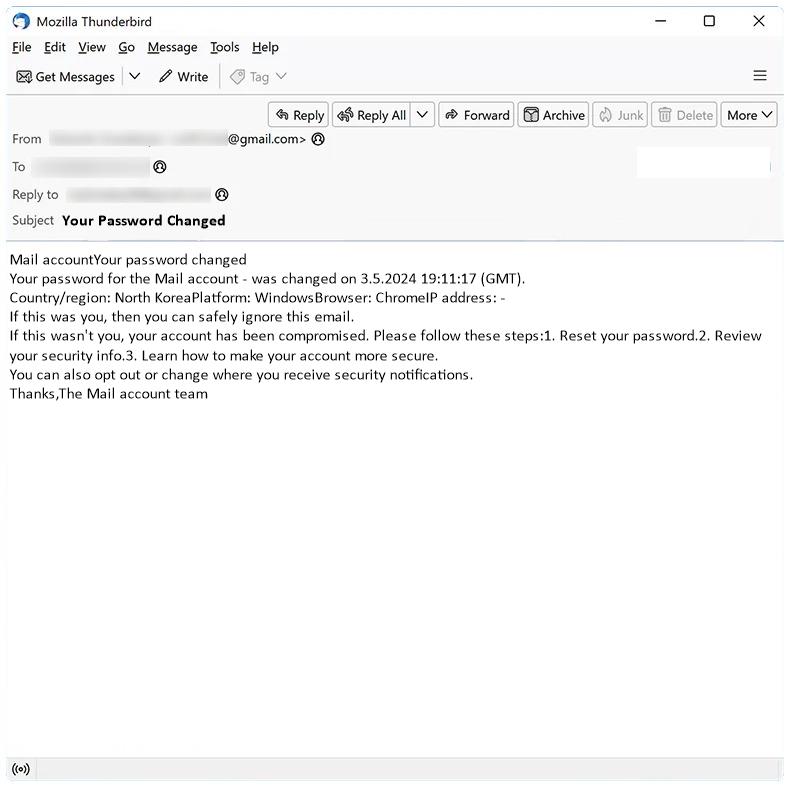
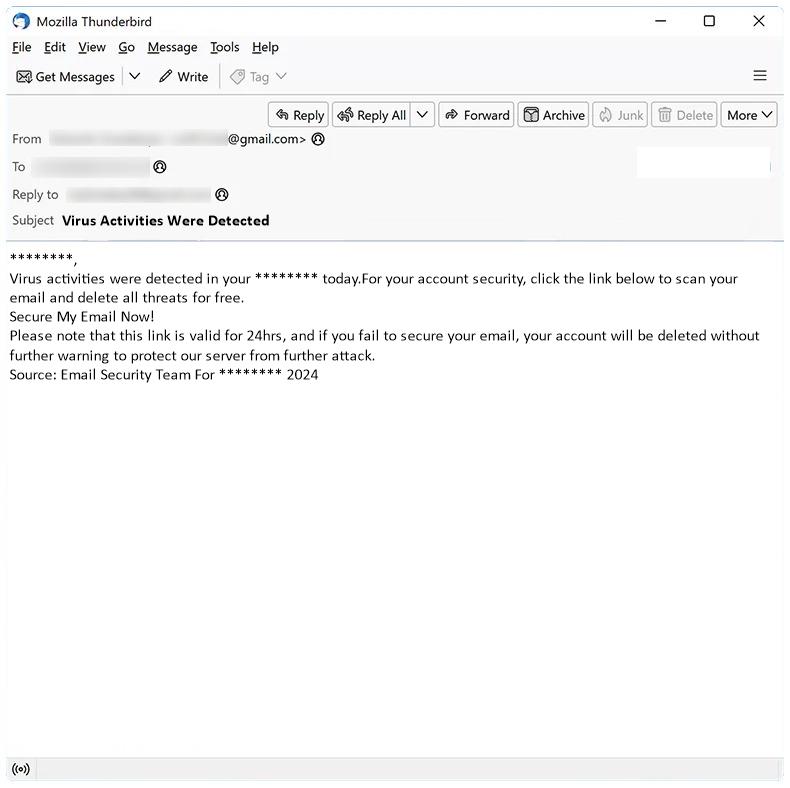
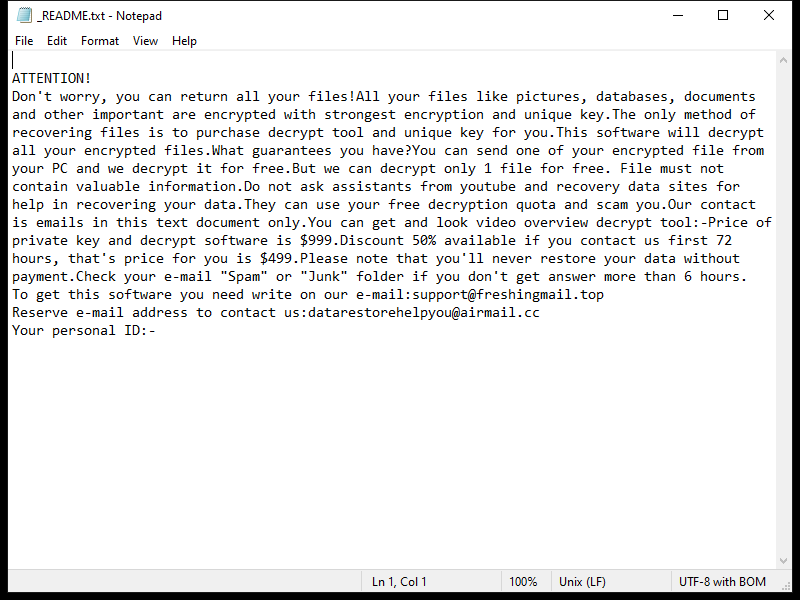
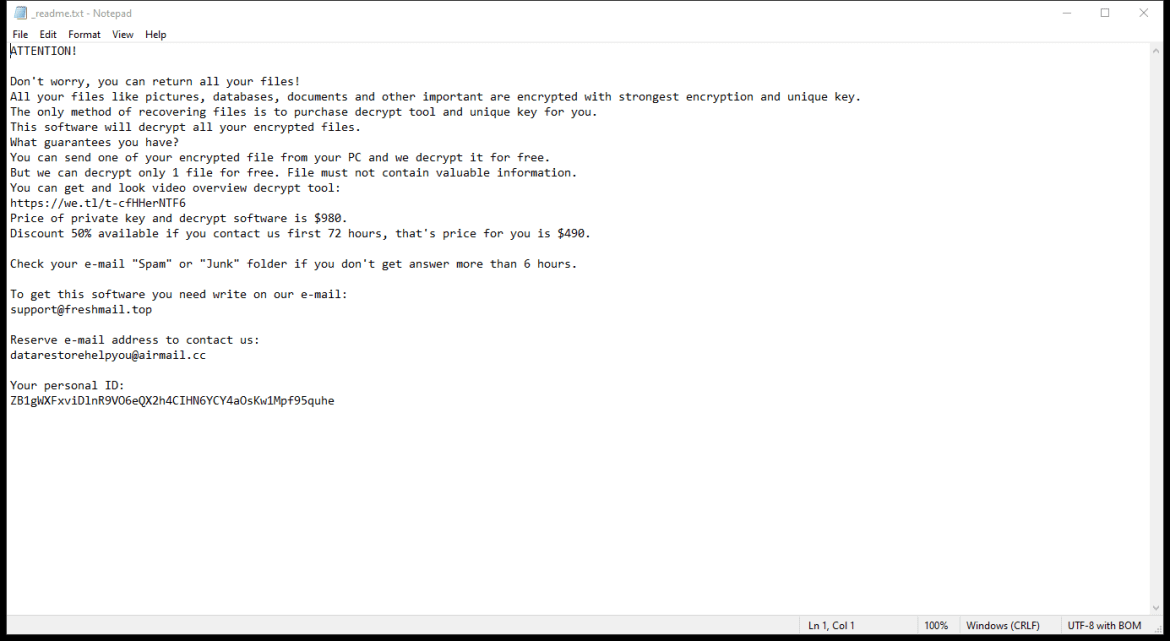
Your Password Changed email spam is a type of phishing scam where cybercriminals send out fake emails claiming that the recipient’s password has been changed. The email typically includes a link or attachment that, when clicked on or opened, can infect the recipient’s computer with malware or ransomware.
These spam campaigns can infect computers through various methods, such as malicious attachments, links to fake websites that mimic legitimate login pages, or by tricking users into providing their login credentials.
Interacting with Your Password Changed email scams can pose several risks, including:
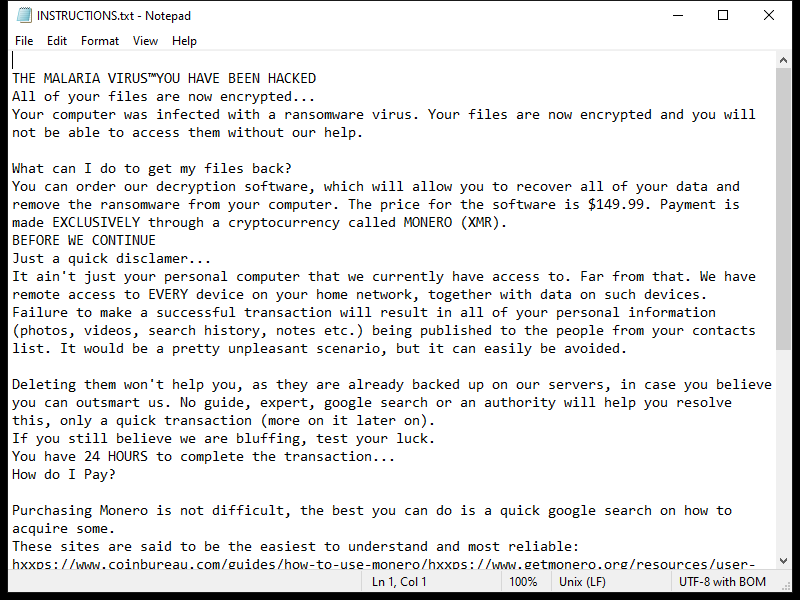
1. Malware infection: Clicking on links or opening attachments in these emails can lead to malware being installed on your computer, which can steal sensitive information or cause damage to your system.
2. Phishing attacks: Cybercriminals may use these emails to trick users into providing their login credentials, which can then be used to access sensitive accounts and steal personal information.
3. Financial loss: If cybercriminals gain access to your accounts through these scams, they may be able to carry out fraudulent transactions or steal money from your accounts.
To protect yourself from Your Password Changed email scams, it is important to be cautious when receiving unsolicited emails and to never click on links or open attachments from unknown or suspicious senders. Make sure to verify the legitimacy of any emails before taking any action, and consider enabling two-factor authentication on your accounts for added security.