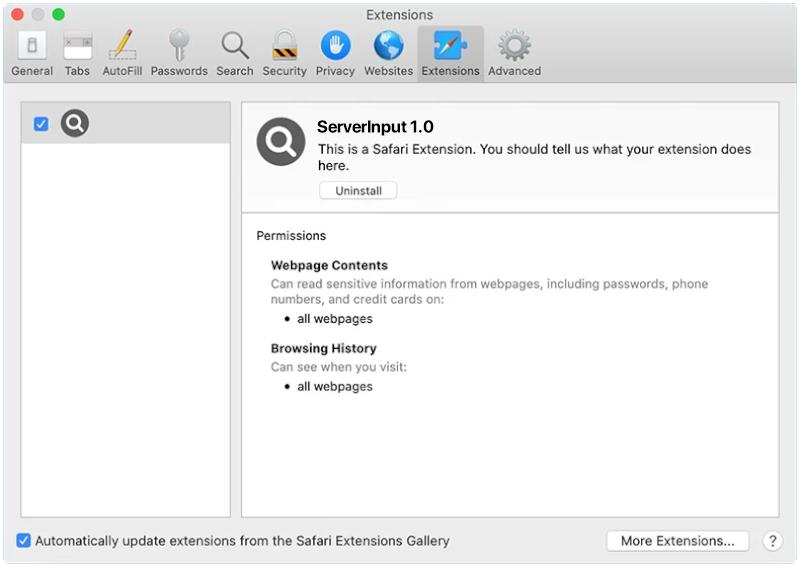
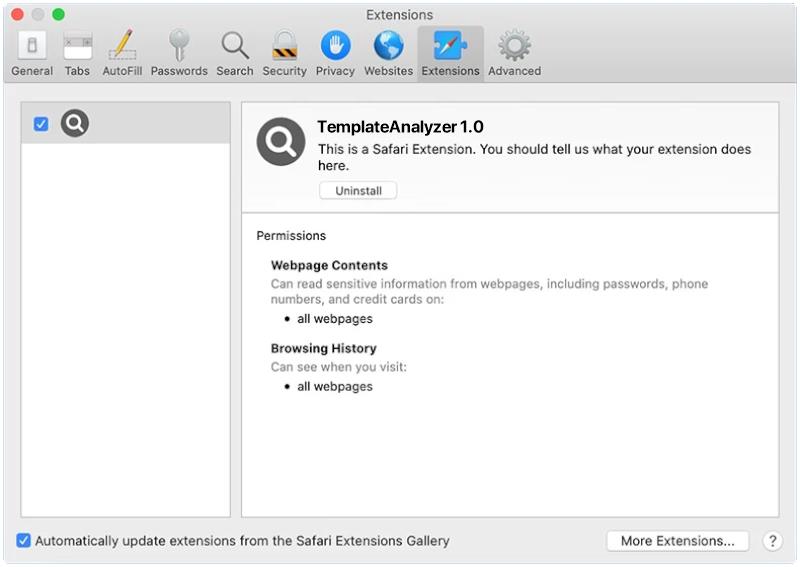
ServerInput is a type of malware that specifically targets Mac computers. It is a malicious program that is designed to infect a Mac system and steal sensitive information such as login credentials, personal data, and financial information. ServerInput can also give cybercriminals remote access to the infected Mac, allowing them to control the system and carry out various malicious activities.
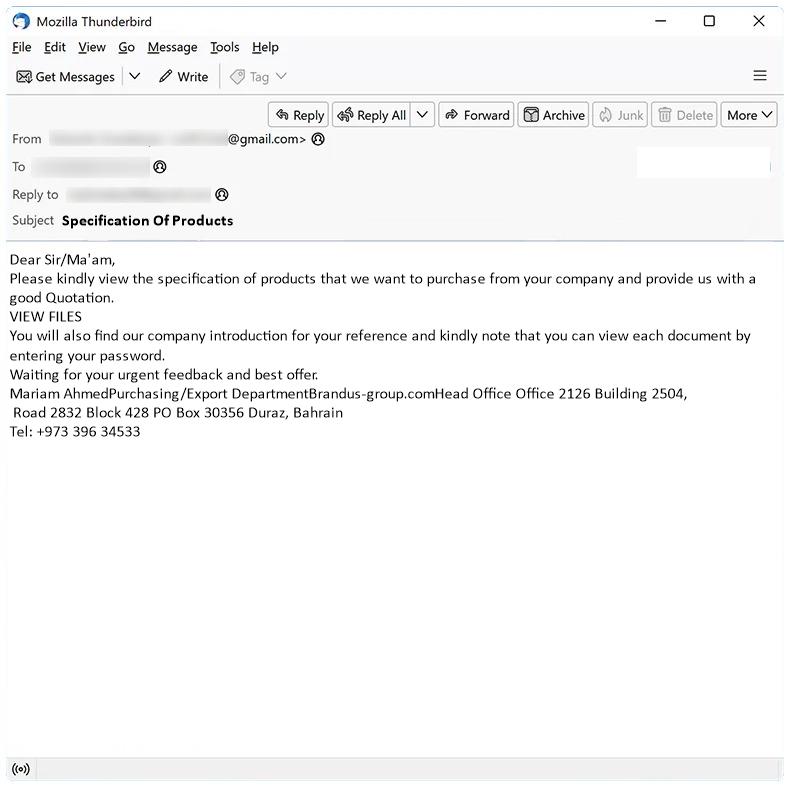
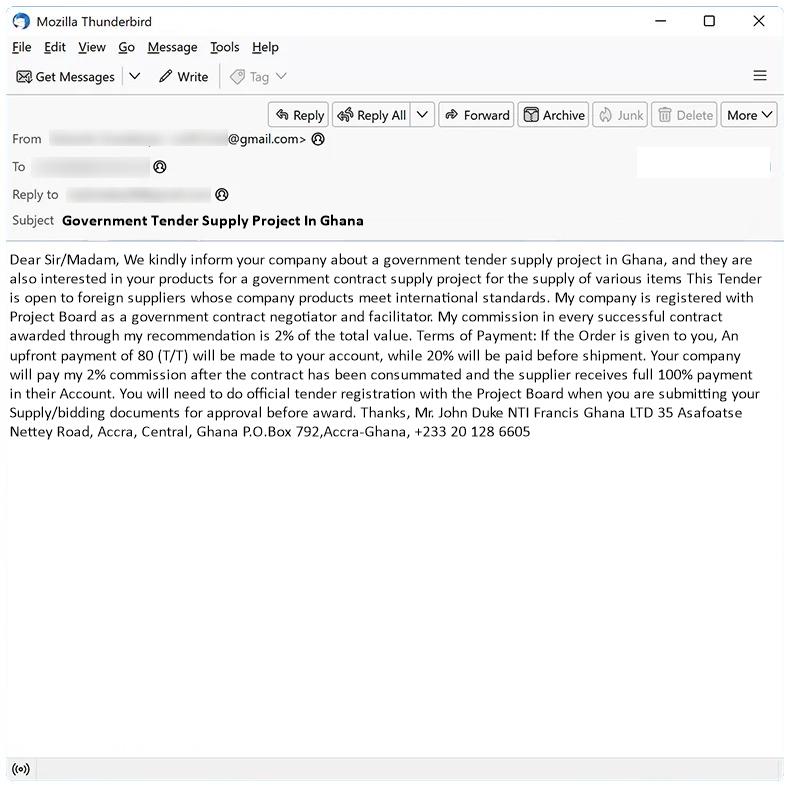
ServerInput typically infects Mac computers through phishing emails, malicious websites, or fake software downloads. Once the malware is installed on a Mac system, it can spread to other devices on the same network and compromise the security of the entire network. ServerInput is a dangerous threat to Mac users as it can steal valuable information and compromise the privacy and security of the infected system. It is important for Mac users to be cautious when downloading software, clicking on links, and opening email attachments to prevent ServerInput and other malware from infecting their systems.