Dx31 Ransomware is a type of malware that encrypts files on a computer system and demands a ransom payment from the victim for their release. Here is some information about Dx31 Ransomware:
1. Infection: Dx31 Ransomware typically infects computers through various methods like malicious email attachments, software vulnerabilities, fake software updates, or by exploiting remote desktop services.
2. File Extensions: After infecting a computer, Dx31 Ransomware adds a unique extension to the encrypted files. Unfortunately, the specific extension used by Dx31 Ransomware is not mentioned in the provided information.
3. File Encryption: Dx31 Ransomware uses a strong encryption algorithm to encrypt the victim’s files, making them inaccessible without the decryption key. The exact encryption algorithm used by Dx31 Ransomware is not mentioned.
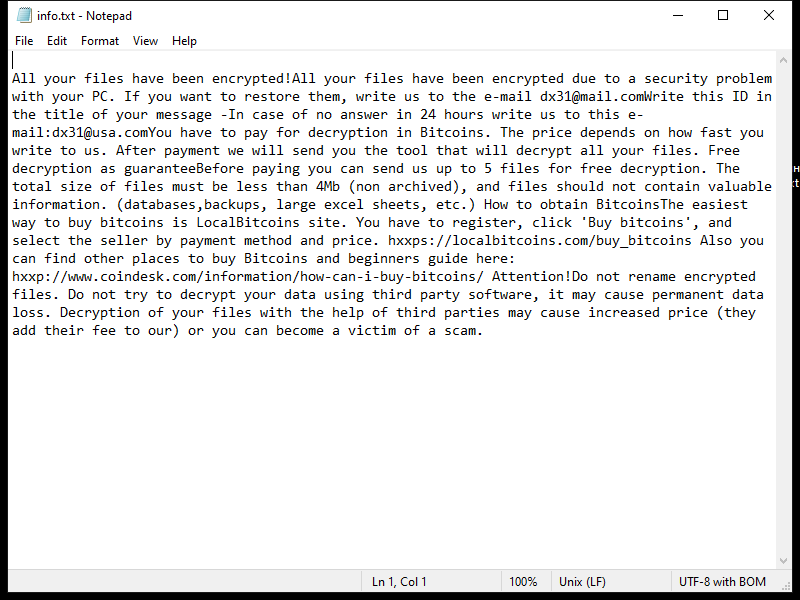
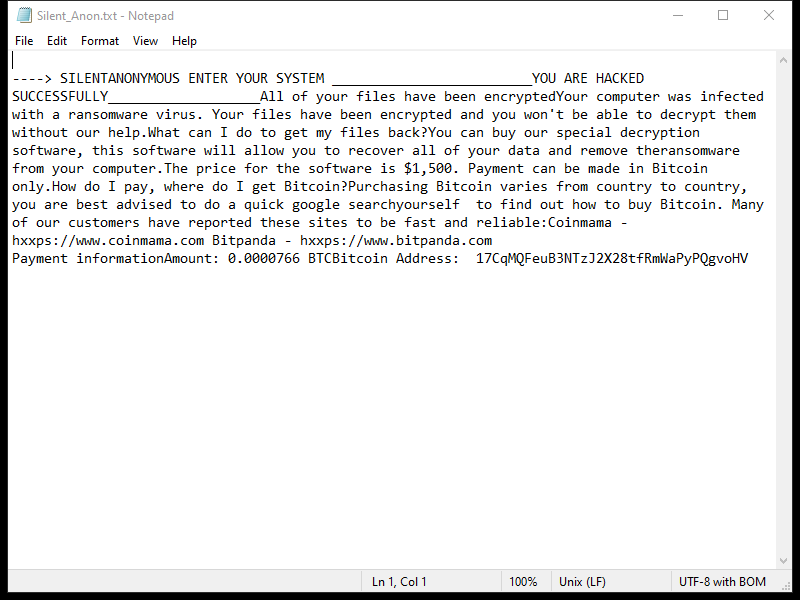
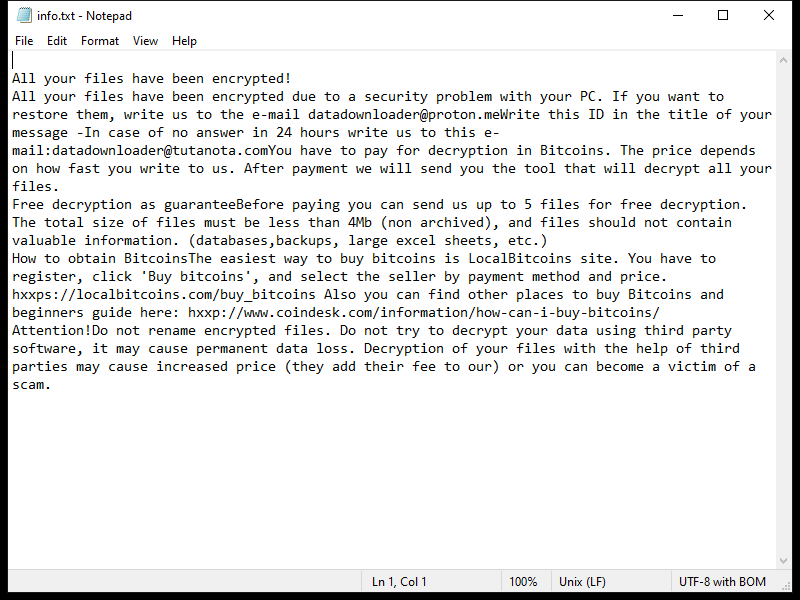
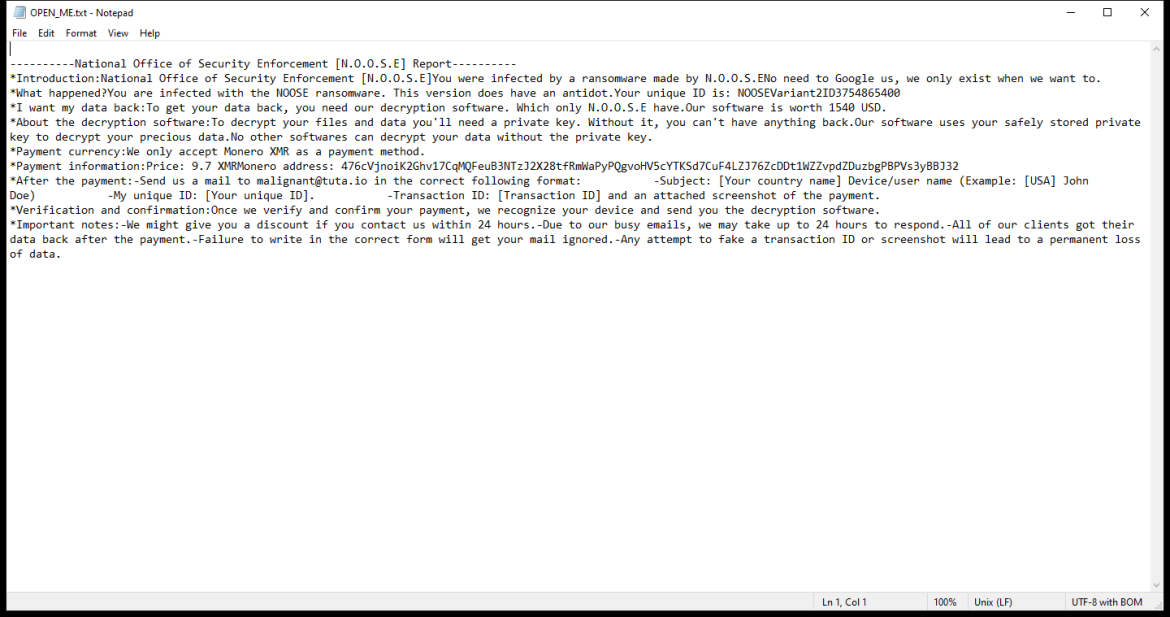
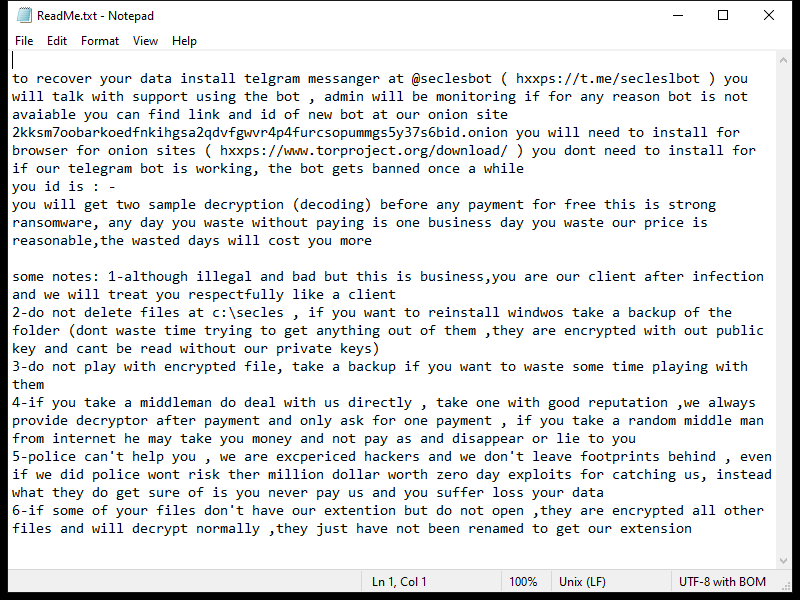
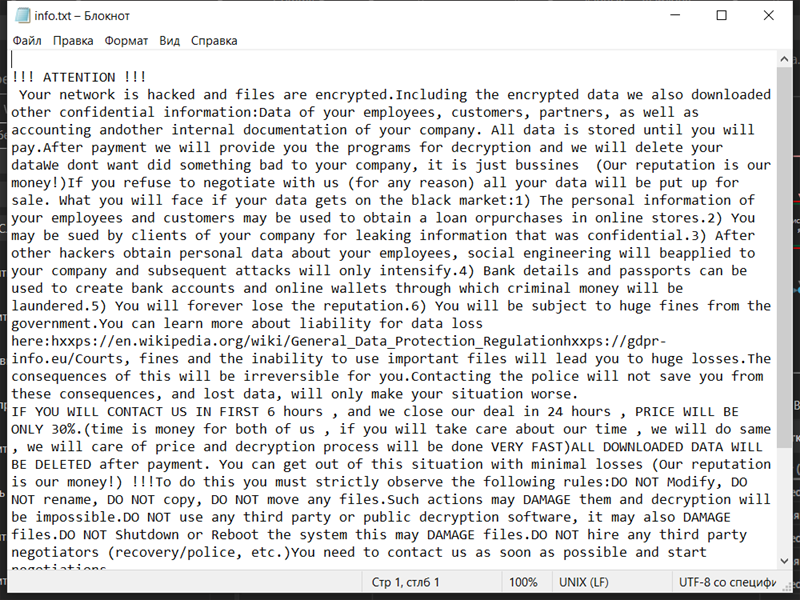
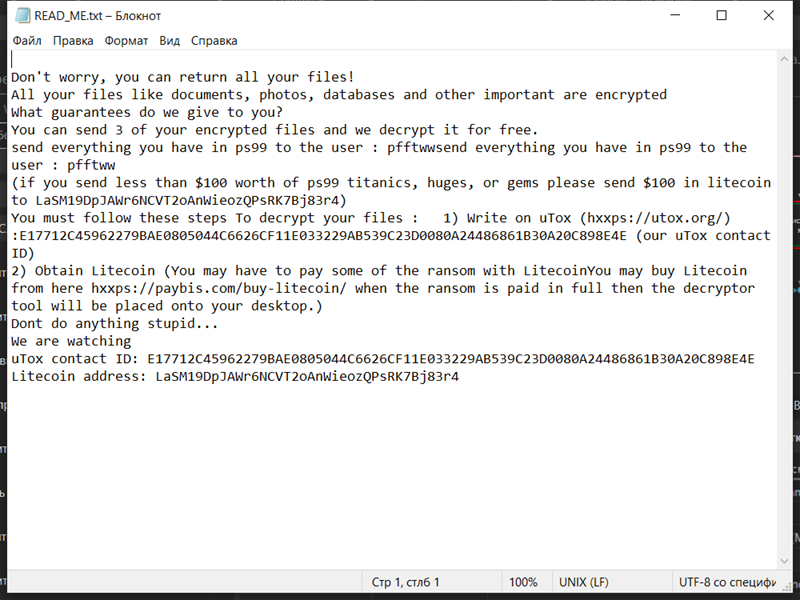
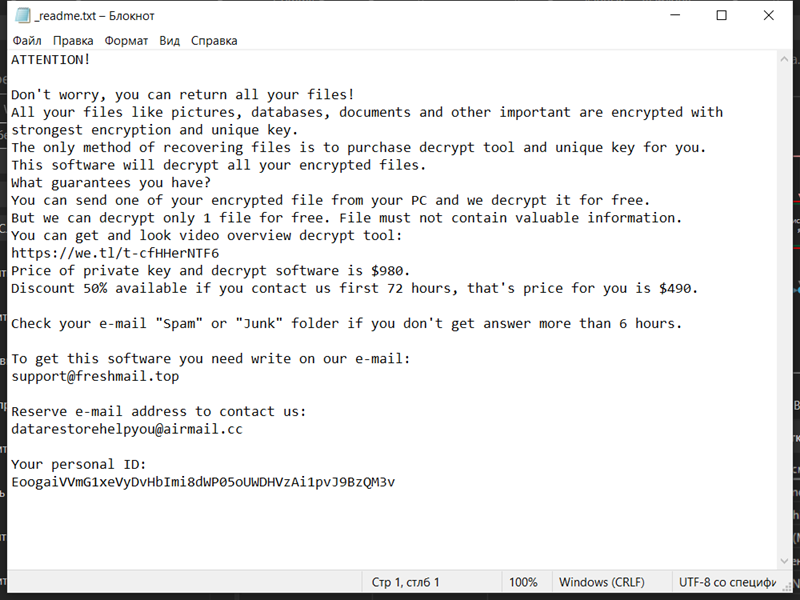
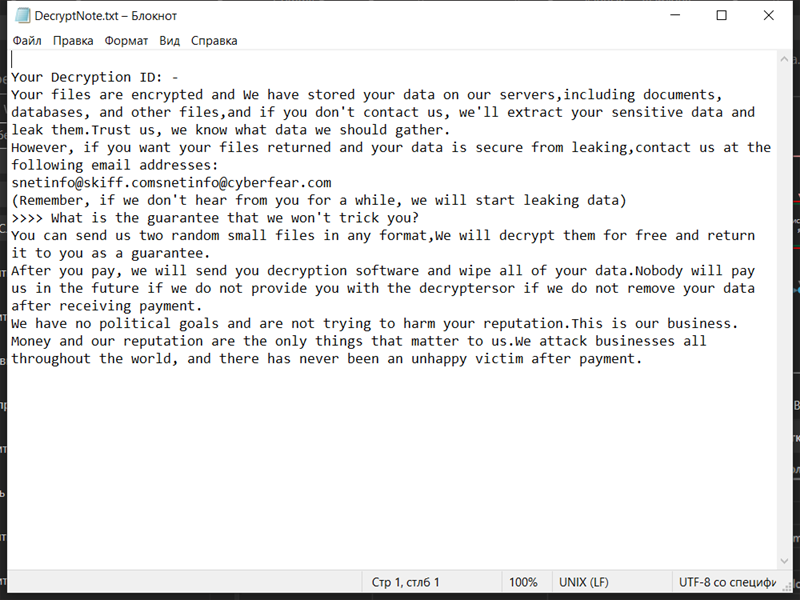
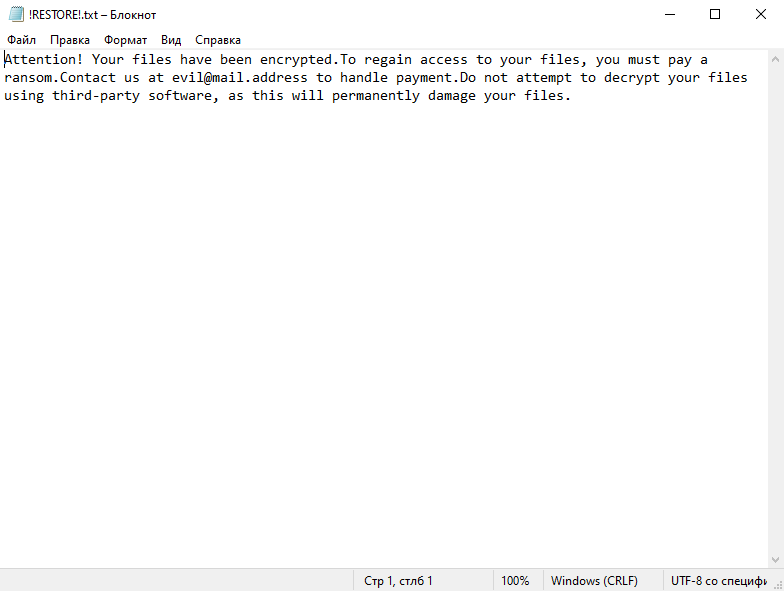
4. Ransom Note: Dx31 Ransomware creates a ransom note that informs the victim about the encryption and provides instructions on how to pay the ransom. The location and name of the ransom note are not specified in the given information.
5. Decryption Tools: As of now, there are no known decryption tools available for Dx31 Ransomware. However, it is advisable to regularly check reputable cybersecurity websites or contact professional cybersecurity firms for any updates on decryption tools.
6. Decrypting .dx31 Files: Without knowing the specific details of Dx31 Ransomware, it is difficult to provide a precise decryption method. In general, the best course of action is to restore your files from a backup if you have one. It is important to ensure that the backup is not connected to the infected system during the recovery process to prevent reinfection. Another option is to consult with a professional cybersecurity firm to explore any possible solutions or developments in decrypting .dx31 files.
Please note that the provided information is a general overview and may not cover all the intricacies of Dx31 Ransomware. It is essential to stay updated on the latest developments and seek professional assistance when dealing with ransomware attacks.