What is Muslat ransomware
Muslat is a new encoder, that will use strong encrypting algorithms to encipher user’s data. Any typical files are in danger – photos, audios, videos, documents and so on. Encrypted data is not available anymore, to be able to use those files again a user have to pay big sum of money ransom to cyber criminals – 980$ in BitCoins. If you are a victim of Muslat ransomware, let us warn you – nobody can guarantee that cyber crooks would decrypt your files after the payment is done. Use this guide to remove Muslat ransomware and decrypt .muslat files.

Muslat ransomware may easily encrypt thousands of files in a few minutes, the only difficult part is to infiltrate victim’s PC. It will use any vulnerabilities of a system to crawl in it. Once the virus is in victim’s computer, it will immediately start the enciphering process. Muslat will mark encrypted files with .muslat extension. Then it will drop ransom note to dictate the terms of decryption. Ransom notes are _readme.txt and readme.txt. The content of ransom notes:
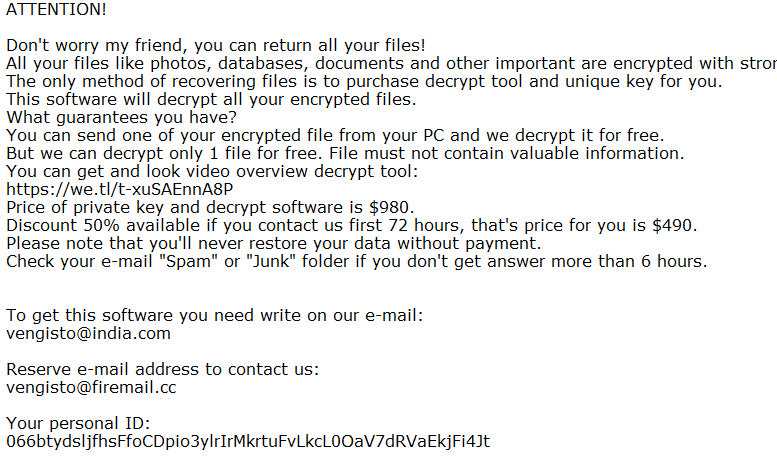
ATTENTION!
Don’t worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-mlQvroK6UO
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” folder if you don’t get answer more than 6 hours.
To get this software you need write on our e-mail:
vengisto@india.com
Reserve e-mail address to contact us:
vengisto@firemail.cc
Your personal ID:
033Vvbsh8HaaVTB4x1YEJ5Z***
There are two solutions of this problem. First is to use special Removal Tool. Removal Tools delete all instances of malware by few clicks and help user to save time. Or you can use Manual Removal Guide, but you should know that it might be very difficult to remove Muslat ransomware manually without specialist’s help.
Muslat Removal Guide
- Download Muslat Removal Tool.
- Remove Muslat from Windows (7, 8, 8.1, Vista, XP, 10) or Mac OS (Run system in Safe Mode).
- How to restore files
- How to protect PC from future infections.
How to remove Muslat ransomware automatically:
Thor Home may help you to get rid of this virus and clean up your system. In case you need a proper and reliable antivirus, we recommend you to try it.

Manual Muslat Removal Guide
Here is step-by-step instructions to remove Muslat from Windows and Mac computers. Follow this steps carefully and remove files and folders belonging to Muslat. First of all, you need to run system in a Safe Mode. Then find and remove needed files and folders.
Uninstall Muslat from Windows or Mac
Here you may find the list of confirmed related to the ransomware files and registry keys. You should delete them in order to remove virus, however it would be easier to do it with our automatic removal tool. The list:
x12.exe
Muslat.dll
_readme.txt
readme.txt
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Muslat by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Muslat by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Muslat by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Muslat by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple logo appears;
- Find programs or files potentially related to Muslat by using Removal Tool;
- Delete found files;
How to restore encrypted files
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
Stellar Data Recovery is able to find and restore different types of encrypted files, including removed emails.
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Restore encrypted files using Recuva
There is an alternative program, that may help you to recover files – Recuva.
- Run the Recuva;
- Follow instructions and wait until scan process ends;
- Find needed files, mark them and Press Recover button;
How to prevent ransomware infection?
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
Malwarebytes
SpyHunter is a reliable antimalware removal tool application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.


Please help me decrypt .muslat files.
Good day! You should try to see whether your files are able to be restored. We advise you to use recovery software to restore infected files. You may find the most efficient recovery software in this article – click here.