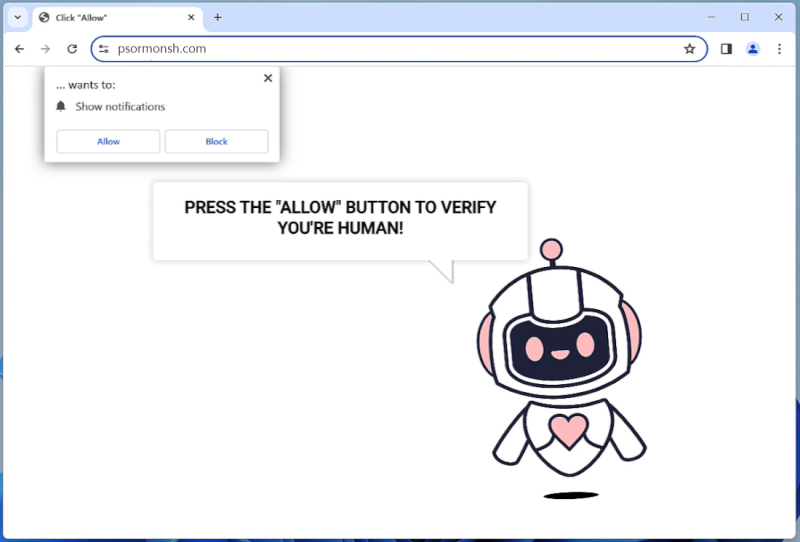
Random Year Fact is a type of adware that displays unwanted advertisements and pop-ups on a user’s computer or web browser. This adware typically infects computers through bundled software downloads, deceptive advertising, or malicious websites. Once installed, Random Year Fact can track a user’s browsing habits and display targeted advertisements based on this information.
Random Year Fact can also change browser settings, redirect users to unfamiliar websites, and slow down the performance of the infected computer. This adware can be difficult to remove, as it may hide in different system files and folders. Users are advised to regularly scan their computers with reputable antivirus software to detect and remove Random Year Fact and other potentially harmful programs.