is likely that users are searching for information about the project’s token distribution and allocation strategy. This information can help investors and users understand how tokens are being distributed and how it may impact the overall value and utility of the token. By having transparency around token allocation, projects can build trust and credibility with their community and stakeholders.